



Preview text:
VIETNAM NATIONAL UNIVERSITY, HANOI INTERNATIONAL SCHOOL
-------------------------------
REPORT OF STANDARDS AND CRITERIA INFORMA FOR ASSESSING TI ON SECURITY SYSTEMS
Subject: Principles of Information Security Class: INS306202
Member: Nguyễn Đức Huy - 20070728
Hoàng Mạn h Linh - 20070947
Phan Khánh Ly - 2 0070745
Phùng Thị Hồng Loan - 20070742 Hanoi 2/2023
1. Concepts .................................................................................................................................. 2
a. Information security: ............................................................................................................... 2
b. Security incident management: .............................................................................................. 3
2. Network security standards .................................................................................................... 3
a. Confidentiality ......................................................................................................................... 3
b. Integrity .................................................................................................................................. 3
c. Availability .............................................................................................................................. 4
d. Types of standard sets ............................................................................................................ 4
3. Criteria ................................................................................................................................... 5
4. Contribution ........................................................................................................................... 6 1
The standards and criteria for assessing the reliability of information
security products (IS - Information Security products) have been interested
by many countries around the world since very early. These can be products
and systems specialized in security and safety such as firewall systems,
intrusion detection systems (IDS - Intrusion Detection System), smart cards
(Smart Cards), applications, disk encryption, etc. or more familiar products
such as a dedicated computer system, database management system (DBMS
- Database Management System), operating system (OS - Operating System), server web (Web Server).
This report briefly introduces the process of forming some criteria used
to evaluate IS products in the world. In which will focus on the contents
related to a set of criteria and standards that are being developed and widely
used in the world called "Common Criteria for Assessment of Information
Technology Security" ( Common Criteria for Information Technology
Security Evaluation), this set of criteria is also known by the more familiar
name “Common Criteria” or “CC”.
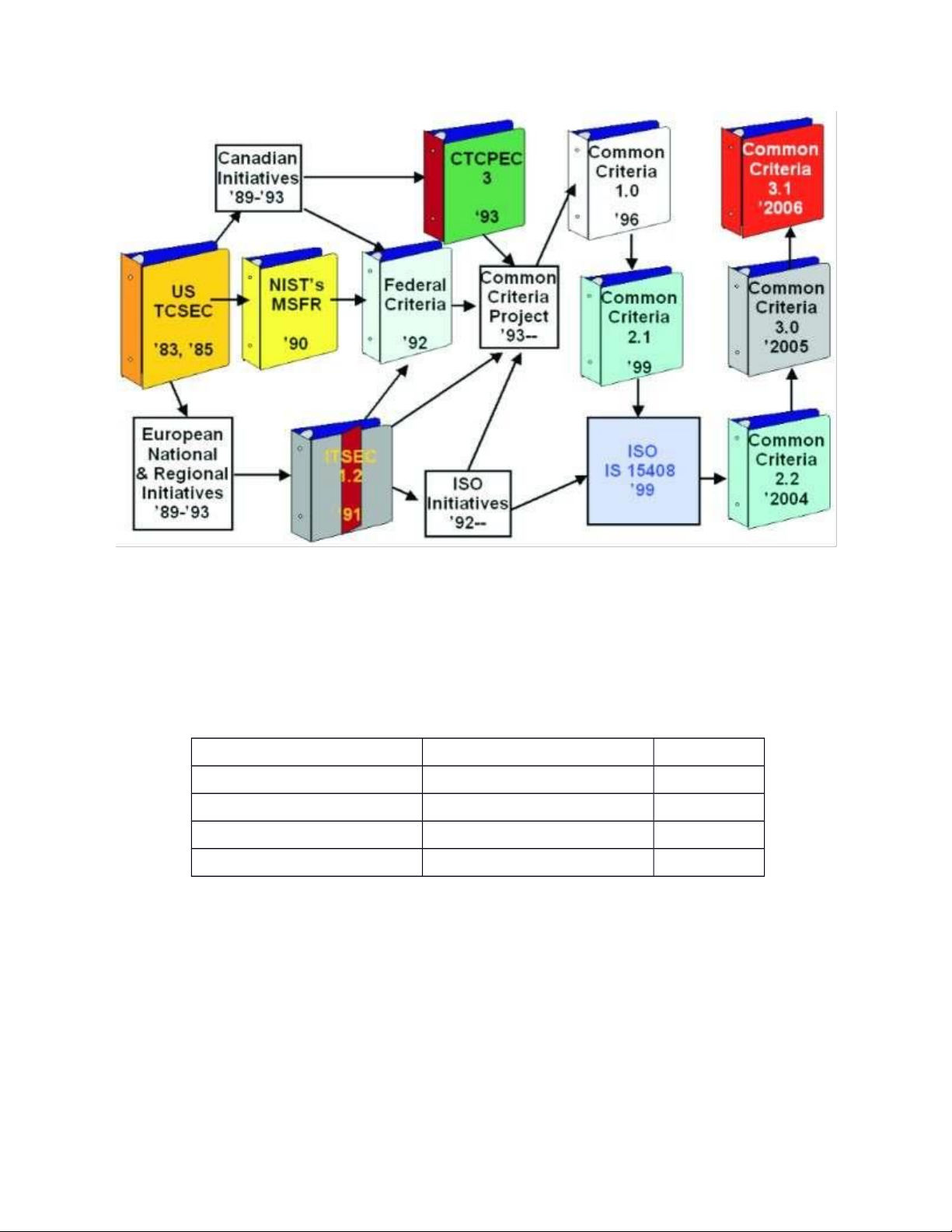
In 1996, the “Common Criteria” (CC) was released. The first version
(version 1.0) was based on the synthesis and refinement of the previous
criteria of the United States, Canada and Europe to overcome the concept of
and evaluation criteria for each country. In 1999, CC developed to version
2.1 and officially became the international standard ISO/IEC 15408:1999.
Then, in 2005, ISO continued to re-issue this set of standards to ISO/IEC 15408:2005. 1. Concepts a. Information security:
To ensure technical safety in the operation of the network and
information infrastructure, to prevent the possibility of taking advantage of
the network and information infrastructure to commit illegal acts, causing
harm to the community; ensure the properties: confidentiality, integrity,
accuracy, availability of information in storage, processing and transmission on the network. 2
b. Security incident management:
Used in the standard is not only information security incident
management, but also covers information security vulnerability
management. If the organization deploys the ISMS system, the good
management of information security incidents will contribute significantly
to an effective and effective ISMS.
2. Network security standards a. Confidentiality
Confidentiality is a requirement whose purpose is to keep sensitive
information from being disclosed to unauthorized recipients. The secrets
might be important for reasons of national security (nuclear weapons data),
law enforcement (the identities of undercover drug agents), competitive
advantage (manufacturing costs or bidding plans), or personal privacy (credit histories).
For instance, classify information as restricted, company confidential, and
unclassified (Schmitt, 1990). Even if an organization has no secrets of its
own, it may be obliged by law or common courtesy to preserve the privacy
of information about individuals. Medical records, for example, may require
more careful protection than do most proprietary information. A hospital
must thus select a suitable confidentiality policy to uphold its fiduciary
responsibility with respect to patient records. b. Integrity
Integrity is a requirement meant to ensure that information and programs
are changed only in a specified and authorized manner. It may be important
to keep data consistent (as in double-entry bookkeeping) or to allow data to
be changed only in an approved manner (as in withdrawals from a bank
account). It may also be necessary to specify the degree of the accuracy of data.
For example, any task involving the potential for fraud must be divided
into parts that are performed by separate people, an approach called
separation of duty. A classic example is a purchasing system, which has three
parts: ordering, receiving, and payment. Someone must sign off on each step, 3
the same person cannot sign off on two steps, and the records can be changed
only by fixed procedures—for example, an account is debited and a check
written only for the amount of an approved and received order. In this case,
although the policy is stated operationally—that is, in terms of specific
management controls—the threat model is explicitly disclosed as well. c. Availability
Availability is a requirement intended to ensure that systems work
promptly and service is not denied to authorize users. From an operational
standpoint, this requirement refers to adequate response time and/or
guaranteed bandwidth. From a security standpoint, it represents the ability to
protect against and recover from a damaging event. The availability of
properly functioning computer systems (e.g., for routing long-distance calls
or handling airline reservations) is essential to the operation of many large
enterprises and some for preserving lives (e.g., air traffic control or
automated medical systems). Contingency planning is concerned with
assessing risks and developing plans for averting or recovering from adverse
events that might render a system unavailable.
For example: an automatic teller machine or a reservation agent's
keyboard and screen) is up if it responds correctly within one second to a
standard request for service; otherwise it is down. This policy means that the
up time at each terminal, averaged over all the terminals, must be at least 99.98 percent.
d. Types of standard sets
- Network security standard set: ISO/IEC 27033.
- ISO/IEC 27035 set of standards for incident management of security incidents.
- ISMS standard set of information security management systems.
- Standard set of network safety: TCVN 9801-1:2013 (ISO/IEC
270331:2009) Information technology - Security engineering - Network security. 4 3. Criteria
According to CC, the assessment of IS products is based on 7 basic
safety levels called "Evaluation Assurance Level" - EAL (Evaluation Assurance Level). EAL Level Description EAL 1 Functionally tested EAL 2 Structurally tested EAL 3
Methodically tested and checked EAL 4
Methodically designed, tested and reviewed EAL 5
Semi-formally designed and tested EAL 6
Semi-formally verified design and tested EAL 7
Formally verified design and tested
In addition to the issuance of the Common Criteria, a set of documents
guiding the evaluation of IS products against the Common Criteria is called
the “Common Methodology for Evaluation of IT Security Products” (CEM).
Information Technology Security Evaluation) has also been developed and
released corresponding to each version. In 2005, the ISO organization also
issued CEM into the international standard ISO/IEC 18045:2005. 5
CEM is a "methodological" document, so its content specifically
presents methods for an Evaluator to do the IS product evaluation steps in accordance with CC. 4. Contribution Name Assignments Mark Nguyễn Đức Huy Presented 6.75 Hoàng Mạnh Linh Presented 6.75
Phan Khánh Ly Powerpoint + Report 6.75 Phùng Thị
Hồng Loan Find information 6.75 6