














Preview text:
lOMoAR cPSD| 58886076
UNIVERSITY OF INFORMATION AND TECHNOLOGY VIETNAM - KOREA
DEPARTMENT OF COMPUTER SCIENTIST SYSTEM PROGRAMMING REPORT
TOPIC: INTER PROCESS COMMUNICATION SHARED MEMORY Instructor : Dr. Hoang Huu Duc
Student perform : Nguyen Duc Van 21IT391 Phan Van Xuat 21IT256 Nguyen Van Vi 21IT661 Nguyen Phan Vinh 21IT663 Class : System Programming(2) Da Nang, November 19, 2023
UNIVERSITY OF INFORMATION AND TECHNOLOGY VIETNAM - KOREA
DEPARTMENT OF COMPUTER SCIENTIST lOMoAR cPSD| 58886076 SYSTEM PROGRAMMING REPORT
TOPIC: INTER PROCESS COMMUNICATION SHARED MEMORY Instructor : Dr. Hoang Huu Duc
Student perform : Nguyen Duc Van 21IT391 Phan Van Xuat 21IT256 Nguyen Van Vi 21IT661 Nguyen Phan Vinh 21IT663 Class : System Programming(2) Da Nang, November 19, 2023 Acknowledgment
To research this topic, our team received significant support and assistance from our
supervising lecturer, Dr.Hoang Huu Duc. With deep and sincere gratitude, we would
like to express our appreciation to him and all our colleagues who worked together,
provided help, and conducted research throughout the project. Given the constraints
of time and limited experience, this report may not be free from shortcomings. We
eagerly anticipate guidance and input from our lecturer. lOMoAR cPSD| 58886076
Our team sincerely thanks you! lOMoAR cPSD| 58886076 DIVISION OF WORK Name ID student Role Assigned work Nguyen Duc Van 21IT391 Leader Phan Van Xuat 21IT256 Member Nguyen Van Vi 21IT661 Member Nguyen Phan Vinh 21IT663 Member lOMoAR cPSD| 58886076 TABLE OF CONTENT PREAMBLE 2 1 Reason for choosing the topic 2 2 Topic Objectives 2 3 Direction of the topic 3 4 Research subjects 3 5 Research scope 3 CHAPTER 1:INTRODUCTION 4 1.1
Overview of system programming 4 1.2
General information about IPC 5 1.3 Main methods of IPC 6 1.3.1 Socket 6 1.3.2 Message Queues 7 1.3.3 Shared Memory 7 1.3.4 Pipes 7 1.3.5 RPC (Remote Procedure Call) 7 1.3.6 Synchronization mechanism 7 1.4 Introducing shared memory 8 1.4.1 Concept of shared memory 8 1.4.2 Shared Memory works 9 1.5 Overview of key technologies 9 1.5.1 Vmware 9 1.5.2 The C programming language 11
CHAPTER 2: DESIGN AND IMPLEMENTATION 13 2.1 Shared memory application 13 2.1.1
Multi-process and multi-threaded system 13 2.1.2 Database 13 2.1.3
Embedded systems and real-time systems 14 2.1.4 Handling distributed tasks 14 2.1.5
Communication between different applications 14 2.2
Mechanism of operation of shared memory 14 2.2.1 Create shared memory 14 2.2.2 Connect to memory area 14 lOMoAR cPSD| 58886076 2.2.3
Communication and data exchange 15 2.2.4 Access coordination 15 2.2.5 Disconnect and release memory 15 2.3
Advantages and disadvantages of shared memory 15 2.3.1 Advantages of Shared Memory 15 • High Performance 15 • Fast Communication 15 • Ease of Deployment 15 • Extensibility 15 2.3.2
Disadvantages of Shared Memory 16 • Data distribution 16 • Potential for collision 16 • Data security 16 • Difficulty in debugging 16 • Race conditions 16 • Share unstructured data 16 Chapter 3: DEMO 17 References 24 LIST OF IMAGES
Picture 1 1 System programming..............................................................................................4
Picture 1 2 Inter-Process Communication(IPC)..........................................................................5
Picture 1 3 Shared Memory.....................................................................................................8
Picture 1 4 VMware................................................................................................................9
Picture 1 5 The C programming language................................................................................10
Picture 2 1 Shared memory application...................................................................................12
Picture 3 1 Code check phone number....................................................................................16
Picture 3 2 Run Code check phone number..............................................................................16
Picture 3 3 Code check email.................................................................................................17
Picture 3 4 Run Code check email..........................................................................................17
Picture 3 5 Code check read file.............................................................................................18
Picture 3 6 Code displays the contact list.................................................................................18
Picture 3 7 Run Code displays the contact list..........................................................................18
Picture 3 8 Code add people to the list....................................................................................19
Picture 3 9 Run code add people to the list..............................................................................19
Picture 3 10 Code to export contacts to file..............................................................................20
Picture 3 11 Run code to export contacts to file........................................................................20 lOMoAR cPSD| 58886076
Picture 3 12 Code edit people in contacts................................................................................21
Picture 3 13 Run code edit people in contacts..........................................................................21
Picture 3 14 Code delete people from contacts.........................................................................22
Picture 3 15 Run code delete people from contacts...................................................................22 lOMoAR cPSD| 58886076 PREAMBLE
In today's technology-driven world, optimizing interactions among system
components plays a crucial role, with Inter Process Communication (IPC) becoming
an indispensable aspect in the field of system programming.
We chose to delve into the study and implementation of Shared Memory, a powerful
IPC method, to achieve flexibility and high performance in transmitting information
between processes. This report promises to provide a profound insight into the
research, design, and deployment process of an application utilizing Shared Memory.
We anticipate that by sharing our experiences and knowledge gained, this report will
contribute to enriching the understanding within the system programming
community. We hope that the outcomes of this project will help readers gain a
clearer understanding of the vital role IPC and Shared Memory play in constructing efficient software systems. 1 Reason for choosing the topic
We have chosen the topic "Inter Process Communication - Shared Memory" for
several significant reasons. In today's technology-driven world, efficient interaction
among system components plays a crucial role, and Inter Process Communication
(IPC) becomes an indispensable factor. The decision to research and implement
Shared Memory is motivated by its flexibility and high performance in transmitting
information between processes. This promises to provide a profound insight into the
research and deployment process of applications, contributing to the enrichment of
knowledge within the system programming community. We anticipate that the
outcomes of this project will help readers gain a clearer understanding of the crucial
role IPC and Shared Memory play in constructing efficient software systems. 2 Topic Objectives
• Develop a solid understanding of the concept of Shared Memory and other IPC methods.
• Grasp the mechanism and pros/cons of Shared Memory.
• Implement a demo Application Using Shared Memory.
• Learn and apply analysis, testing, and debugging methods and tools during
declarative development and application demos.
• Evaluate application performance and stability.
• Present the results and experiences from the implementation and demo
process in a project report, including analysis, experimental results and comments. 3 Direction of the topic
The direction of the topic "Implement and Demo for Sockets in IPC" in the project
report can be implemented according to the following chapters: • Chapter 1: INTRODUCTION lOMoAR cPSD| 58886076
• Chapter 2: DESIGN AND IMPLEMENTATION • Chapter 3: DEMO 4 Research subjects
The topic "Inter Process Communication Shared Memory" may be suitable for
university students, software developers, researchers and anyone interested in the
process of exchanging information between processes. 5 Research scope
Inter Process Communication (IPC):
- Investigate fundamental aspects of various IPC methods.
- Compare and evaluate the effectiveness of IPC in facilitating interaction between processes. Shared Memory:
- Focus on the implementation and application of Shared Memory in interprocess communication.
- Research safety mechanisms such as Semaphores and Mutex to ensure
stability and security in memory sharing.
Real-world Application Deployment:
- Develop a practical application utilizing Shared Memory for information exchange between processes.
- Evaluate performance and optimize within the context of real-world application usage.
Integration of Feature Expansion and Scalability:
- Research and implement additional features to enhance the application's functionality.
- Assess the application's scalability on large systems with multiple processes.
Performance Evaluation and Comparison with Other IPC Methods:
- Conduct a performance evaluation of the application using Shared Memory
and compare it with other IPC methods.
Results Analysis and Discussion:
- Analyze the achieved results from implementation and evaluation.
- Discuss limitations, challenges, and the significance of the findings. CHAPTER 1:INTRODUCTION
1.1 Overview of system programming 1.1.1 System programming concepts lOMoAR cPSD| 58886076
Picture 1 1 System programming
System programming is the activity of developing system software. Firstly, it
highlights the distinct nature of system programs when compared to application
programming, where application programming aims to create software that provides
services to users (e.g., word processors), whereas system programmers focus on
producing software that delivers services to computer hardware (e.g., disk
defragmentation software). It also necessitates a greater awareness of hardware considerations.
1.1.2 System programming overview
More special points in system programming:
• System programmers will bear the responsibilities related to hardware and
certain attributes of programs running on that system, and they will often
leverage those attributes (for example, by using an algorithm known to be
effective when employed with specific hardware).
• Typically, a low-level programming language or assembly language is
employed for the following reasons:
- Can operate in resource-constrained environments.
- Highly efficient and capable of performing close to the hardware.
- Has a minimal or no runtime library.
- Allows direct and "raw" control through memory access and control flow.
- Enables programmers to write portions of the program directly in assembly language.
System programmers differ significantly from application programmers who
specialize in one domain or another.
In system programming, there are often limited programming tools available. The
use of automatic garbage collection is not common, and debugging can be lOMoAR cPSD| 58886076
challenging at times. Implemented libraries, if available at all, are often less robust
than those in more common programming languages, leading to fewer error checks.
Due to these limitations, consoles and logging are frequently employed, and
operating systems may extensively utilize hierarchical logging systems.
System programmers perform specific tasks within an operating system and network
operations, such as implementing paging (virtual memory) or a device driver for an operating system.
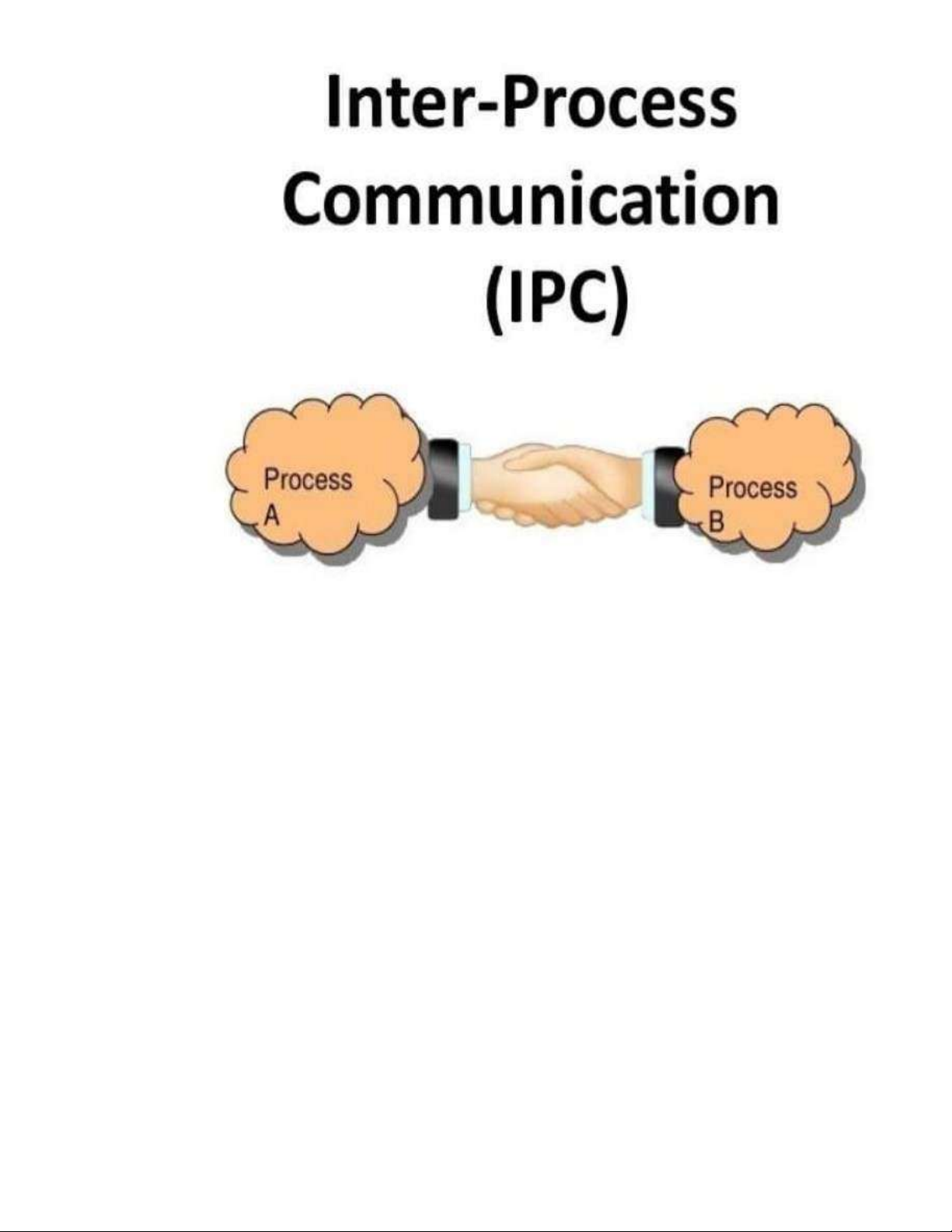
1.2 General information about IPC
IPC stands for "Inter-Process Communication" in the field of information technology
and computer programming. IPC is the way different processes on a computer system
or within a network can communicate, exchange information, and interact with each
other. This enables different processes to perform distinct tasks and collaborate to
accomplish larger objectives or share data and resources with each other. lOMoAR cPSD| 58886076
Picture 1 2 Inter-Process Communication(IPC) 1.3 Main methods of IPC 1.3.1 Socket
- TCP/IP Socket utilizes the Transmission Control Protocol (TCP) to establish a
reliable connection between two endpoints. The endpoints can be two
processes on the same computer or two different computers on a network.
TCP ensures data integrity and correct sequencing, providing mechanisms
such as error control, flow control, and authentication.
- UDP Socket uses the User Datagram Protocol (UDP), a less reliable protocol
compared to TCP. UDP does not guarantee data integrity and sequencing. This
may be suitable for applications that require fast data transmission and can
tolerate data loss, such as live streaming or online gaming.
- By using sockets, applications can establish network connections and
send/receive data over the network through TCP/IP or UDP protocols. An
application can run as a server, listening for connection requests from other
applications and handling them. Alternatively, it can run as a client,
establishing a connection to an existing server and transmitting data over the network.
- With TCP/IP or UDP sockets, different processes or computers can
communicate and share data over the network or on the same computer. lOMoAR cPSD| 58886076 1.3.2 Message Queues
- Use queues to allow processes to send and receive text messages or structured
data. Message queues can be utilized for sending and receiving simple text
messages or structured data. Simple text messages are often used for control
communication or notifications between processes, while structured data can
include records, complex data structures, or serialized objects.
- Processes can send messages to a queue at any time, and the receiving process
can dequeue messages in the order they were placed in the queue. This creates
an asynchronous communication between processes, allowing them to operate
independently and without dependencies on each other. Message queues are a
common mechanism for IPC in multiprocess or distributed systems. They
enable processes to communicate safely and efficiently, ensuring data
integrity during communication. 1.3.3 Shared Memory
- Is a mechanism in the operating system that allows processes to share a
portion of common memory. Instead of copying data back and forth between
processes, they can directly access the same memory region. This speeds up
data access and reduces overhead associated with data copying. 1.3.4 Pipes
- Are a mechanism in the operating system used to transmit data between
parent and child processes in a process communication model. Pipes are
created by connecting the output of one process to the input of another
process, forming a one-way communication channel.
1.3.5 RPC (Remote Procedure Call)
- Is a protocol and programming model that allows calling functions or
methods from a remote process in a manner similar to calling functions within
the same process. RPC enables applications running on different computers in
a network to interact and communicate with each other through remote function calls.
1.3.6 Synchronization mechanism
- Are used to ensure consistency and safety in the execution of concurrent
processes. Mechanisms such as semaphores, mutexes, and conditions are
essential tools in building synchronization solutions.
- Semaphore: Semaphore is a synchronization variable used to control access to
a shared resource. It holds a non-negative integer value and supports two
main operations, "wait" and "signal." When a process wants to access the
resource, it must invoke the "wait" operation on the semaphore. If the
semaphore value is positive, the process decreases the semaphore value and
continues execution. If the value is non-positive, the process is blocked and
waits until the semaphore is increased by another process using the "signal"
operation. Semaphores enable control over concurrent access to resources and
help avoid issues such as conflicts and starvation. lOMoAR cPSD| 58886076
- Mutex (Mutual Exclusion): Mutex is a synchronization mechanism used to
ensure that only one process can access a shared resource at a time. Mutex is
often employed to protect sections of code called a "critical section," where
shared data may be subject to conflicts. A process wishing to access the
critical section must invoke the "lock" operation on the mutex before
performing operations on shared data and call the "unlock" operation after
completion. If the mutex has already been locked by another process, the
current process will be blocked until the mutex is released. Mutex helps
ensure consistency and prevent conflicts when accessing shared data.
- Condition: Condition is a synchronization mechanism used to manage waiting
and signaling between processes. Conditions are often employed in
synchronization scenarios following the "producer-consumer" model or
similar scenarios. A process can invoke the "wait" operation on a condition to
wait for a specific condition to be met. When the condition is met, another
process can send a signal through the "signal" or "broadcast" operation to
notify the waiting processes. Conditions help manage waiting and signaling
between processes and avoid issues such as indefinite waiting or false wakeups. 1.4 Introducing shared memory
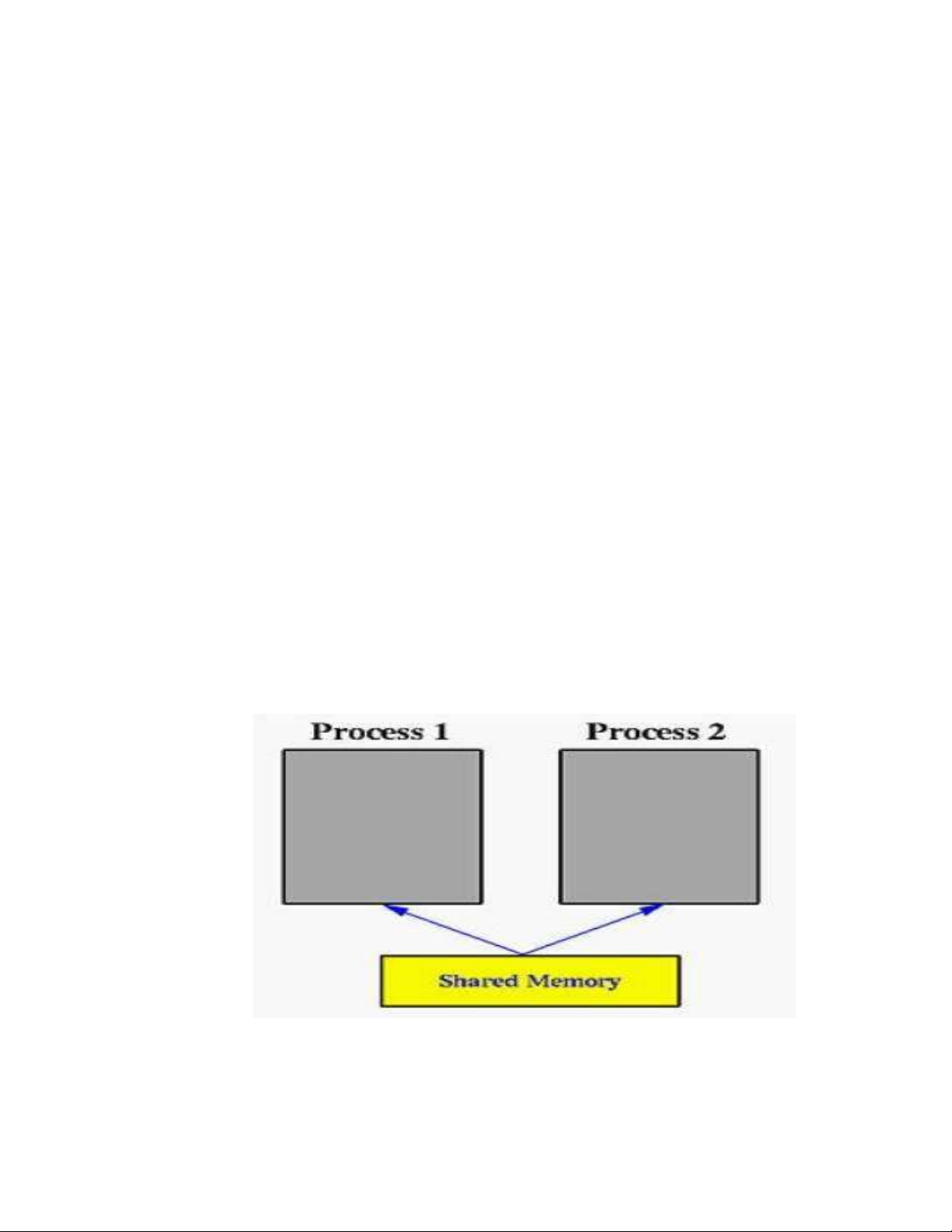
1.4.1 Concept of shared memory
- Shared Memory is a mechanism that allows multiple processes or threads in a
computer system to access and share the same physical memory area (RAM)
to exchange data. In shared memory, processes can read and write data to this
shared memory area, allowing them to interact and communicate quickly and efficiently. Picture 1 3 Shared Memory 1.4.2 Shared Memory works
- Create and Attach: One process, often the "creator" process, creates a shared
memory region through the system API (e.g., shmget in Unix). Another lOMoAR cPSD| 58886076
process, typically the "attacher" process, uses the same key to access that shared memory region.
- Access Data: Once the shared memory region is created and attached,
processes can directly access it like any other memory region using pointers or variables.
- Synchronization: To ensure consistency and avoid data conflicts, processes
often need to use synchronization mechanisms such as semaphores or
mutexes. This is particularly crucial when multiple processes are concurrently performing write operations.
- Release and Detach: When processes no longer need the shared memory
region, they can release it to allow other processes to use it. Simultaneously, a
process can detach from the shared memory region when it's no longer needed.
- Remove Memory Region: In some cases, the creating process may decide to
remove the shared memory region after it's no longer in use. This ensures that
the shared memory region won't persist after all processes have finished using it.
1.5 Overview of key technologies 1.5.1 Vmware
VMware is a virtualization software system that enables users to run multiple
operating systems (OS) on the same computer. It allows users to install an operating
system within a virtual environment while maintaining the original host operating system on the computer. Picture 1 4 VMware lOMoAR cPSD| 58886076
With VMware, users can run multiple different operating systems on the same
computer without the need to reinstall each time they want to switch to a different
operating system. VMware also has the ability to share resources among virtual
operating systems, helping to save resources and increase system performance.
VMware was founded in 1998 by Diane Greene, Mendel Rosenblum, Scott Devine,
and Edward Wang. It is a multinational technology company with its headquarters in
Palo Alto, California, USA. VMware is one of the leading virtualization software
companies globally, offering various products and services related to system
virtualization, including VMware Workstation, VMware Fusion, and VMware vSphere. Main function of Vmware:
Create and manage virtual machines
- VMware provides tools and solutions that allow users to create and manage
virtual machines on their computers . These virtual machines resemble actual
computers, allowing users to run operating systems and other applications on them.
Manage computers in a corporate environment
- The tool will have features to help IT administrators manage and monitor
computers in a business environment, helping administrators easily manage
and maintain computer systems.
Synchronize computer environments
- For example, users can synchronize operating system settings, software
installations and other resources between different computers to reduce time
and effort spent on managing computer systems.
Increase computer security
- VMware also provides security tools and solutions that allow users to protect
computers and resources. These tools help prevent cyber attacks and prevent
the creation of security holes in computer systems.
Supports different operating systems
- You can use VMware on Macbook to support the installation of additional
Windows running in parallel, saving time and effort for system installation and management.
1.5.2 The C programming language
The C programming language is a computer programming language developed by
Dennis Ritchie in the 1970s at Bell Labs. C is a powerful, high-performance
programming language, and is widely used in systems software development,
embedded software, personal computer applications, and many other industrial sectors. lOMoAR cPSD| 58886076
Picture 1 5 The C programming language
C focuses on memory management and provides many features that are closely
related to computer architecture, giving programmers more detailed control over
how data and machine code are processed. It also has a simple and powerful syntax,
which helps in efficient and maintainable software development.
The C language has created the foundation for many other programming languages,
including C++, C#, and many others. Additionally, it is also a popular language for
writing operating systems and embedded software due to its hardware control capabilities.
Applications of C programming language
The C programming language has many different applications in many different
fields due to its flexibility, high performance, and close interaction with computer
architecture. Here are some popular applications of the C programming language:
- Operating system: C is widely used in operating system development. Most
popular operating systems today are written in C such as UNIX, Linux, Windows or MacOS.
- System software development : C is an ideal language for developing system
software, such as database managers (SQLite, MySQL, Berkeley DB ) , file
managers (ext4 on Linux). and NTFS on Windows), and important
components of the computer system.
- Embedded application development : C is often used in developing embedded
software, that is, software that runs on devices such as mobile phones,
medical equipment, industrial control equipment, and dynamic control
systems. mechanics, video games and many other applications. For example,
gaming consoles like PlayStation and Xbox, or Android/iOS operating
systems, are all written in C.
- Personal computer application development : C is still used for personal
computer application development, especially in areas that require high
performance such as computer games and graphics software. For example, lOMoAR cPSD| 58886076
games on Steam are written in Unity and Unreal Engine, the core of these software is written in C.
- Data analysis and scientific computing : C is often used in applications related
to scientific computing and data analysis. For example, libraries used in the
field of data science and machine learning such as OpenCV and TensorFlow
provide APIs for C/C++ to develop applications in this field.
- Writing libraries and frameworks : C is often used to write libraries and
frameworks that programmers can use to develop applications for a variety of
purposes. Some libraries are written in C such as OpenGL, OpenSSL, GTK+ (GIMP Toolkit),...
CHAPTER 2: DESIGN AND IMPLEMENTATION 2.1 Shared memory application
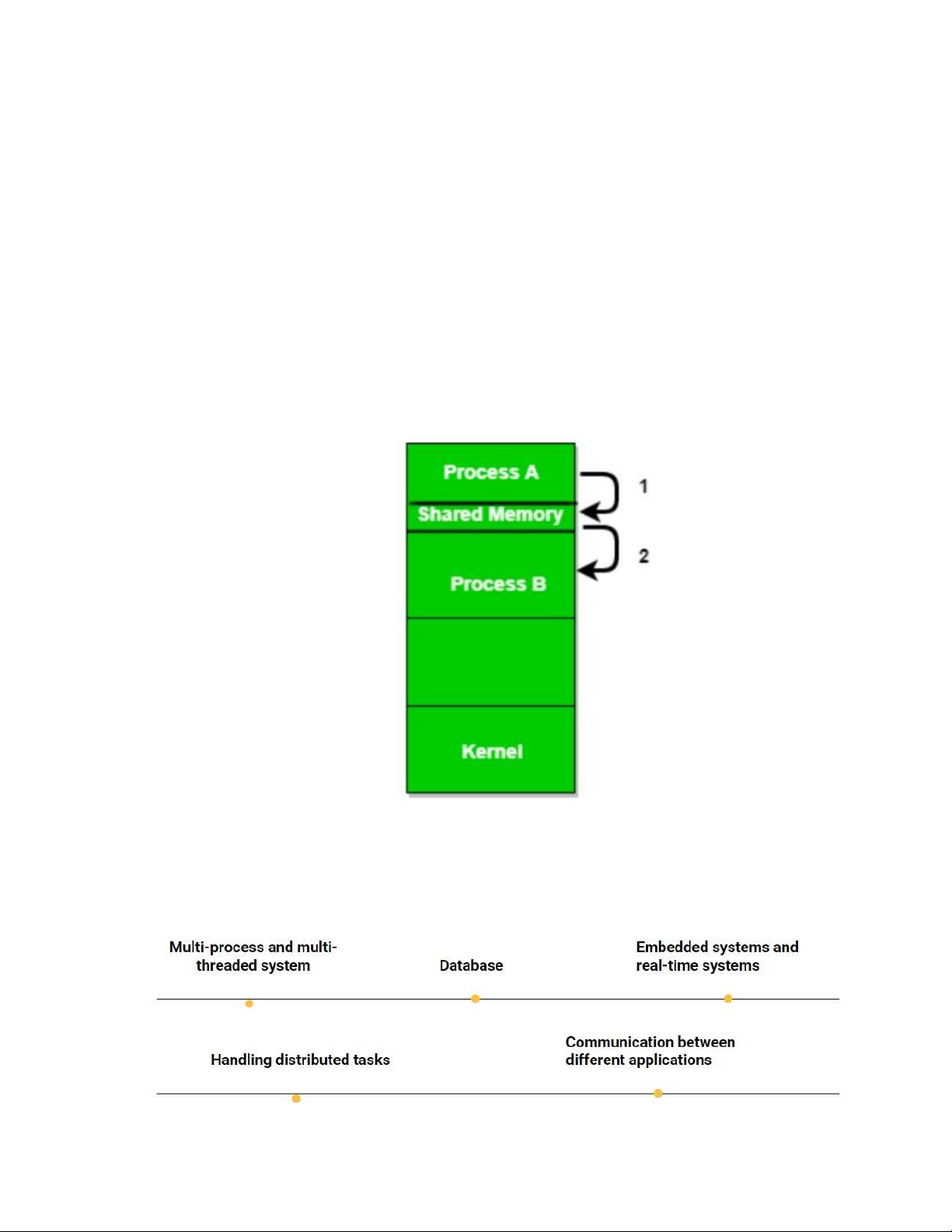
Picture 2 1 Shared memory application lOMoAR cPSD| 58886076
2.1.1 Multi-process and multi-threaded system
- Shared memory is often used to exchange data between processes or threads
in a multi-process or multi-threaded application. This increases performance
and allows processes or threads to work together to perform complex tasks. 2.1.2 Database
- In a database management system (DBMS), shared memory is used to store
and share cached data, which speeds up data access in the database and improves performance.
2.1.3 Embedded systems and real-time systems
- In embedded systems and real-time systems, shared memory is often used to
communicate and exchange data between system components.
2.1.4 Handling distributed tasks
- In distributed systems, shared memory can be used to exchange data between
different computers in the network to perform distributed tasks.
2.1.5 Communication between different applications
- In personal computing environments, shared memory can be used to
communicate and exchange data between different applications to provide interactive functionality.
2.2 Mechanism of operation of shared memory 2.2.1 Create shared memory
- Procedure: To start using shared memory, you need to create a
sharedmemory region. Typically, this is done using system functions such as
shmget() on Unix/Linux or CreateFileMapping() on Windows. During
creation, you provide the size of the memory area and a unique key to access it. lOMoAR cPSD| 58886076
- Details: During the creation process, you specify the size of the
memoryregion and assign a unique key for access. 2.2.2 Connect to memory area
- Procedure: Once the shared memory has been created, processes or
threadsthat want to use it need to connect to the memory using a function like
shmat() on Unix/Linux or MapViewOfFile() on Windows.
- Details: After connecting, processes can read and write data to this sharedmemory area.
2.2.3 Communication and data exchange
- Procedure: Once connected, processes can use shared memory
tocommunicate and exchange data. They can read data from the memory area
or write data to it on a regular basis.
- Details: Shared memory provides an efficient mechanism for processes
tointeract and share information. 2.2.4 Access coordination
- Procedure: Shared memory does not provide built-in access
coordinationmechanisms. Access management to shared memory must be done
by the processes that use it. This may entail using locks or semaphores to ensure there are no data conflicts. - Details: Effective access management often involves using
synchronizationmechanisms such as semaphores to maintain data consistency
when multiple processes access shared memory.
2.2.5 Disconnect and release memory
- Procedure: When processes are no longer needed, they must disconnectfrom
the shared memory using a function like shmdt() on Unix/Linux or
UnmapViewOfFile() on Windows. When there are no more processes
connected to the memory, you can free the memory using functions such as
shmctl() on Unix/Linux or CloseHandle() on Windows.
- Details: Disconnecting and releasing memory are crucial steps to
ensureefficient system resource management and avoid memory leaks.
This process clarifies the important steps in creating, using, and releasing
shared memory, emphasizing the significance of access management to ensure
data consistency in a multi-process or multi-threaded environment.
2.3 Advantages and disadvantages of shared memory
2.3.1 Advantages of Shared Memory High Performance
Shared memory allows processes or threads to directly access the same memory area,
eliminating the need to copy data. This leads to high performance because there is no
need to transfer data between processes.




