Preview text:
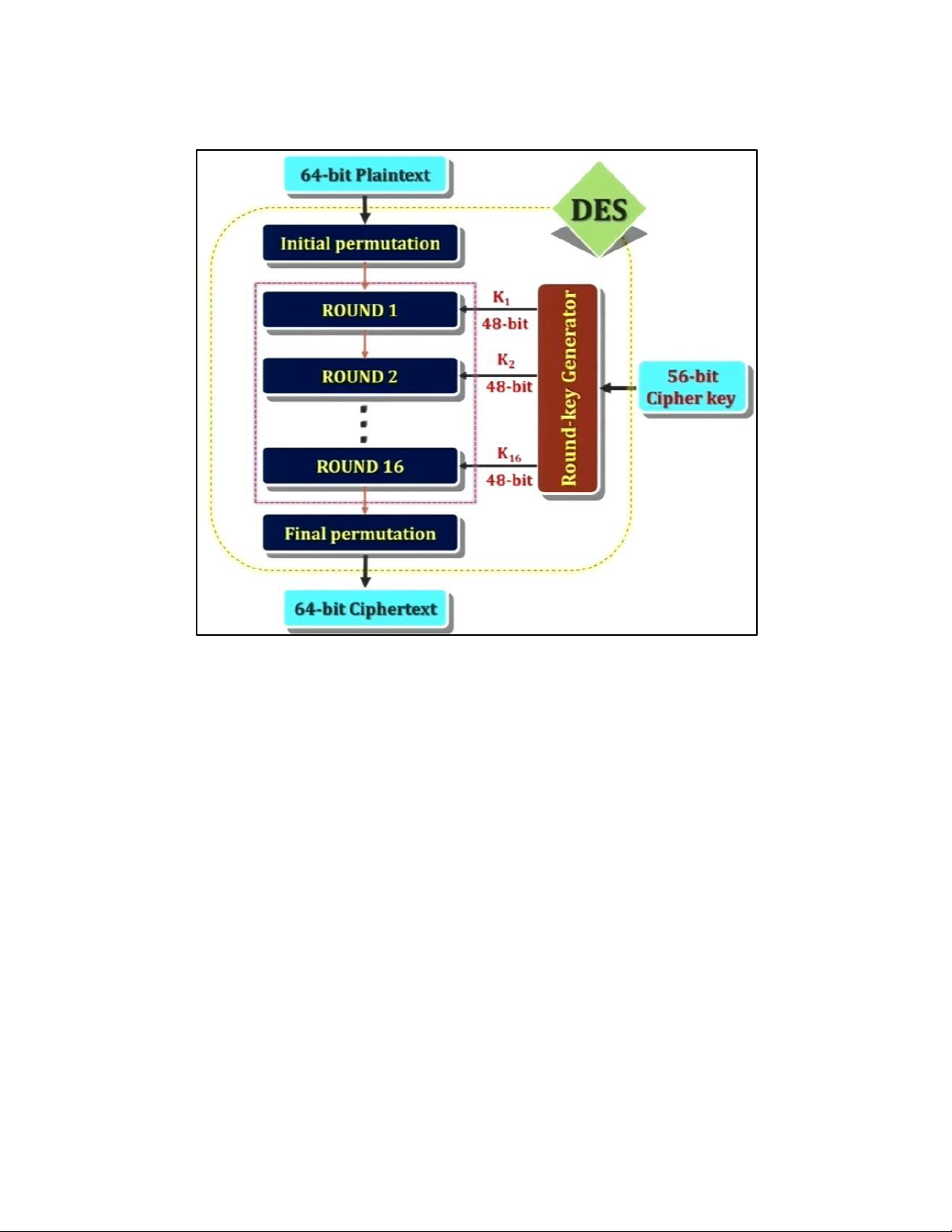
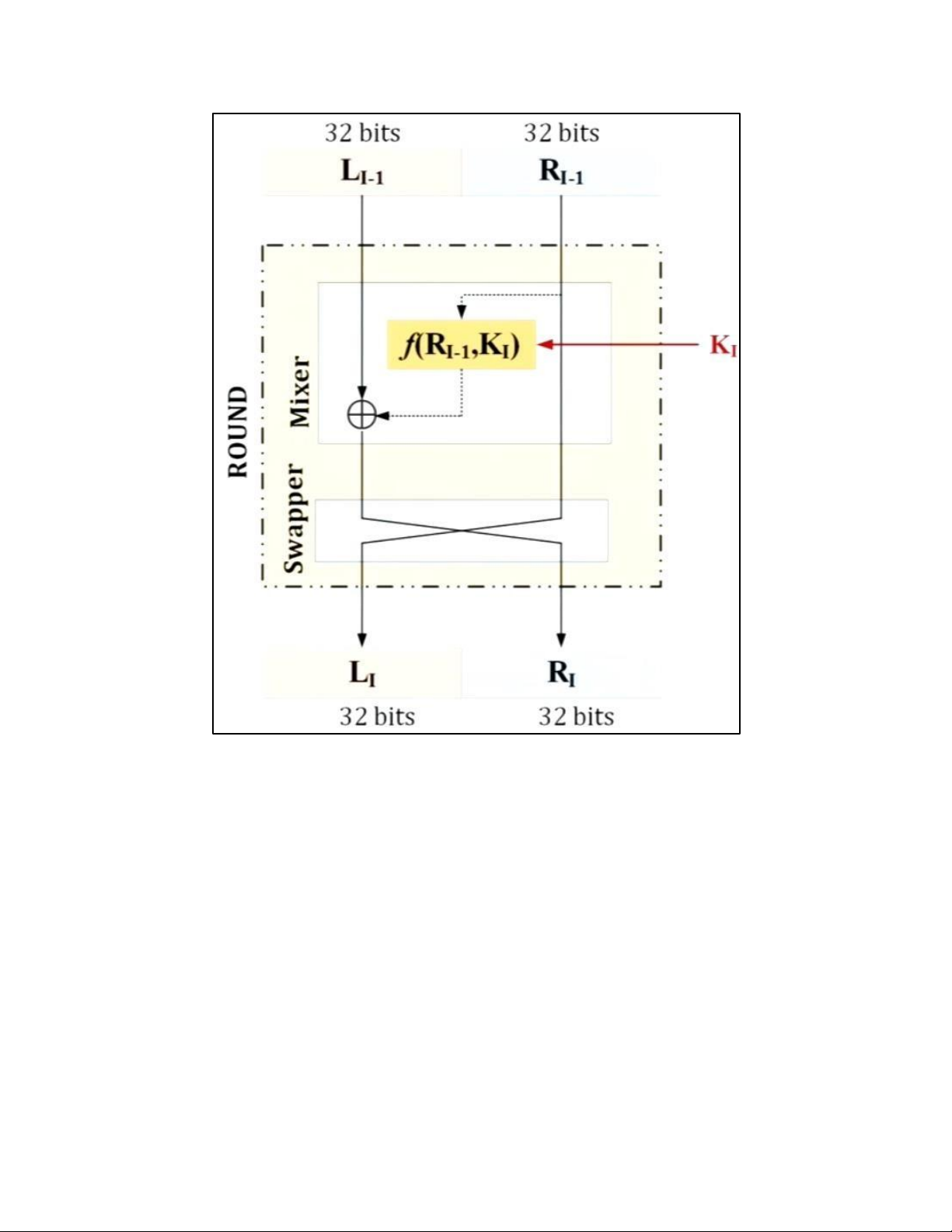
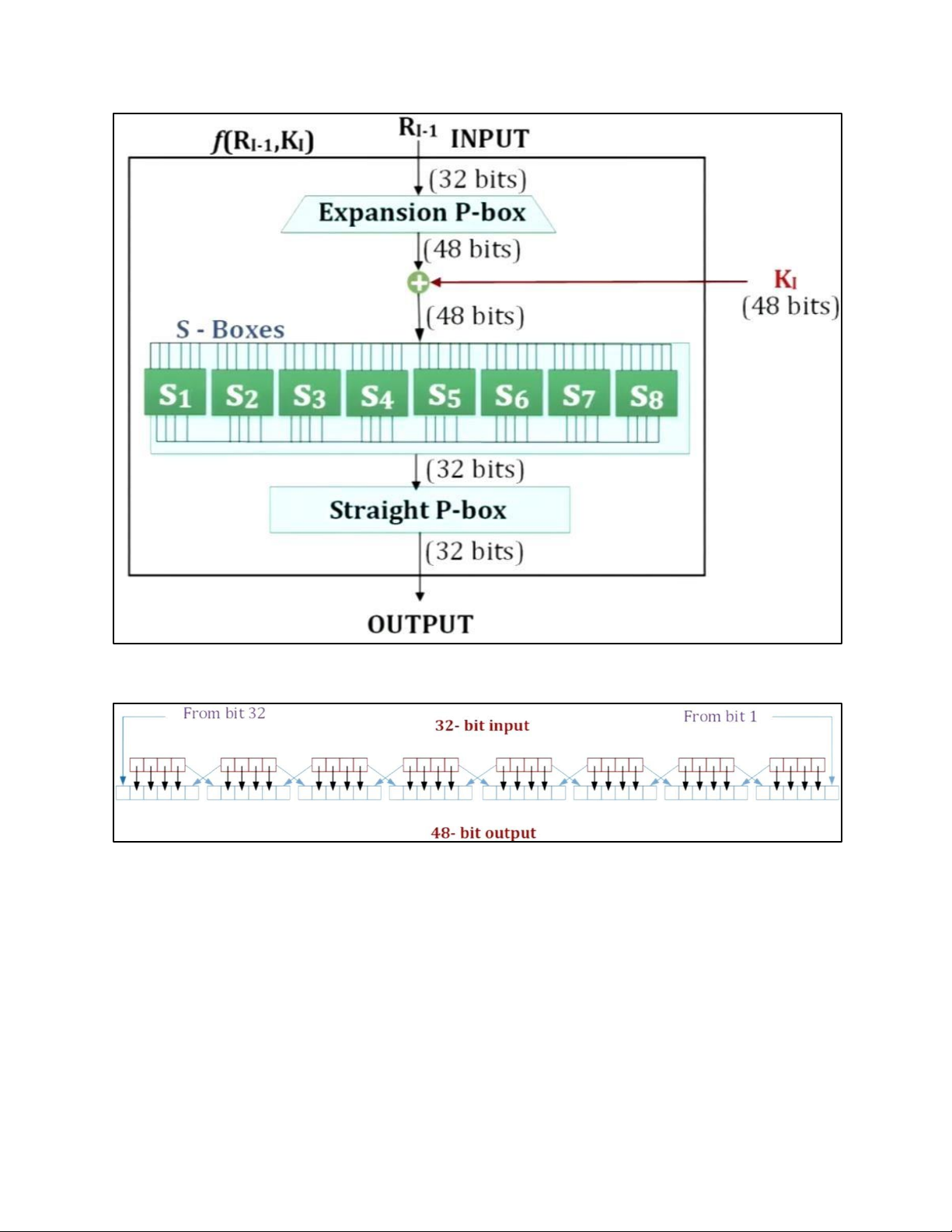
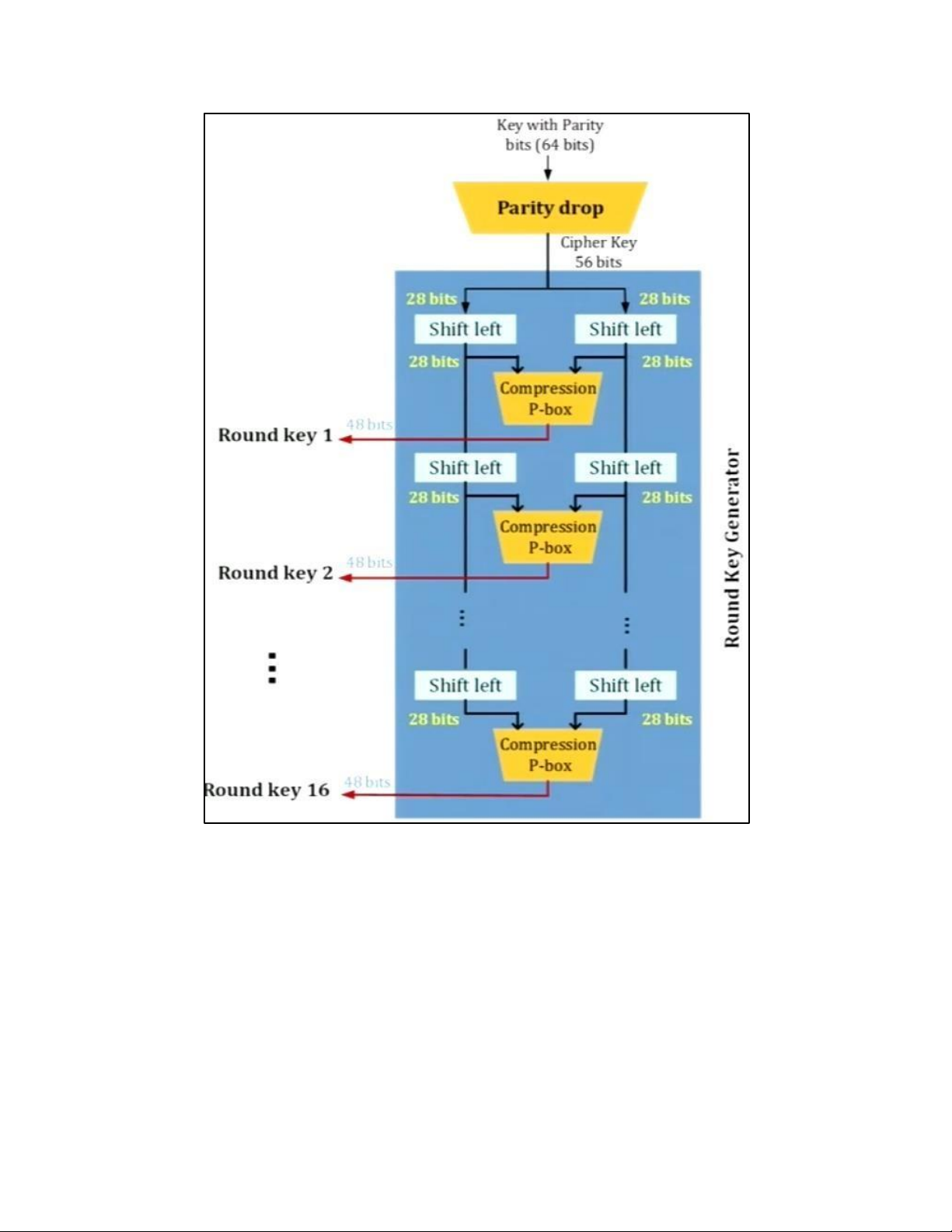
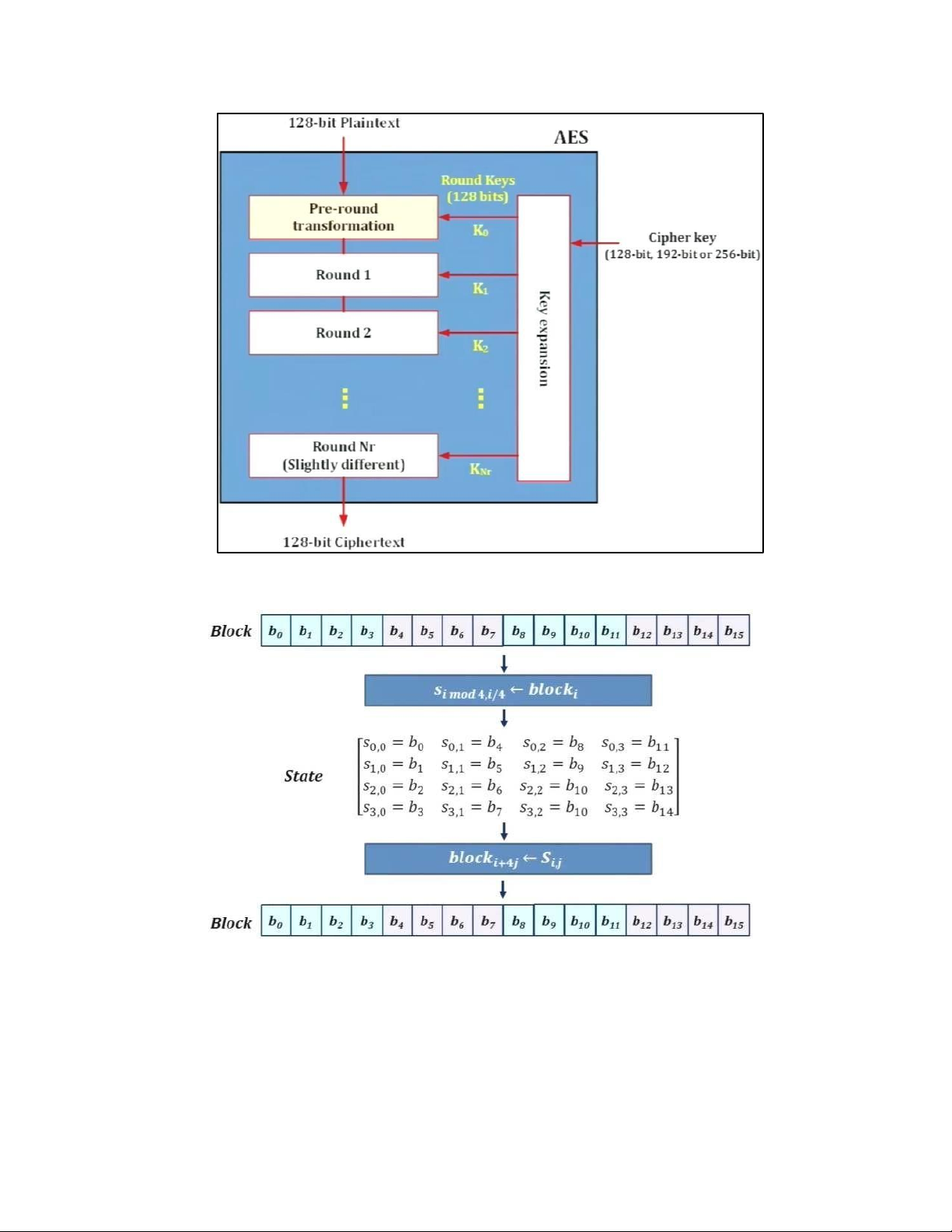
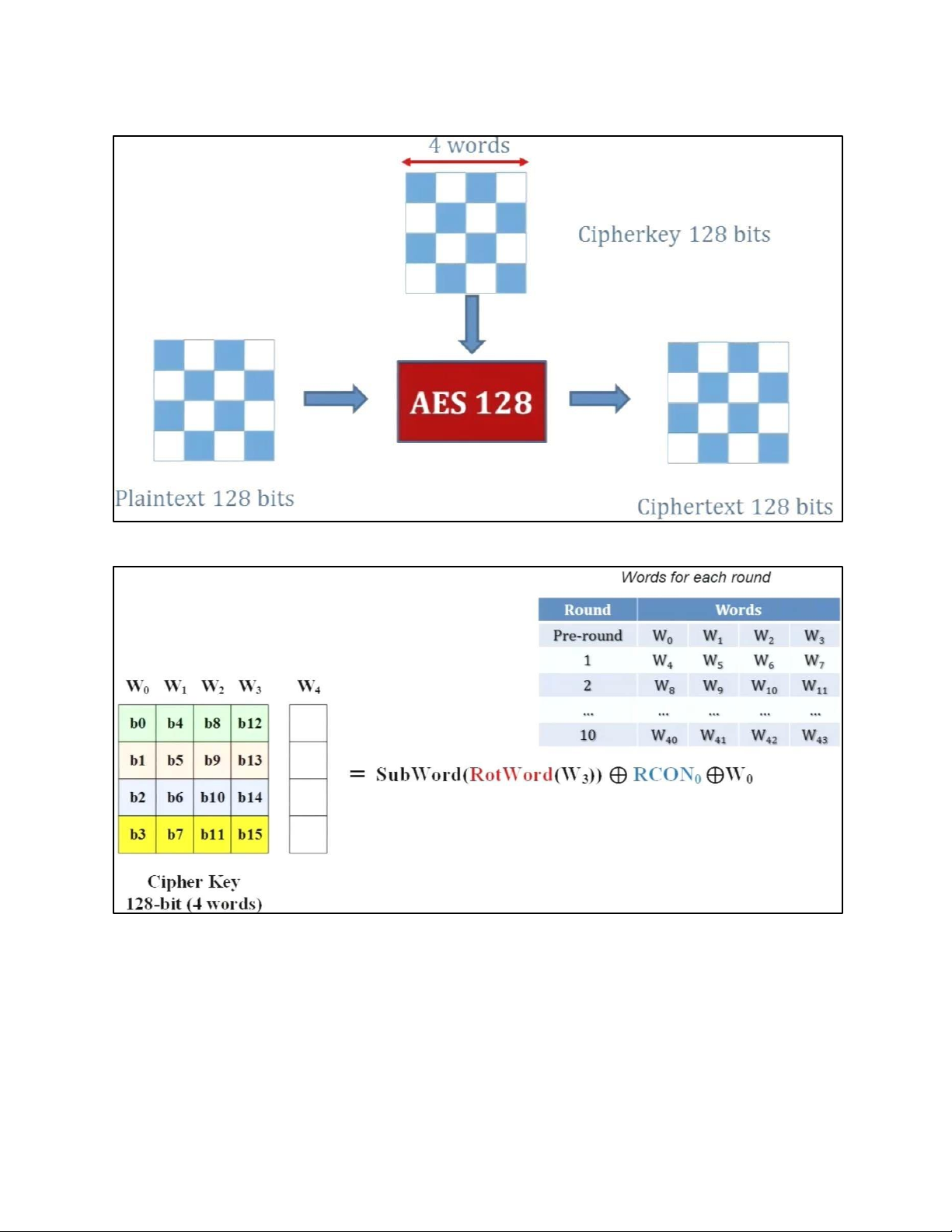
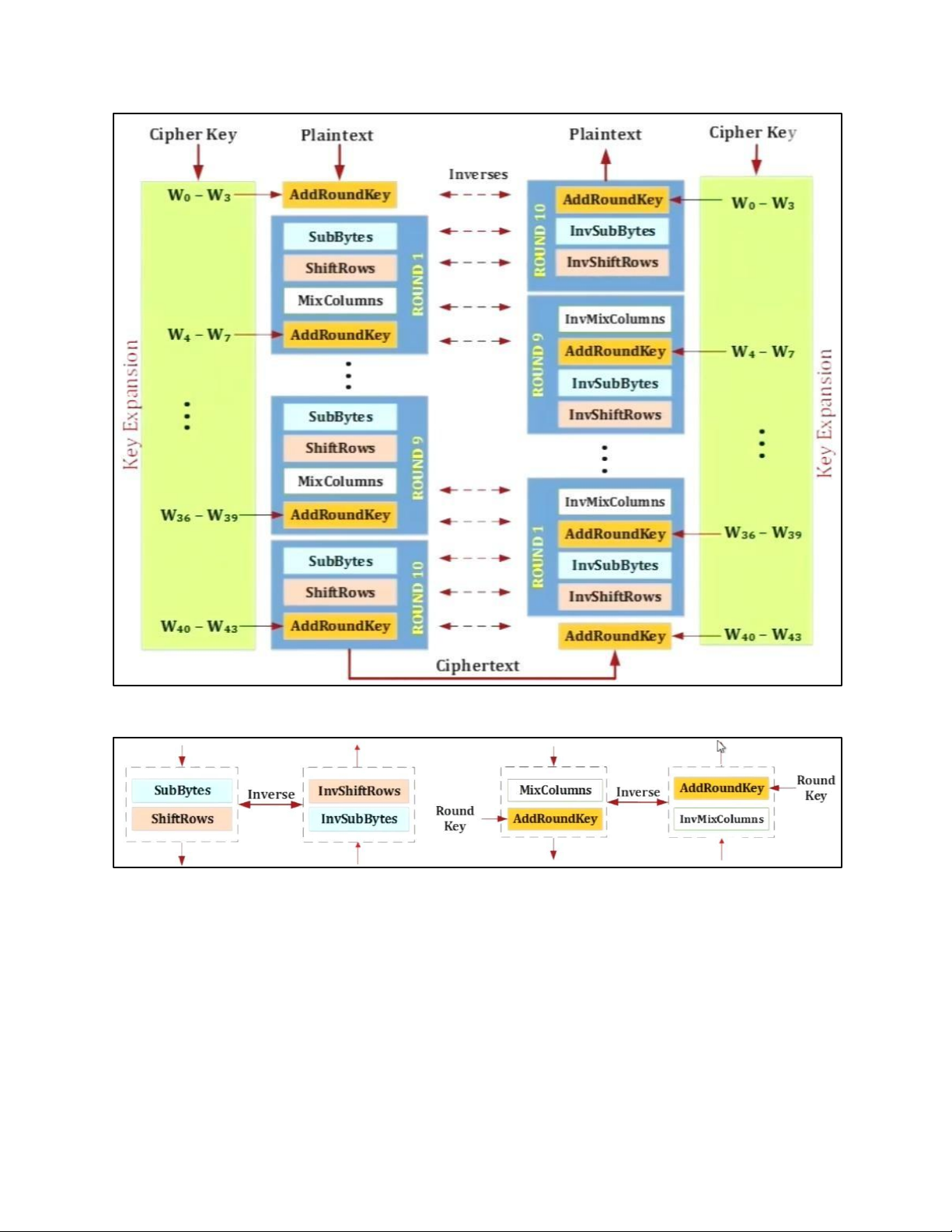
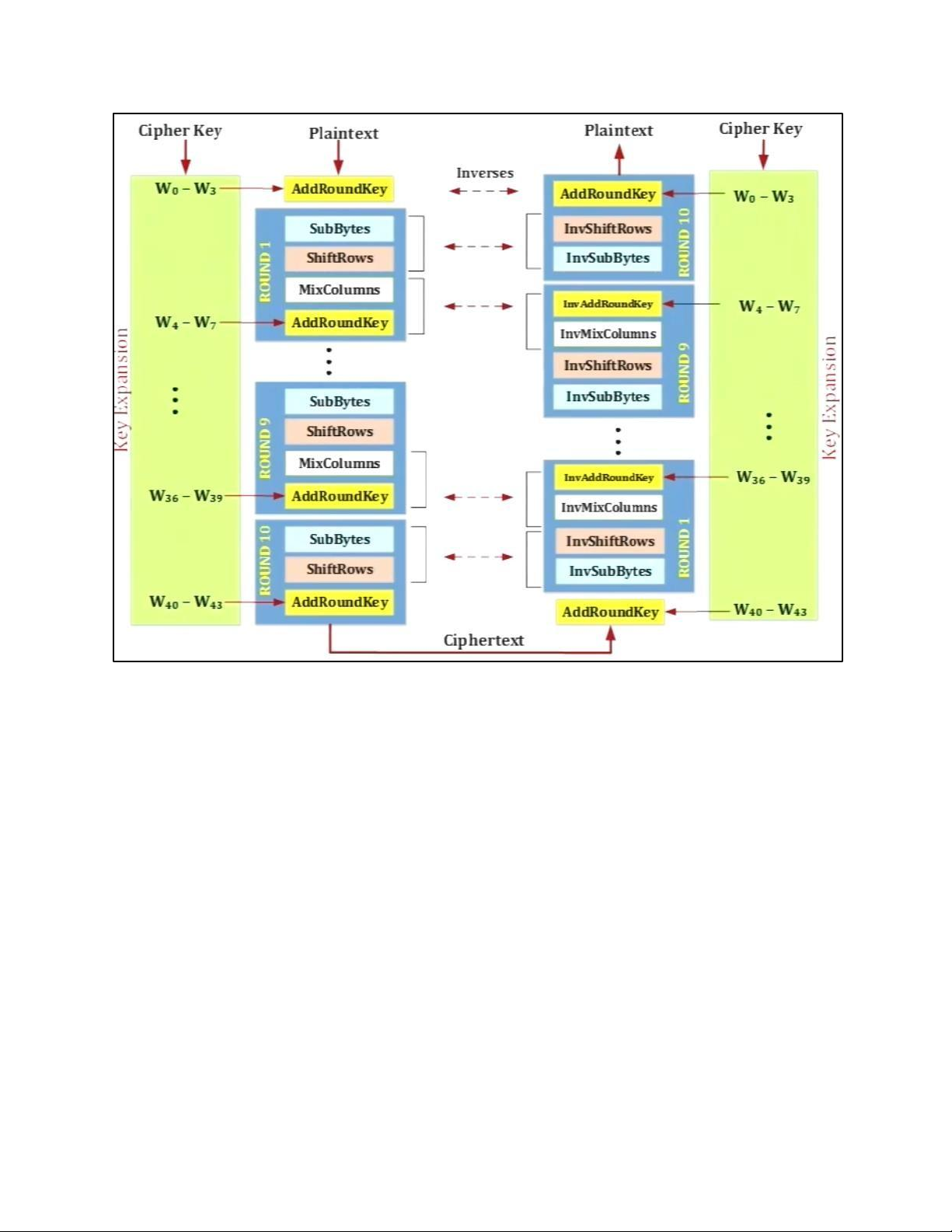
lOMoAR cPSD| 61548596 4. DES TẠI MỖI ROUND: lOMoAR cPSD| 61548596 H M DES: lOMoAR cPSD| 61548596 EXPANSION PBOX: KEY GENERATION: lOMoAR cPSD| 61548596 lOMoAR cPSD| 61548596 5. AES 5.1 . AES CIPHER a. AES CIPHER ARCHITECTURE lOMoAR cPSD| 61548596
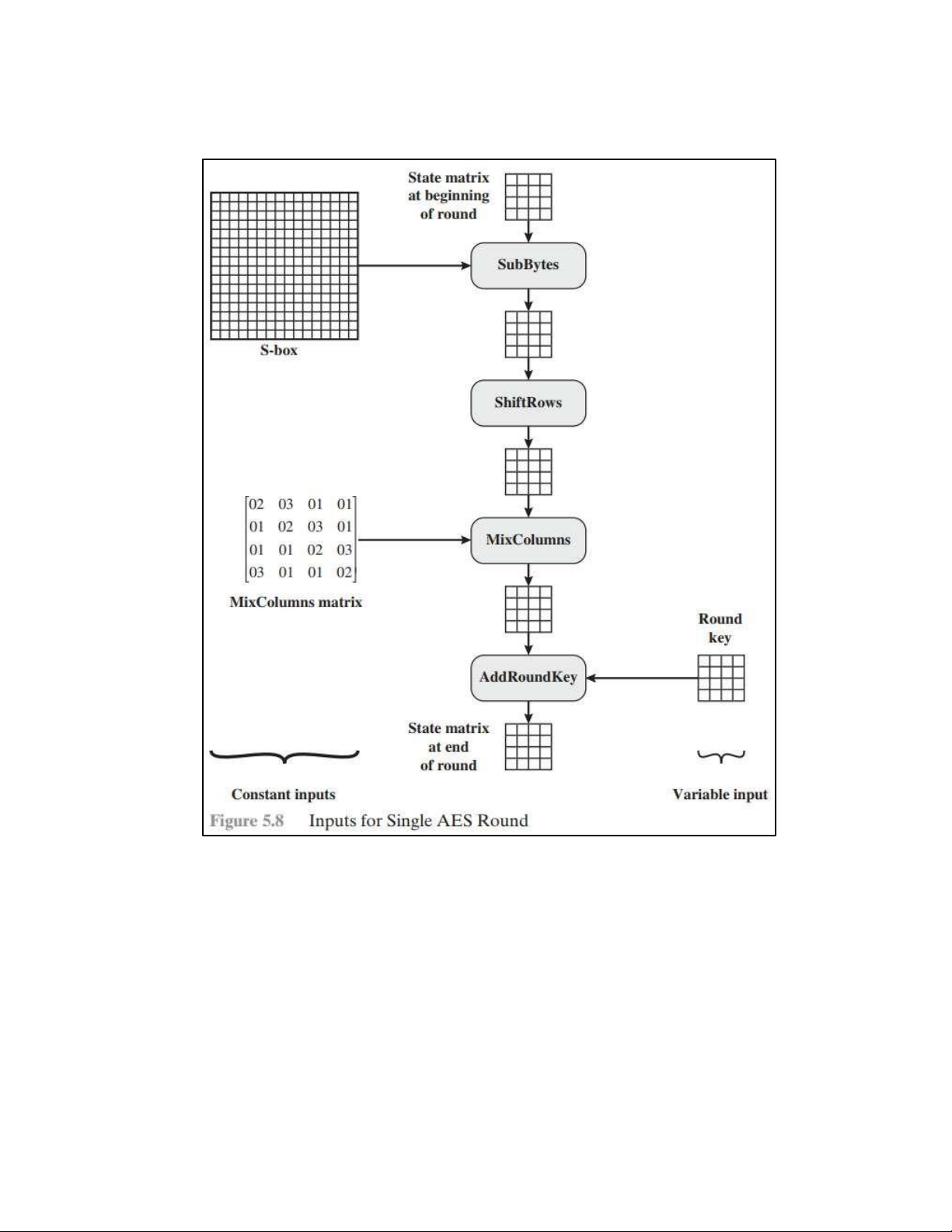
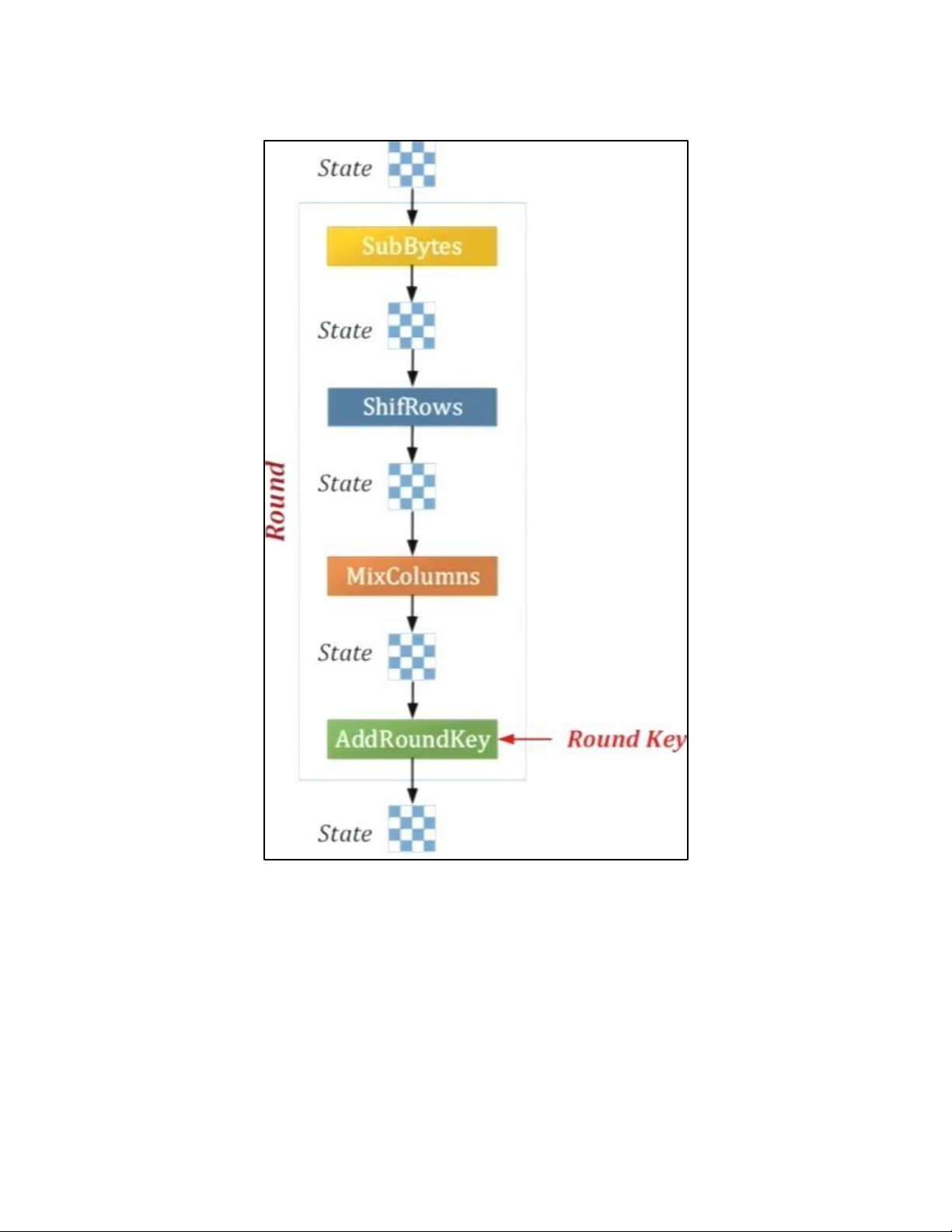
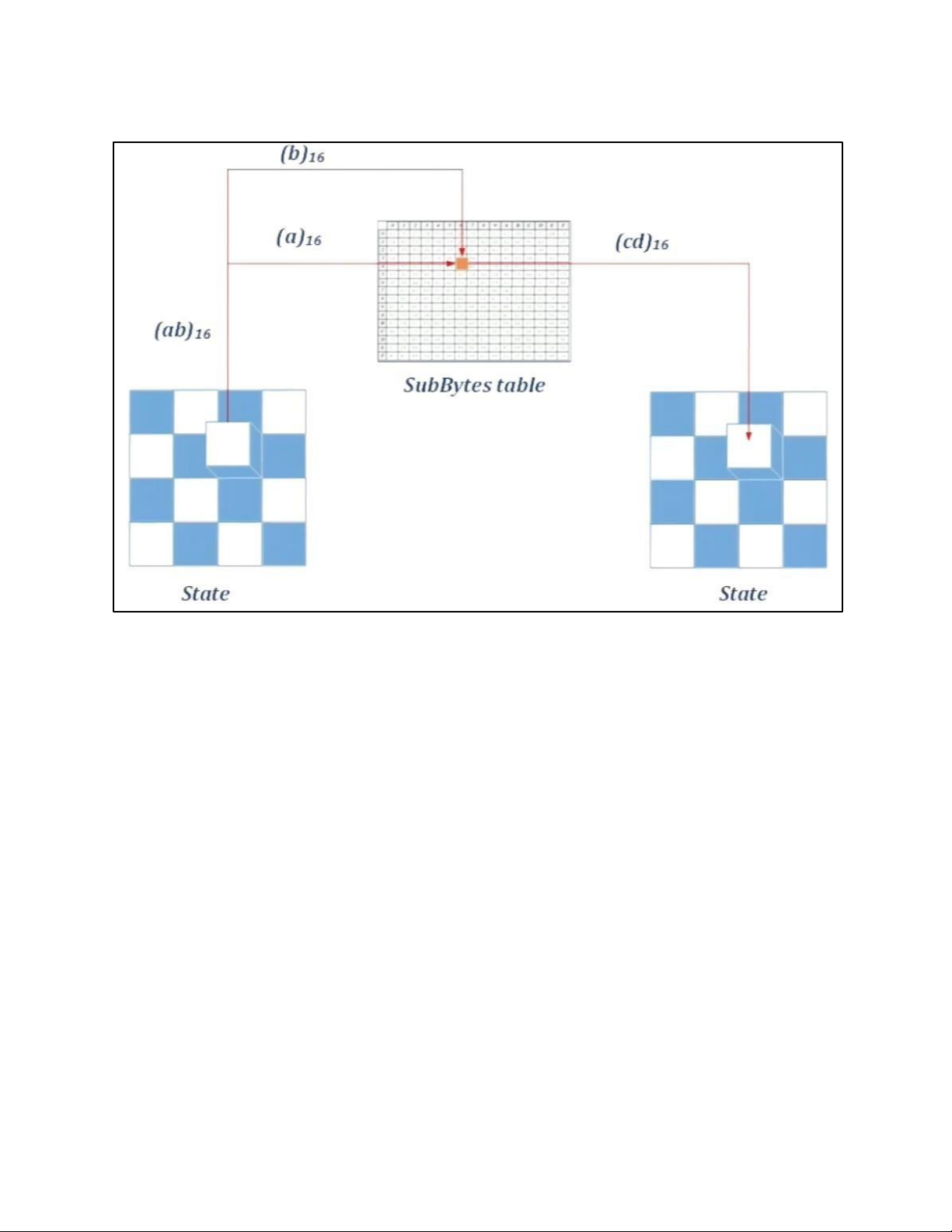
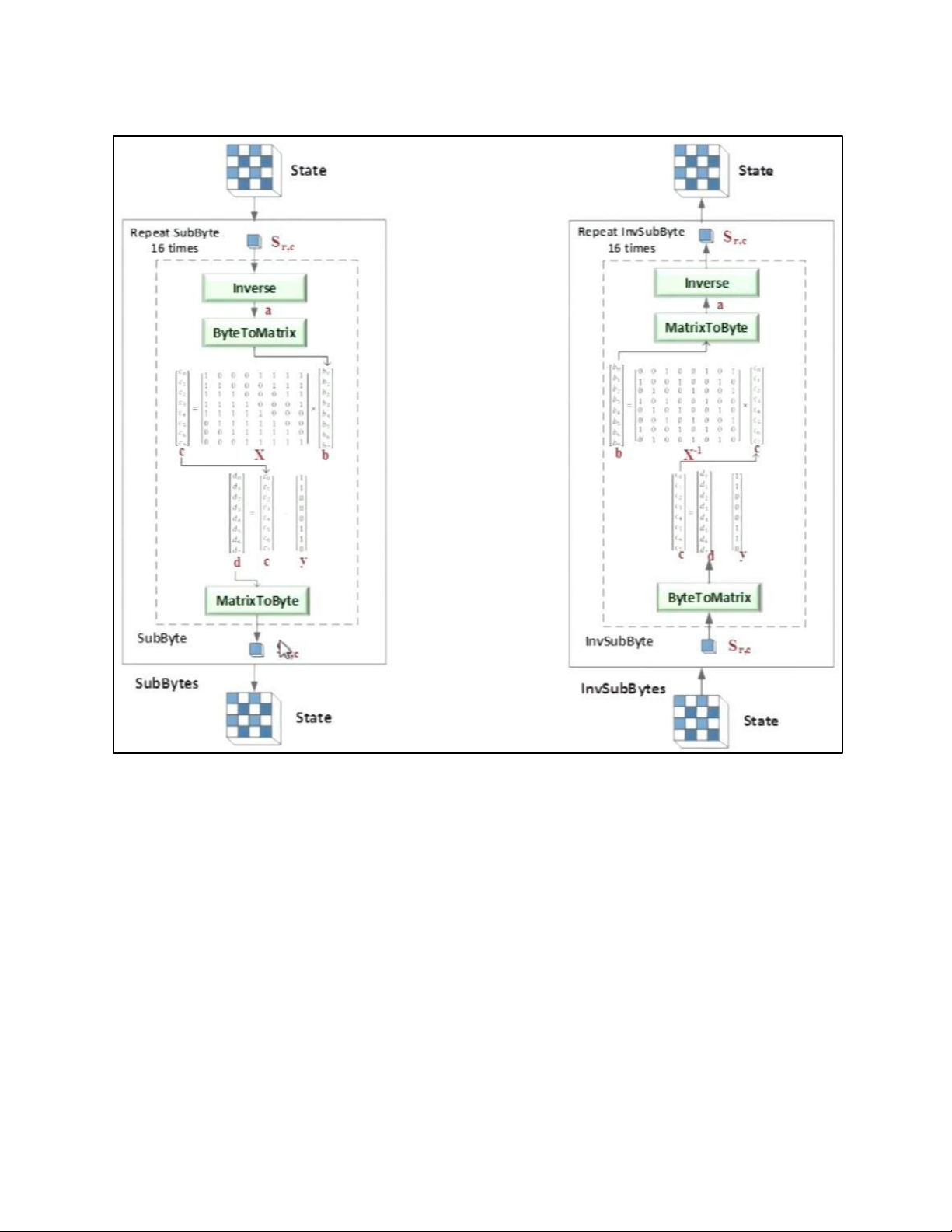
• BLOCK TO STATE AND STATE TO BLOCK TRANSFORMATION lOMoAR cPSD| 61548596 • STRUCTURE OF EACH ROUND b. AES PRINCIPLE • SUBSTITUTION lOMoAR cPSD| 61548596 - SUBBYTES lOMoAR cPSD| 61548596
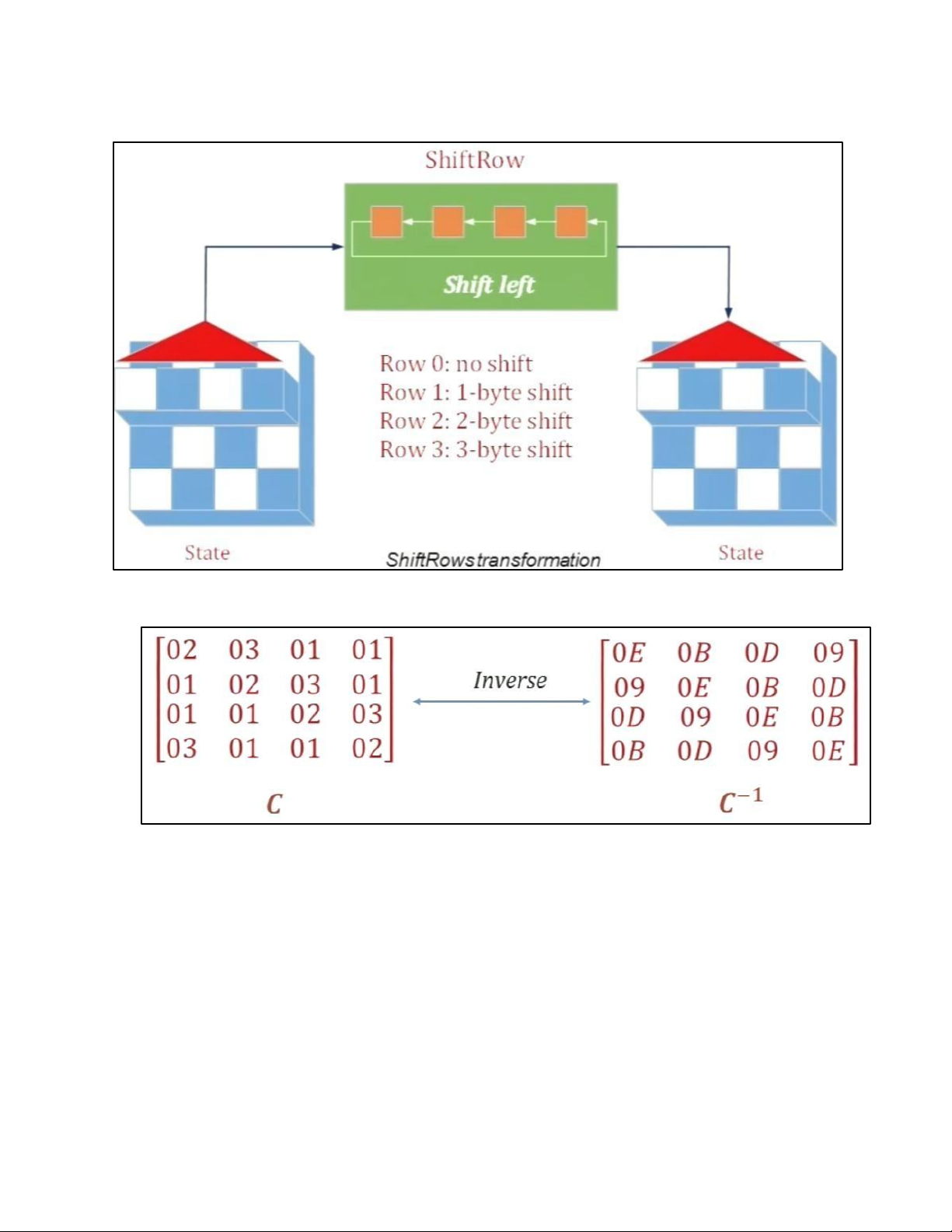
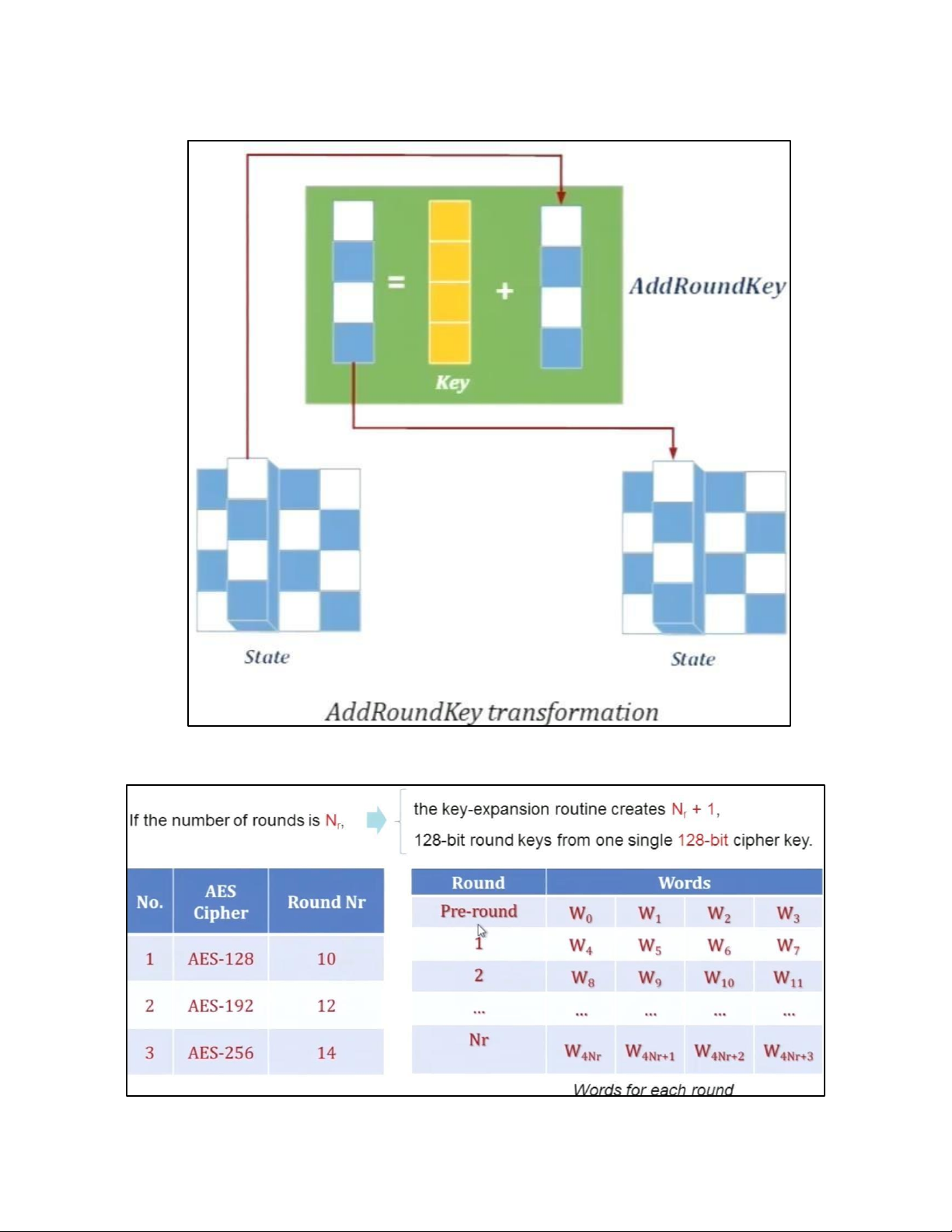
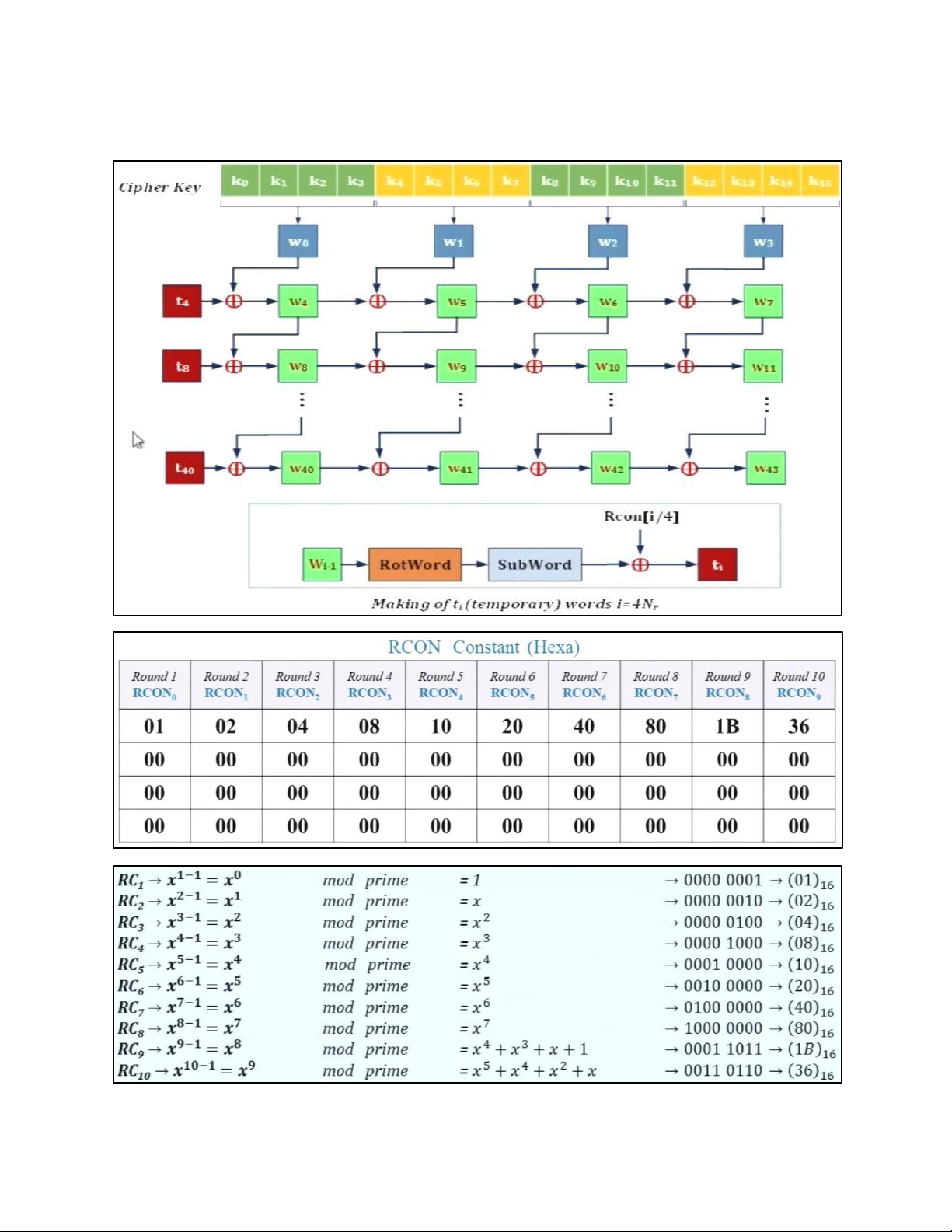
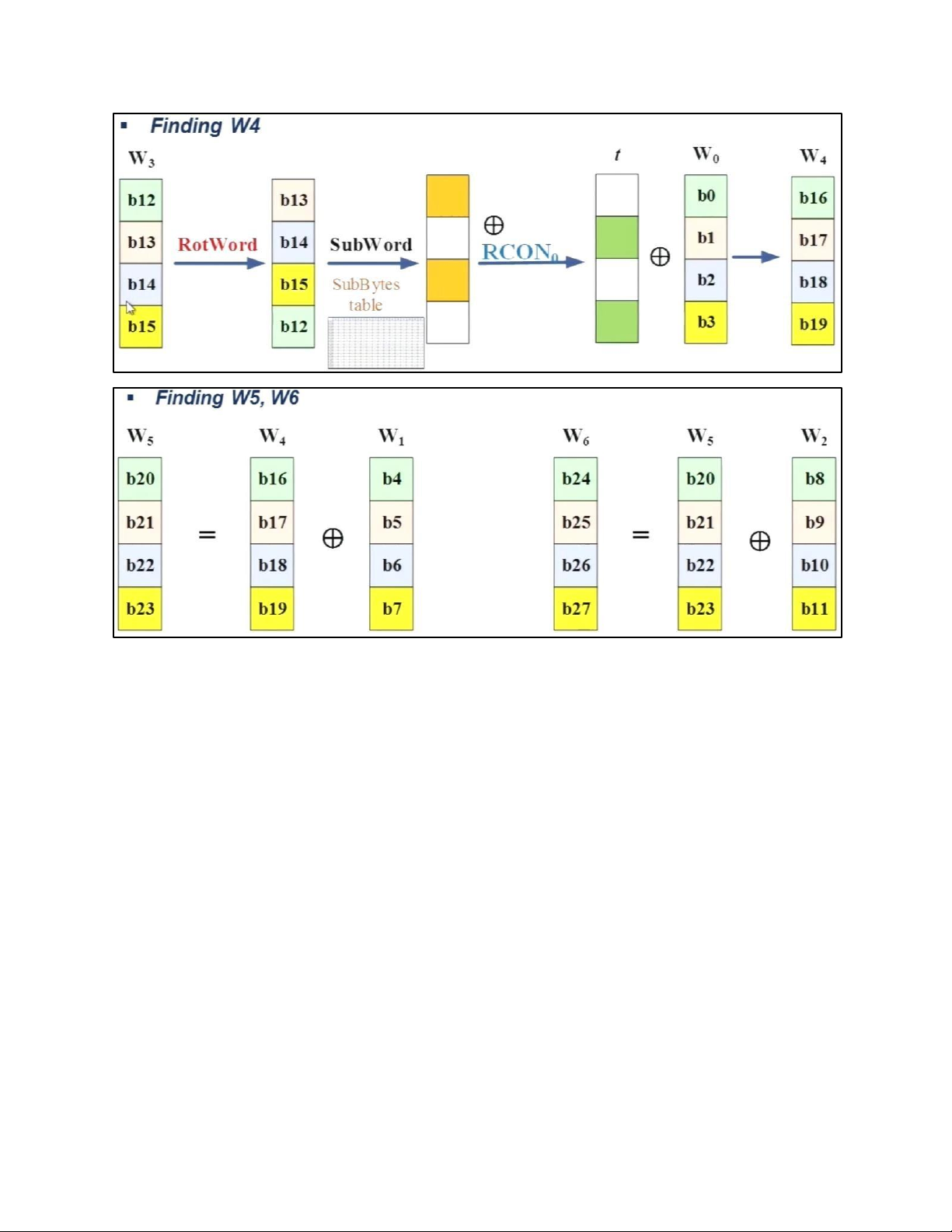
- TRANSFORMATION USING GF (28) • PERMUTATION lOMoAR cPSD| 61548596 - SHIFTROWS • MIXING lOMoAR cPSD| 61548596 • KEY – ADDING c. KEY EXPANSION lOMoAR cPSD| 61548596 KEY EXPANSION IN AES 128 lOMoAR cPSD| 61548596 lOMoAR cPSD| 61548596 5.2 . AES CIPHER DESIGN a. ORIGINAL DESIGN lOMoAR cPSD| 61548596 b. ALTERNATIVE DESIGN lOMoAR cPSD| 61548596
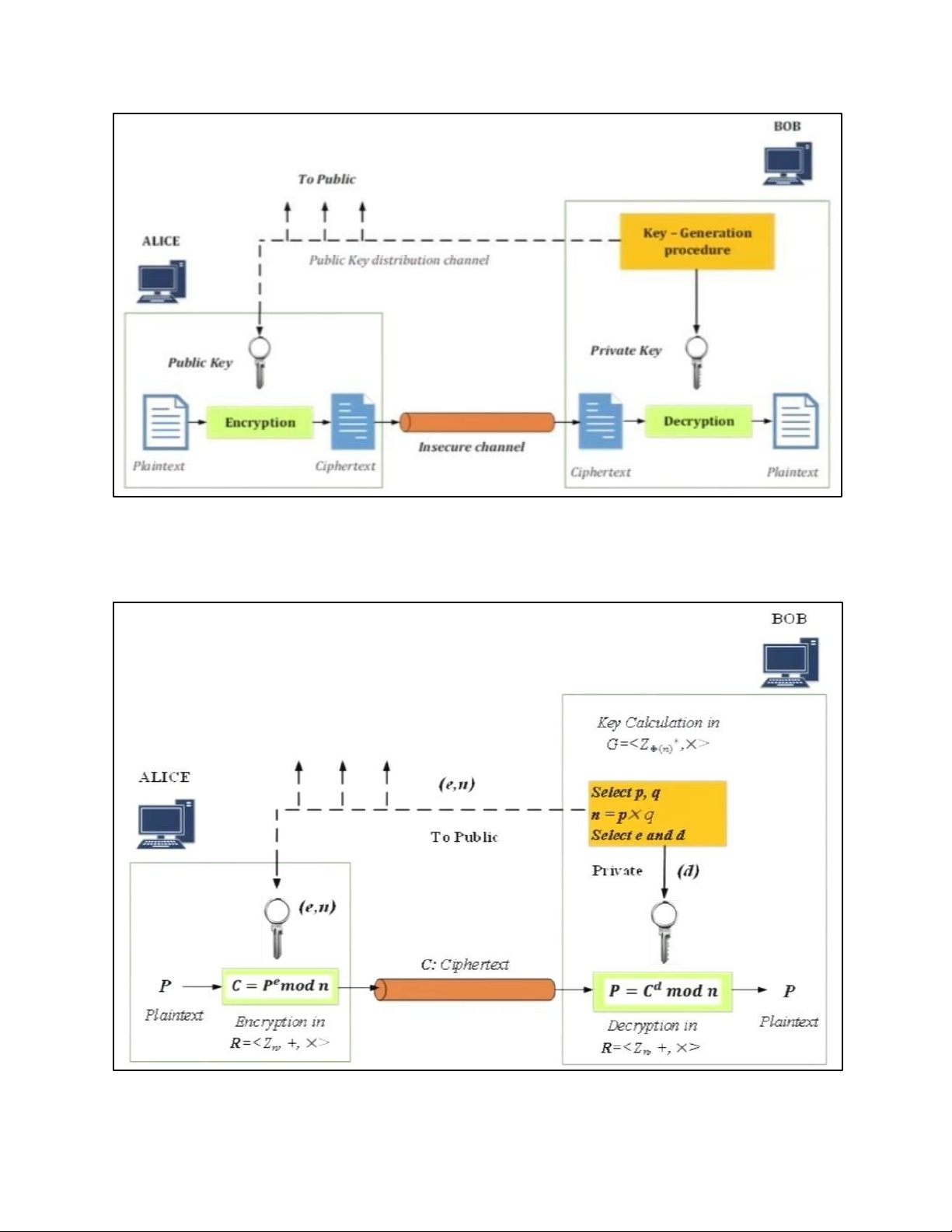
6. INTRODUCTION TO PUBLIC KEY CRYPTOGRAPHY 6.1. PUBLIC KEY a. SYSTEM STRUCTURE lOMoAR cPSD| 61548596
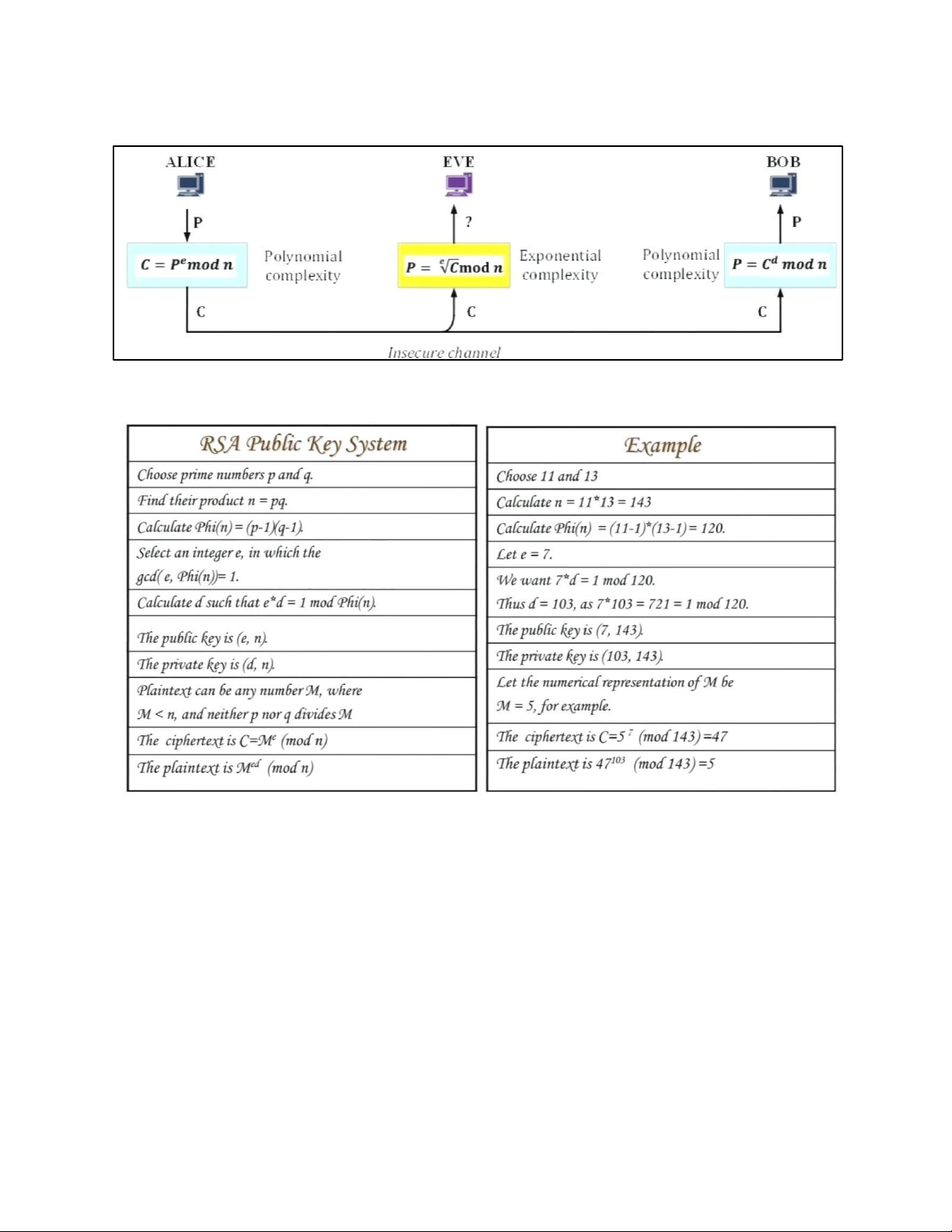
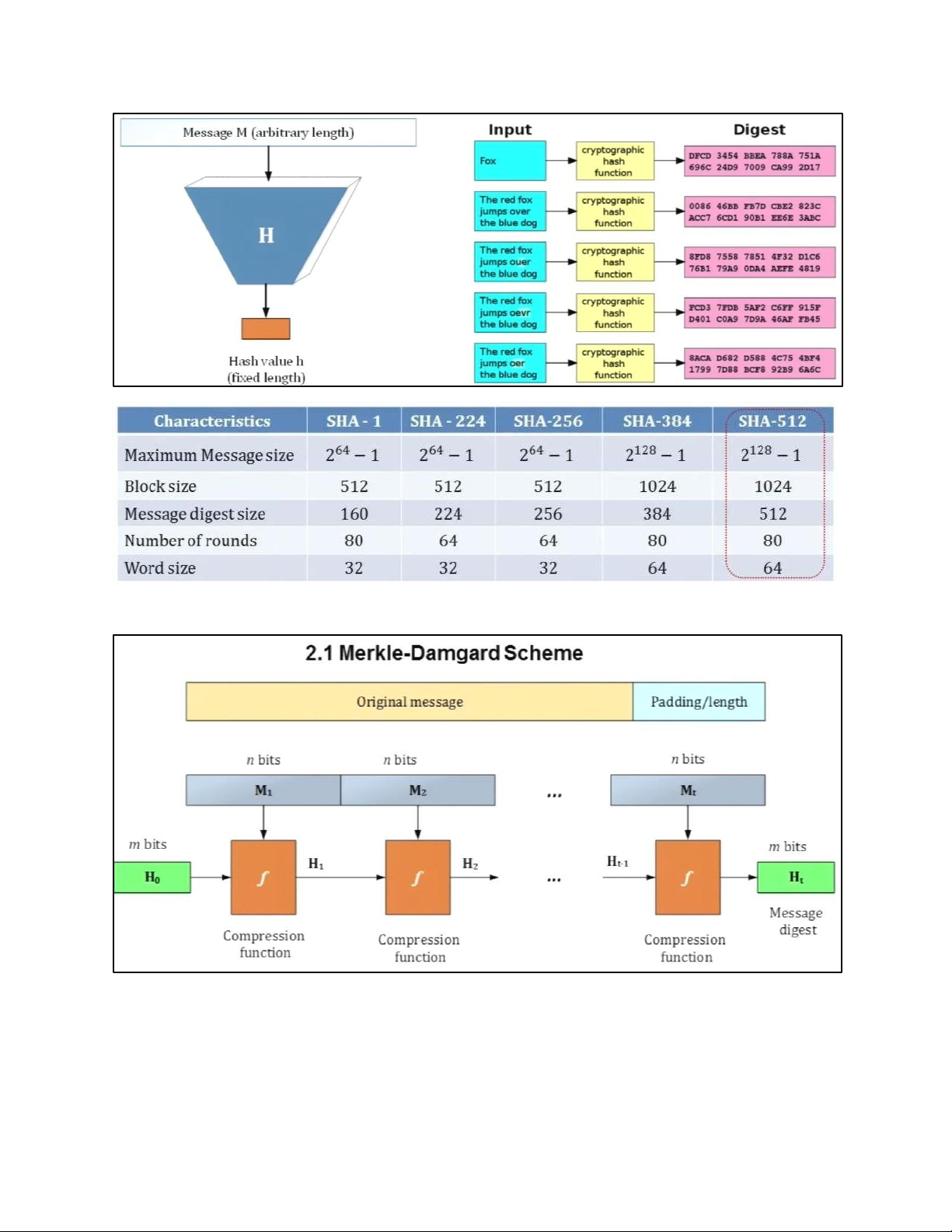
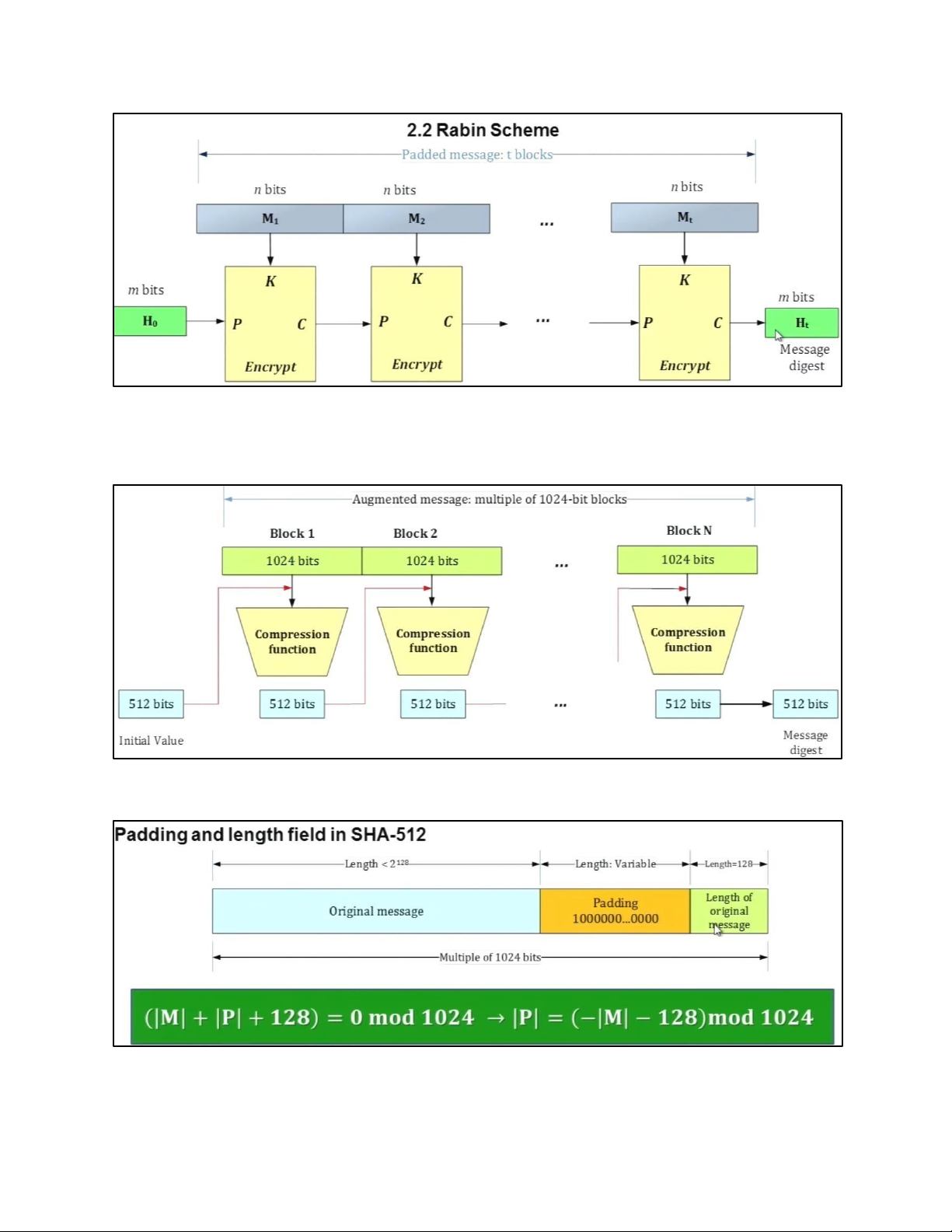
7 . RSA CRYPTOGRAPHY 7.1. SYSTEM MODEL lOMoAR cPSD| 61548596 7.2. RSA CRYPTOGRAPHY 7.3 . SUMMARIZED EXAMPLE 8. HASH FUNCTION 8.1. INTRODUCTION lOMoAR cPSD| 61548596 8.2. HASH FUNCTION SCHEME lOMoAR cPSD| 61548596 8.3 . SHA-512 a. ALGORITHM STRUCTURE b. PRINCIPLE


