














Preview text:
IDEA GROUP PUBLISHING
701 E. Chocolate Avenue, Hershey PA 17033-1240, USA 16#$$!
Tel: 717/533-8845; Fax 717/533-8661; URL-http://www.idea-group.com Managing Information Copyright Idea Group Inc. Security on a Shoestring Budget Varadharajan Sridhar
Indian Institute of Management, Lucknow, India Bharat Bhasker
Indian Institute of Management, Lucknow, India EXECUTIVE SUMMARY CoApyright Idea Group Inc.
s organizations continue to deploy mission-critical, network-centric information
systems, managing the security of such systems has become very critical. Building and
managing such security infrastructure can be potentially very expensive, especially for small
and medium-sized organizations. The Indian Institute of Management, Lucknow (IIML), the
premier teaching and research business school in India, embarked on implementing a robust
security management infrastructure with a limited budget on hand. The case examines how
IIML successfully implemented the security infrastructure by appropriately developing
security policies and selecting a proper combination of freeware and proprietary software
components. Since security management is not a one-time activity and uses intensive
technology, a careful analysis is required to assess whether the maintenance of the security infrastructure can be C don o e in p -ho yright Idea Group Inc.
use or outsourced. The case illustrates the trade-offs
involved and presents experiences of IIML in outsourcing the post-implementation phase
to a Security Service Provider. The case also highlights the challenges organizations face
while implementing freeware security products and outsourcing security services. BACKGROUND
The Indian Institute of Management Lucknow (IIML) is one of the six national level
management institutes set up by the Government of India at Lucknow, India, in 1984. The
Institute’s mission is to help improve the management of the corporate and the non-corporate
sectors and also the public systems in the country, through pursuit of excellence in
management education, research, consultancy, and training. In order to fulfill its objectives,
the Institute undertakes a diverse range of academic and professional activities. C This o cha p pter ayright Idea Group Inc.
ppears in the book, Annals of Cases on Information Technology, Volume 5, edited by Mehdi
Kosrow-Pour. Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms
without written permission of Idea Group Inc. is prohibited. 152 Sridhar & Bhasker
IIML has a large Information Technology (IT) infrastructure and has an annual budget
of about 10 million Indian Rupees (INR) (equivalent to about $200,000) allocated in recent
years for the development of information technology resources. The details of the annual
budget allocated for the computer services of IIML for the year 2001-2002 is given in Appendix
A. Students, faculty, and staff of IIML use Internet resources quite extensively for teaching,
research, consulting, and administrative activities. The IT infrastructure of the Institute is
distributed across the sprawling 20-acre campus. There are about 400 client machines, about
10 high-end servers running various operating systems, applications, and services, catering
to the needs of students, faculty, and staff of the Institute. There are about 600 users on the campus.
The Computer Center (CC) at the Institute is responsible for all IT services on the campus
and maintains 24-hour computer labs housing about 200 machines for the students, and also
hosts the servers and networking equipment. The Computer Center employs one Manager and six systeC ms a o nd pyright Idea Group Inc.
programmer analysts who are involved in the maintenance of IT services
of the Institute. Most of the Computer Center staff has been with IIML since the Institute
started Computer Center operations in 1986. Even though some of the Center’s staff do not
have academic and professional qualifications in Computer Science or related disciplines,
they have acquired expertise in software development and networking through on-the-job training.
The IIML Web site (www.iiml.ac.in) is viewed by prospective students, researchers,
and scholars at various institutions and corporations around the world. The web site also
provides information to about 80,000 potential candidates who apply every year for the MBA
program offered by the Institute. Apart from the World Wide Web (WWW), email is another
Internet application that is widely used by faculty, students, and staff of the Institute. Email
communication by students and faculty spans geographical boundaries and is one of the
mission-critical Internet services of the Institute. The Institute Intranet is connected to the C Inteo rne p t viayright Idea Group Inc.
two Internet-access links. There is a plan to network all the student hostel rooms
and faculty residences in the coming academic year to provide campus-wide networking. This
will further increase the population of client machines by 500. The Institute also has plans
to offer distance education programs to corporate executives in the near future. SETTING THE STAGE In a recent securit C y sur o vey r p ep y ort r right Idea Group Inc.
eleased by Internet Security Systems (ISS, 2002), it
is reported that Internet risk was, in general, high in 2001 and is getting worse. ISS noted 830
million alarm events, and dealt with 2,185 security incidents in 2001 alone. ISS also points out
that 70% of the security attacks happened through the widely used WWW services. IIML
was also one of the thousands of affected organizations. The IIML web site was defaced a
number of times between May and August 2001, and a large number of man-hours was spent
to restore the damaged web pages. A spate of virus attacks caused considerable damage
leading to data loss, increased clean-up costs, and a subsequent drop in productivity levels
of the users. These attacks impacted the normal function of the users and caused considerable
drain of computer center resources. IIML had installed simple security services that could
not prevent the above-mentioned security intrusions. To address the above-mentioned
security threats, a three-member security planning team was formed in August 2001. The team,
including Mr. Mohapatra, the Computer Center Manager, set out to prepare a framework for
the implementation of a comprehensive information security management system for IIML.
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written
permission of Idea Group Inc. is prohibited. Copyright Idea Group Inc.
Managing Information Security 153
Despite the importance of information security, it is reported in Dinnie (1999) that 45%
of companies worldwide made no allowance in their budget for information security and 41%
had no budget for maintenance. It is not surprising that only $20,000, a mere 10% of the annual
budget of IIML, was allocated for information security management. The challenge was to
minimize the security threats by implementing appropriate security components within the
allocated budget. Moreover, since security management is an ongoing activity, Mr. Mohapatra
also had to decide about the strategies for the continuous maintenance of the deployed infrastructure. C C
AS opyright Idea Group Inc. E DESCRIPTION
According to von Solms, von Solms, and Caelli (1994),
The goal of Information Security Management (ISM) is to lessen either
the probability that something undesirable will happen (or the frequency
with which it is known to be happening) or the severity of the consequences
when it does happen, or both (p. 143).
The operational environment of an organization is the total set of information services
needed and responsible for storing, producing, and distributing information throughout the
organization (von Solms et al., 1994). Information Security Management is an effort to provide
an optimal level of security for the organization’s operational environment. The main elements
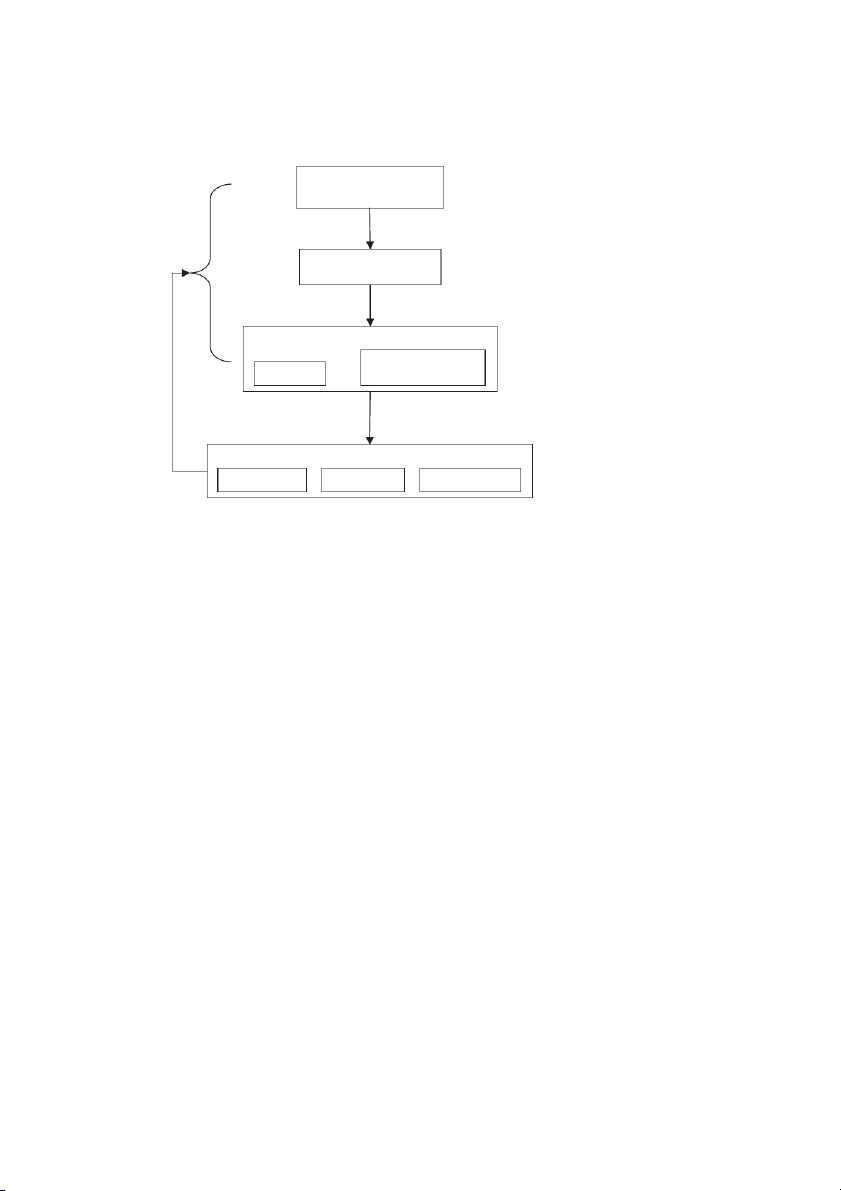
in ISM are given in Figure 1. An optimal security level is determined by the trade-off between
cost and complexities of security measures against the risk, vulnerabilities, and the loss the
organization faces in the event of security breaches. Security risks arise because a security
attack can exploit vulnerabilities. Countermeasures reduce risk by lowering vulnerabilities, C but o ne p w o y nes right Idea Group Inc.
may appear, and hence the feedback loop shown in Figure 1, indicating
continuous refinement of security policies and procedures.
Risk Analysis and Security Policy Formulation
Risk analysis as noted in Figure 1 is the first step in any security deployment exercise.
Risk is realized when a threat takes advantage of vulnerability to cause harm to the
organizational information resources. There are more than 70 risk analysis methods, including
the widely used tool CRAMM, (United Kingdom Central Computer and Telecommunications
Agency’s Risk Analysis and Management Method) available for organizations to conduct
security risk analysis (Spinellis, Kokolakis, & Gritzalis, 1999). The security management team did a risk profile analys C is baso ed p on t y he ri right Idea Group Inc.
sk profile matrix given in Guttman and Bagwill (1997).
Based on the risk analysis, a security policy document had to be formulated that defined
the threats and risks of the information resources within IIML and the procedures and
mechanisms for preventing or recovering from any such threats. The key trade-offs while
formulating the security policy guidelines are: (1) services offered versus security provided,
(2) ease of use versus security, and (3) cost of security versus risk of loss (Fraser, 1997). The
main purpose of an information security policy is to inform the users and staff of their
obligatory requirement to protect the information assets and resources of the organization.
As pointed out in Whiteman, Townsend and Aalberts (2001), a baseline security policy
consisting of a minimal set of guidelines was first developed and circulated among the users
to get feedback and suggestions. A security policy document covers areas such as
identification and authorization control, incident handling, Internet usage, firewall policies
and administration, electronic mail usage, and WWW usage (refer to Guttman & Bagwill, 1997,
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written Copyright Idea Group Inc.
permission of Idea Group Inc. is prohibited. 154 Sridhar & Bhasker
Figure 1. The Main Elements in Information Security Management Copyright Idea Group Inc. Copyright Idea Group Inc. Copyright Idea Group Inc.
for a comprehensive guide on security policy formulation). IIML wanted to provide many
different services both for internal users and to the outside, each of which required different
levels of access needs and models of trust. A comprehensive list of services were compiled
by the security team as given in Fraser (1997), and the corresponding access-control
guidelines were developed. As given in Abrams and Bailey (1995), policy can be expressed
in three different forms: natural language statements, mathematical, or non-mathematical
formal statements. The security policy document for IIML was prepared using a combination
of natural language statements and formal expressions. Mathematical statements, while
reducing ambiguity to a minimum, are not understood by the heterogeneous user community,
and hence were not adopted. To minimize the ambiguity in natural statements, a non-
mathematical but constrained and more precise form of the policy construct is also incorpo-
rated. A sample policy statement in both forms is given in Appendix B. This methodology
helped the security team to effectively disseminate the policies to the user community and
define precise benchmarks for the security infrastructure implementation phase.
Selection of the Security Components
There are various components in an information security infrastructure, such as the
firewall, intrusion detection system, virus protection system, and content inspection systems
(refer to McBride, Patilla, Robinson, Thermos, & Moser, 2000, for a comprehensive descrip-
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written
permission of Idea Group Inc. is prohibited. Copyright Idea Group Inc.
Managing Information Security 155
tion of security components). The firewall is a single network access point between the
organization network and the external networks. The organizational information resources
are protected by the firewall. Firewall solutions can be as simple as installing the latest version
of the operating systems on the public servers of the network, and harden the operating
system to reduce vulnerabilities. On the higher end, there is the commercial product by
Checkpoint that integrates all security functions, costing about $3,000 for a 25-user license.
But a firewall alone cannot prevent all security threats. Although firewalls remain critical front-
line defensive equipment, other security components are also needed to guard against the e C volvi Th o ng intr e se p usi con y ons r (ISiSg , 20 h 02). t Idea Group Inc.
d most important component in a security infrastructure is an Intrusion
Detection System (IDS), which is extremely effective in identifying intruders (ISS, 2002). An
IDS uses techniques such as pattern matching, expression matching, or byte-code matching
to detect any intrusions. Once a possible intrusion is discovered, the IDS will take action
ranging from sending an alert to the console of the security administrator to initiating a close
to the intruder’s network connection. An Intrusion Detection System such as Real Secure
from Internet Security Systems costs about $10,000 to $20,000. Freeware products such as Snort are also available.
With the ever-increasing virus attacks, an active virus protection system that detects
virus patterns and cleans the files and email messages before they enter the internal network
servers is very much essential. A content management system scans the messages for
obnoxious and offensive content and filters the messages and sends notifications to the
senders. The content management system also improves network and server performance by
filtering unsolicited mail messages and blocking spamming. Virus protection systems and
content management systems such as Trend Micro Interscan eManager is priced at about C $6, o 000 p for yright Idea Group Inc. a 300-user license.
Additionally, there may be upgrades required for the network devices such as switches
and routers to incorporate network security features. In effect, the bill for setting up the
security infrastructure could run as high as $60,000 to $200,000, depending upon the size of
the information technology infrastructure of the organization. Apart from the hardware and
software, trained manpower is needed to install, configure, and manage the security
infrastructure. In practical terms, a dynamic proactive defense that combines firewall,
intrusion detection, antivirus, and content management, coupled with strong policies and
procedures and a strict regime for software updates and security patching is very much
required for an effective security infrastructure. The various security components along with the required character C isticso as p defi y nedright Idea Group Inc.
by the security team are enclosed in Appendix C.
Comprehensive information security management is a big budget item, and with the
awareness of security management still in the nascent stage in India, organizations think twice
before embarking on such a project. With a given budget constraint and other limitations,
organizations should choose a suitable combination of the various security components that
are compatible with the assessed risk level and the defined security policies of the organi- zation.
One way to reduce the infrastructure cost is to look at Open-source software (OSS),
which is available free or at minimal price. The term “open source” refers to the code that is
open to the public (refer to Swift, 2001, for a comprehensive guide on OSS). The open source
technologies may not provide a comprehensive security solution, but help to reduce the total
cost of ownership, and can fit in to the organization’s security infrastructure at a very low
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written Copyright Idea Group Inc.
permission of Idea Group Inc. is prohibited. 156 Sridhar & Bhasker
price compared to proprietary components. The main disadvantage of open-source software
is lack of support and scalability. It has been noted that OSS is used mainly in smaller
organizations that do not have many mission-critical applications (Gill, 2002). Most of the free
software also relies on security experts for installation and configuration. Though OSS
provides source code, it is practically impossible for a non-expert to fix any problems. On the
other hand, OSS advocates argue that minimal changes in the requirements are easy to make,
as the open source community consisting of millions of programmers around the world
constantly work on patches, bug fixes, and customized modifications of the software (Gill,
2002). Documentation for OSS is minimal, and it is not user friendly. Compared to OSS, the
commercial software, such as Checkpoint Firewall, comes with the support of a wide array
of hardware and software and has experts trained in the configuration. Under GNU public
license (FSF, 2002), freeware comes with no warranty. But, Checkpoint gives a warranty for
its product. Copyright Idea Group Inc.
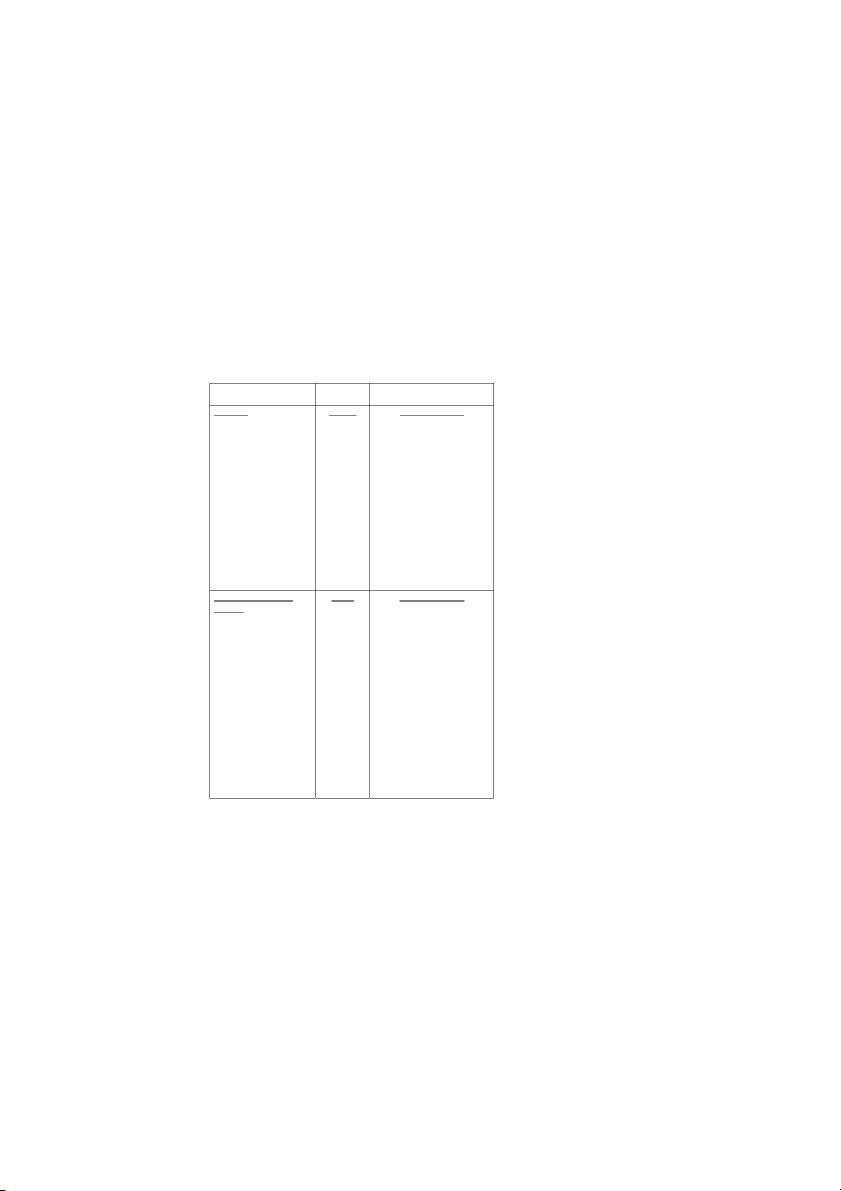
Table 1. Comparison of OSS and Proprietary Security Products Security OSS Proprietary Product Component/Metric Product Firewall Astero Checkpoint NG 1. Centralized Management Yes Yes 2. Single point access (network address translation and masquerading) Yes Yes 3. Strong access control and authentication Yes Yes Copyright Idea Group Inc. 4. Built-in proxy serve r with authentication No Yes 5. Hardware/software platform support Limited Comprehensive 6. License GNU Proprietary 7. Price Freeware $10,000 (INR 5,00,000) for 250 use license Intrusion Detection Snort ISS Real Secure System 1. Server iC
ntrusi opyright Idea Group Inc. on monitoring Yes Yes 2. Priority based alerts Yes Yes 3. Centralized management Yes Yes 4. Automatic signature updates Yes Yes 5. Network intrusion detection Yes Yes 6. Hardware/software platform support Limited Comprehensive 7. License GNU Proprietary 8. Price Freeware $8,000 (INR 4,00,000) for one network sensor plus $2,000 (INR 1,00,000) for software subscription services
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written
permission of Idea Group Inc. is prohibited. Copyright Idea Group Inc.
Managing Information Security 157
The alternatives before the security team were (1) select OSS components, (2) select
proprietary components, and (3) select a combination of OSS and proprietary components.
The selection depends on factors such as functionality, flexibility of the product, robustness,
product support, ease of use, and finally, the cost. Based on the desired characteristics
outlined in Appendix C and the initial bids received from the vendors, the comparison chart shown in Table 1 was prepared.
The above table indicates that the OSS products satisfy all the desired characteristics
as outlined by the security team. However, the hardware/software platform support was lim C ited i o n th p e ca y se r of i O g SS h prod t u Idea Group Inc.
cts compared to the proprietary products. The cost of the
proprietary products is much more than the allocated budget. The decision was clearly in
favor of OSS products, especially because of the cost savings, although the security
management team was aware of the limitations of OSS products as outlined above. For virus
protection and content management, all the bids were for Trend Micro’s Interscan VirusWall
and eManager, respectively. These are proprietary products and no equivalent OSS products
were available. Since the selected OSS products lack proper documentation and hence require
expertise for installation, it was decided to outsource the installation and configuration to
Bangalore Labs, a Security Service Provider (SSP). The implementation costs, as given below
in Table 2, were well within the budget.
Implementation of the Information Security Architecture
Security consultants from Bangalore Labs installed and configured the firewall and IDS
components as per the security policy. All the email messages from within and from outside
the campus network are first scanned by the Interscan VirusWall before being delivered to C the o mai p l y boxes. right Idea Group Inc.
This prevents virus-laden mail messages from ever reaching the user mailboxes
and hence reduced the virus threats noticed earlier. The VirusWall was configured to get the
updated signature files from the vendor Trend Micro (www.anitivirus.com) site every 24
hours to keep up with new virus and worms. Within minutes after completing the installation,
the benefits of the security infrastructure were evident when the IDS alerted the system
administrator of Code Red virus intrusions, and the VirusWall filtered them.
There are other complexities as the IIML network is connected to two Internet Service
Providers. IIML wanted to route the traffic through both the links so that load balancing would
be achieved. To do this, the SSP implemented a “policy based routing,” so that all Web traffic
is directed through a high-capacity Internet access link, and email and other traffic is routed
through the low-bandwidth access link. These were the additional value-added services that Copyright Idea Group Inc.
Table 2. Cost of the Security Infrastructure Implementation at IIML Activity Cost
1. Trend Micro Interscan VirusWall and
eManager @ $18.1 for 300 users $5,430 (INR 271,500)
2. Installation and configuration of Astero
Firewall, Snort IDS, Squid Proxy, Trend $7,400 (INR 370,000)
Micro Interscan VirusWall and Trend Micro Interscan eManager
Total Cost of the Project $ 12,830(INR 641,500)
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written Copyright Idea Group Inc.
permission of Idea Group Inc. is prohibited. 158 Sridhar & Bhasker
the SSP provided to IIML in addition to installing and configuring the security components.
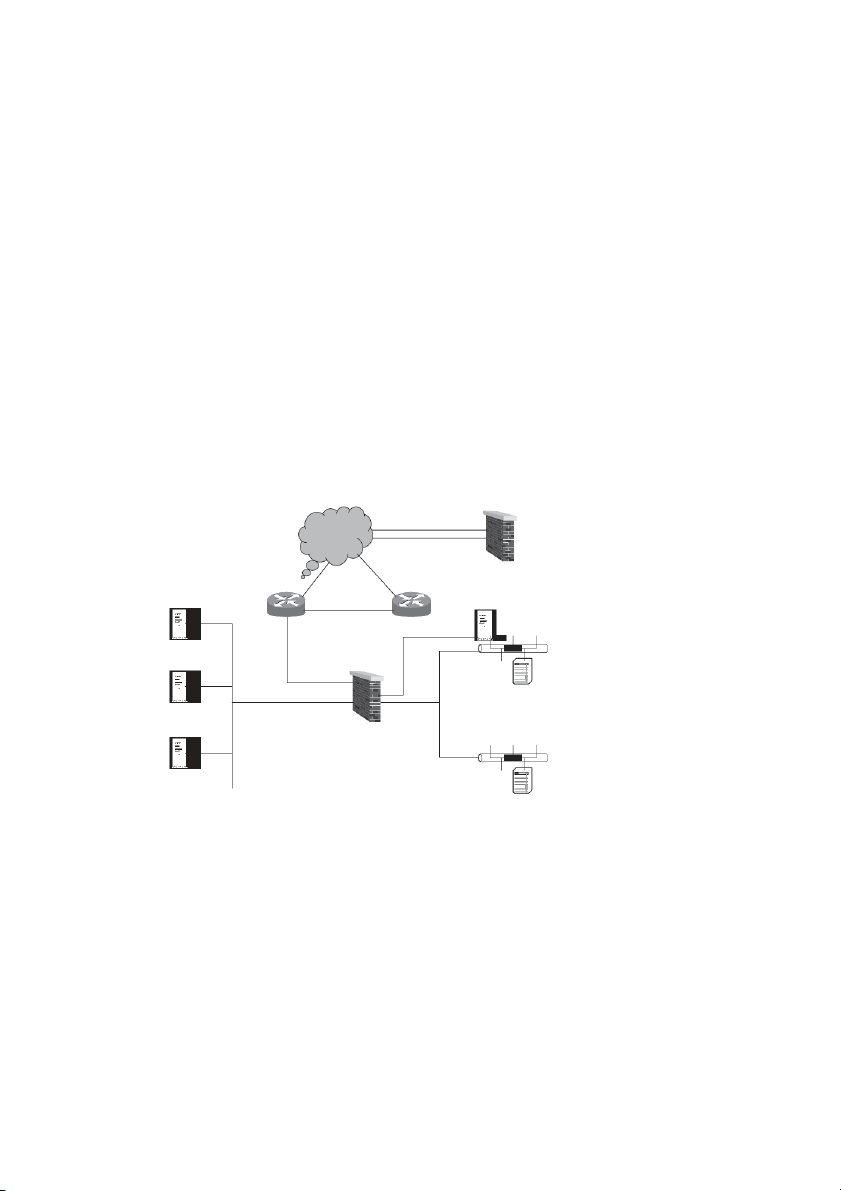
The architecture of the IIML network is given in Figure 2. The whole project took about three
weeks. The project plan and the rollout of the different services are shown in Appendix D.
Outsourcing Maintenance of the Security Infrastructure
After the successful implementation of the recommended security control, it is impor-
tant that operational and administrative procedures are developed to support and enforce
the security controls. To enforce the continuous, effective functioning of the security
controls, it is very important that the controls are also effectively maintained and monitored
(von Solms, 1998). Security management is not a one-time activity, and as new vulnerabilities
are exposed through penetration testing, patches, and configuration, changes are required
for the security components on a continuous basis which act as a feedback mechanism, as given in Fig C ure 1 o . It hp as y bee right Idea Group Inc.
n reported in Weissman (1995) that periodic penetration testing,
which is a form of stress testing that exposes security weaknesses, is a must for high-rated
security systems. ISS (2002) reports that even though vulnerability assessment is a very
important proactive measure, many organizations do not have the staff, resources, or
processes to develop institutionalized standards for routine scans and remediation.
Whether to do the maintenance of the security infrastructure using in-house expertise
or to outsource it to a service provider is a dilemma that haunts security administrators. The
primary motive for considering outsourcing is that long-term outsourcing contracts tend to
convert variable costs into fixed costs and thus make technology spending more predictable
(Alner, 2001). Security management involves intensive technologies and requires highly
Figure 2. Information Security Architecture at IIML Copyright Idea Group Inc. Copyright Idea G oup Inc. Ethern t e Ethern t e
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written
permission of Idea Group Inc. is prohibited. Copyright Idea Group Inc.
Managing Information Security 159
skilled and trained security specialists. The organization must recruit, train, and retain
employees with unique skills to provide maintenance of the security systems. With little
expertise available in this area, businesses can outsource the security management to SSPs
(Pereira, 2001). SSPs also have the advanced system and communication monitoring tools
and professionals trained in specific security technologies, and hence can guarantee service and system availability.
The security service provisioning industry is still evolving, even in the U.S. In India,
Bangalore Labs started this movement, followed by others. The parameters that organiza- tio C ns sh o ould p inv y esti r gaitg e be h fore t o Idea Group Inc.
utsourcing their security management services include:
technology of SSP to support the services, availability of key infrastructure such as Internet
connectivity and network operations centers, comprehensiveness of services offered, and
finally, the price and value of service offerings. Typical security services provided by SSPs
are included in Appendix E (Sridhar & Bhandari, 2002). Most of the maintenance can be done
by SSPs remotely from their Network Operations Centers (NOCs).
The IIML security team decided to outsource the maintenance activities because of the
above reasons. Service Level Agreements (SLAs) are critical in the outsourcing business
(Alner, 2001). The information security SLA should specify the services expected from the
outsourcer and indicate what functions will be retained by the client. SLAs and an Annual
Maintenance Contract were signed with Bangalore Labs, the cost details of which are given
below in Table 3. Bangalore Labs has a state-of-the-art Network Operations Centre (NOC)
at Bangalore. A Virtual Private Network (VPN) tunnel (refer to Stallings, 2000, for VPN
technology) was constructed between the IIML firewall and the firewall at Bangalore Labs
through which remote monitoring is done (refer to Figure 1). The first successful vulnerability
test post-implementation was done at the end of November 2001, and the firewall withstood C the o ri p gor ofyright Idea Group Inc. the test.
CURRENT CHALLENGES/PROBLEMS FACING THE ORGANIZATION
The deployment of IIML’s information security infrastructure was completed, and the
project completion was signed-off with Bangalore Labs on November 5, 2001. Problems
started surfacing at the end of December 2001. Performance of the firewall deteriorated, and
there were frequent network disconnects with the firewall server. Since all the internal and
external traffic was being routed through the firewall, the users started noticing an increase Table 3. Cost of the C
Annu opyright Idea Group Inc. al Maintenance Contract Activity Cost Annual Maintenance Contract
a. Vulnerability scanning at $176 per server, 3 times a year for 4 servers $2,112 (INR 105,600)
b. Vulnerability scanning at $526 per network device per year for 4 devices $2,104 (INR 105,200)
c. Firewall log analysis every 14 days at $100 for 26 fortnights $2,600 (INR 130,000)
Total Annual Maintenance Contract Cost $ 6816 (INR 340,800)
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written Copyright Idea Group Inc.
permission of Idea Group Inc. is prohibited. 160 Sridhar & Bhasker
in the Web traffic response time. Some users who used services such as remote login (Telnet)
to outside computer systems were not able to do so, because of the policies incorporated in
the firewall. Complaints started pouring in at the help desk of the Computer Center. Even
though the consultants at Bangalore Labs were in constant touch with the IIML Computer
Center and were coming up with some solutions, the problems persisted. At this stage, there
were the following three issues regarding the security infrastructure project that raised alarms for IIML: 1.
Would the OSS components withstand the rigor of the operational environment?
Would OSS really reduce the total cost of ownership? 2.
Does outsourcing security management lead to compromises? 3.
Has the deployment of the security infrastructure reduced the functionality of the services? Will OSS C Mee o
t thpyright Idea Group Inc.
e Functionality of the Operational Environment?
Repeated attempts by the security consultants at Bangalore Labs and the support team
at Astero, Germany, could not provide a permanent solution to the decreasing performance
and throughput of the Firewall. In early January 2002, Astero released the new version of its
Firewall, which had bug fixes for some of the problems, including the high swap usage problem experienced at the IIML site.
Open-source software movement believes in producing a product that can be tested by
millions around the world. There are user forums such as those available at www.snort.org,
where the worldwide user community shares its experiences and problems. Solutions for
trouble-shooting or enabling a new feature, which is not mentioned in the documentation,
can be found out through these forums almost instantaneously. However, since these are
technology intensive, it is normally impossible for non-experts to fix problems, as pointed out
in Gill (2002). Having the source code did not really help IIML, as the Computer Center staff C waso un pyright Idea Group Inc.
able to make changes to the code and patch up the bugs. They had to depend on SSP,
who in turn depended on the vendor and the user community to solve the problems. It took
time to find a solution, in contrast to what the advocates of OSS point out.
Even though Bangalore Labs sent the new version of the firewall to IIML under the
contract agreement without any additional fees, the trend in the freeware market throws up
uncertainties for IIML. The ideological purity of the open-source software business is being
diluted as start-ups build proprietary products on top of an open source solution. For example, Sistina, which developeC d an o op pyright Idea Group Inc.
en source file system that multiple computers can share,
changed course in August 2001, switched to a closed-source license for the newer versions
of its Global File System (Shankland, 2001). Shankland (2001) also points out that many other
companies have followed a similar path, becoming increasingly protective of their intellectual
property. Astero, which started improving the security features of Linux when it started the
product development on Astero Firewall, also has developed additional components that are
integrated into the firewall. The firewall code is supported under the GNU public license.
However, the Web interface for managing the firewall and other components, such as
“Up2Date” services, which provides updates on bug fixes and new releases, are not provided
as part of the licensing agreement. Astero charges about $4,000 for commercial use of its
Firewall software and an annual renewal fee of $1,000 for 500 active Internet Protocol (IP)
addresses. The migration of freeware software to commercial proprietary software will affect
the total cost of ownership of the security infrastructure of organizations, especially those
in developing countries that have limited budgets for security management.
Copyright © 2003, Idea Group Inc. Copying or distributing in print or electronic forms without written
permission of Idea Group Inc. is prohibited. Copyright Idea Group Inc.




