Report tài liệu
Chia sẻ tài liệu
Tóm tắt - Sơ đồ khối các hệ mật môn Lý thuyết mật mã | Trường Đại học Bách Khoa Hà Nội
Tóm tắt - Sơ đồ khối các hệ mật môn Lý thuyết mật mã. Tài liệu được sưu tầm gồm 25 trang, giúp các bạn ôn luyện và phục vụ cho việc học tập, đạt kết quả tốt. Mời các bạn đón xem!
Môn: Lý thuyết mật mã 19 tài liệu
Trường: Đại học Bách Khoa Hà Nội 5.5 K tài liệu
Tác giả:
Tài liệu khác của Đại học Bách Khoa Hà Nội
Preview text:
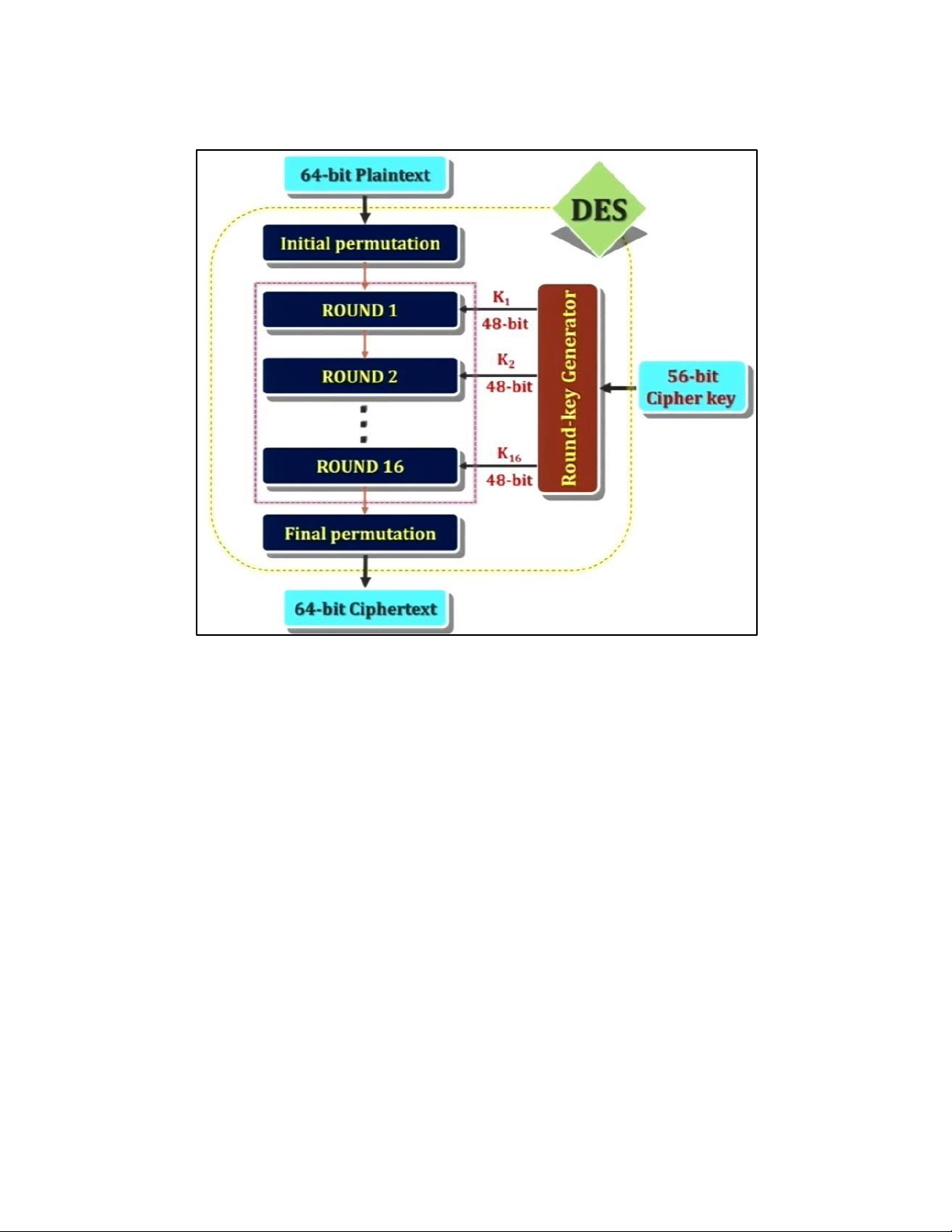
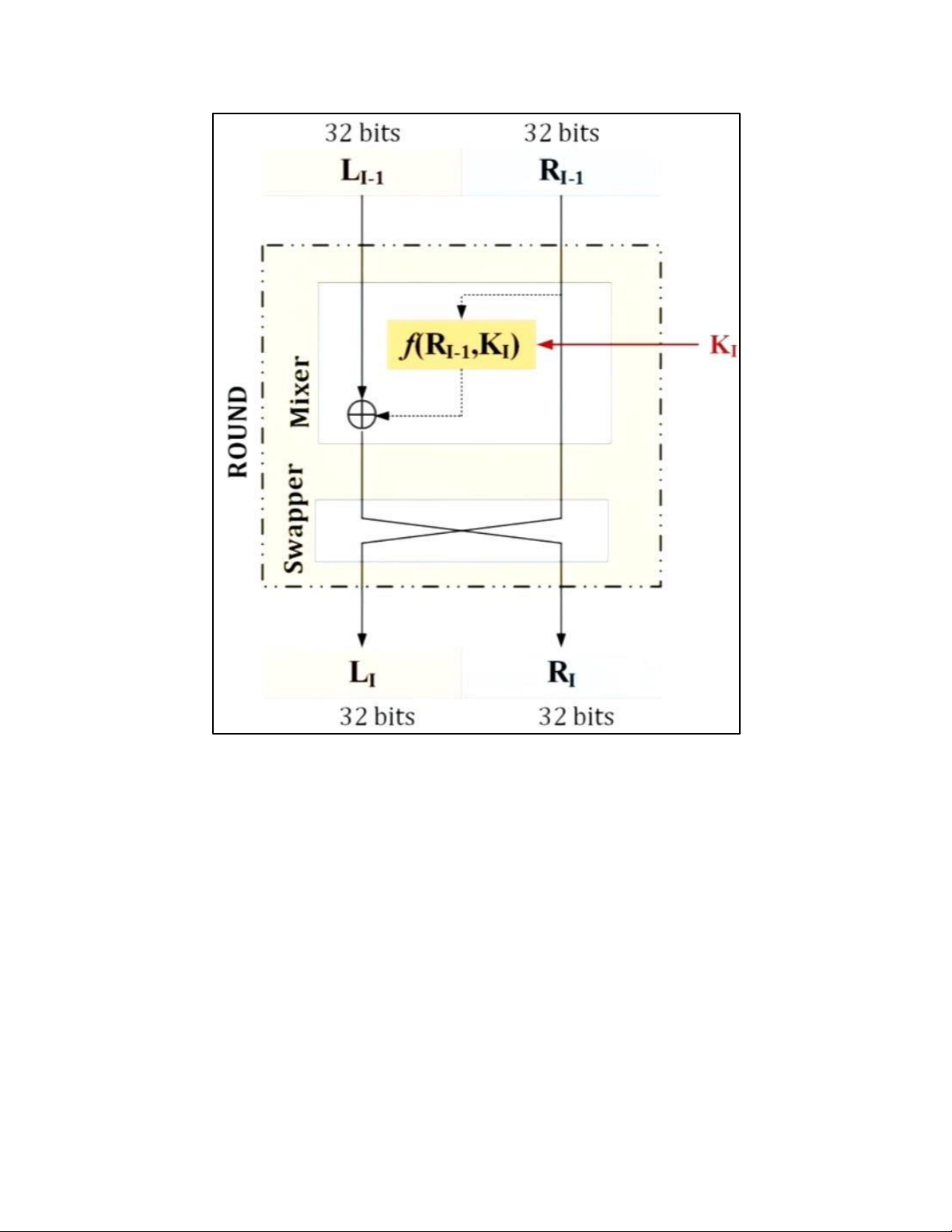
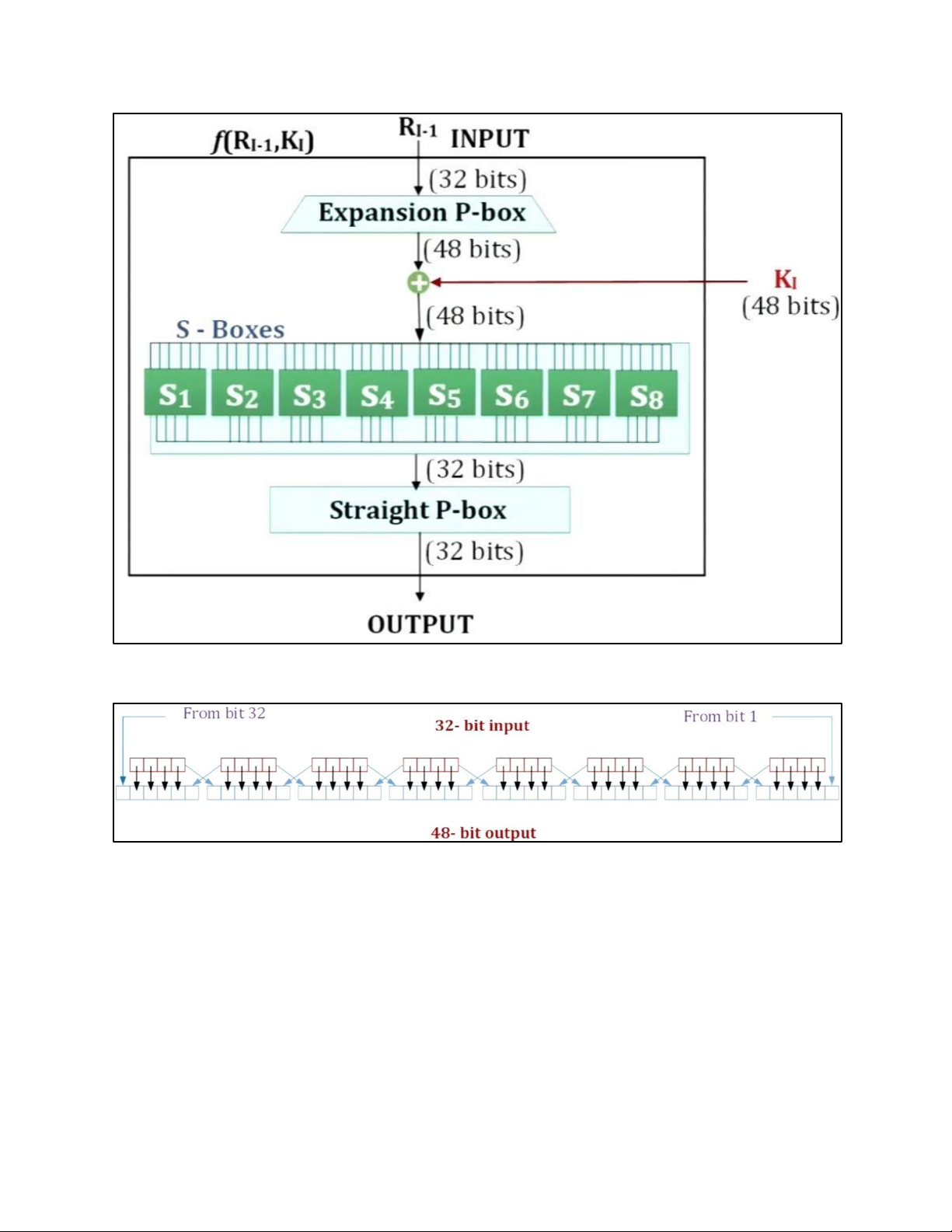
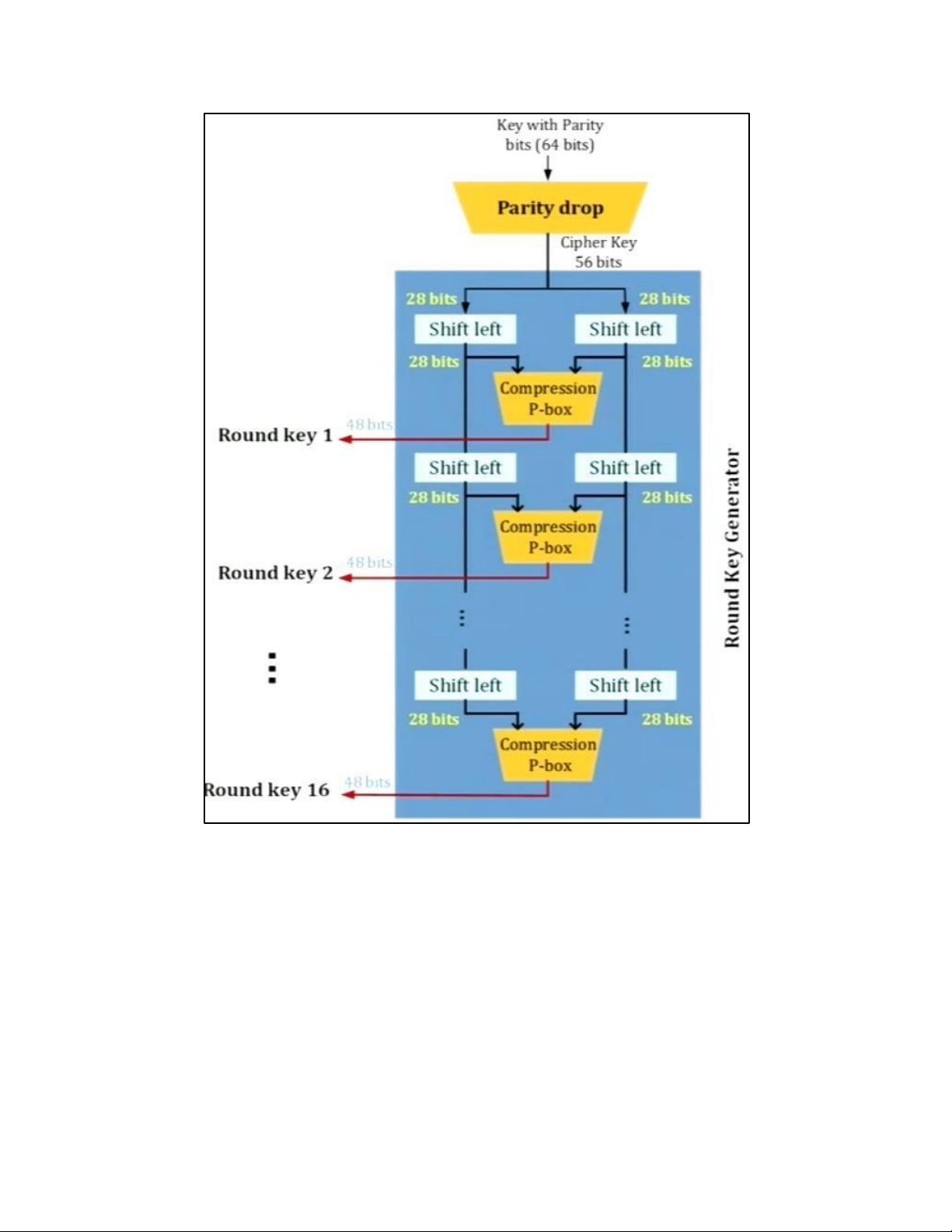
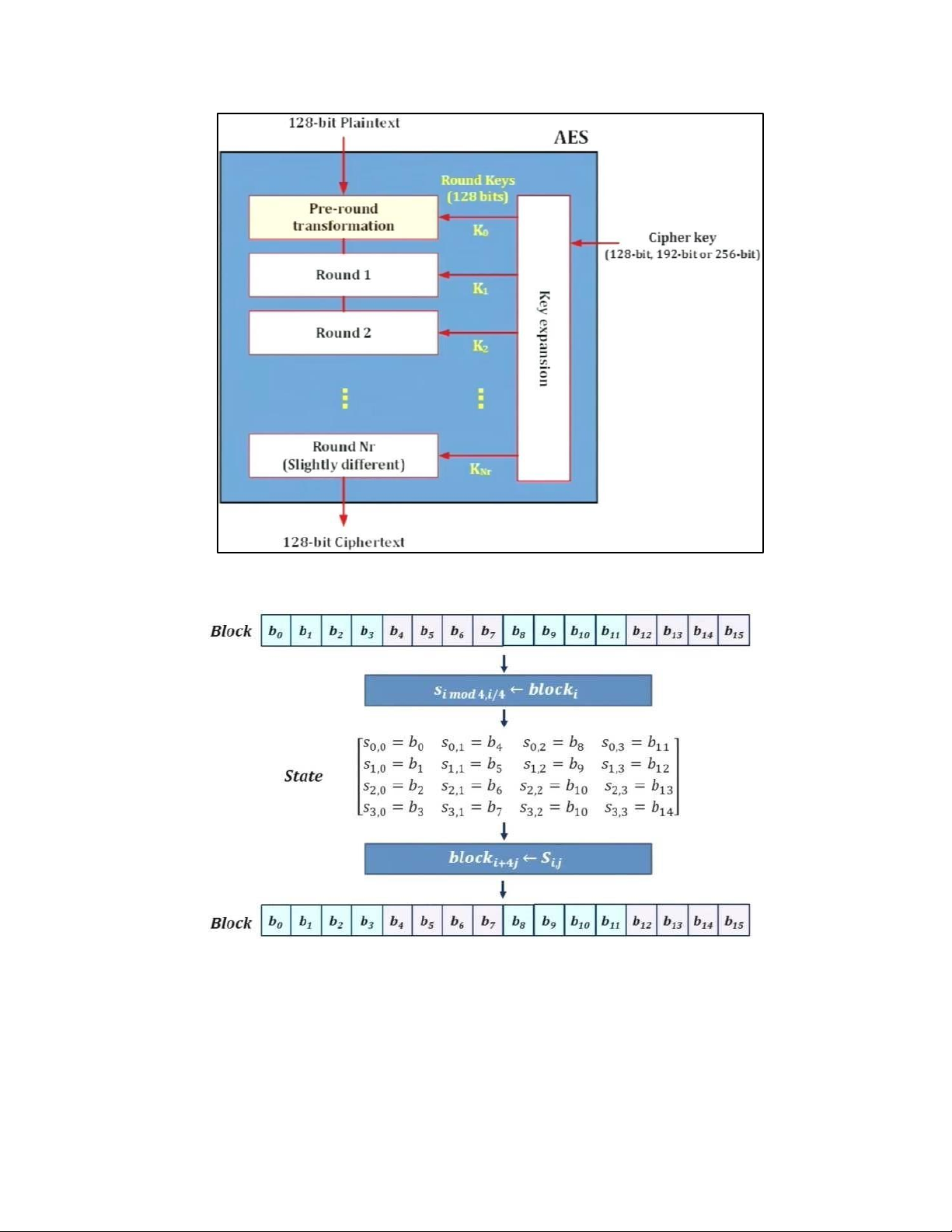
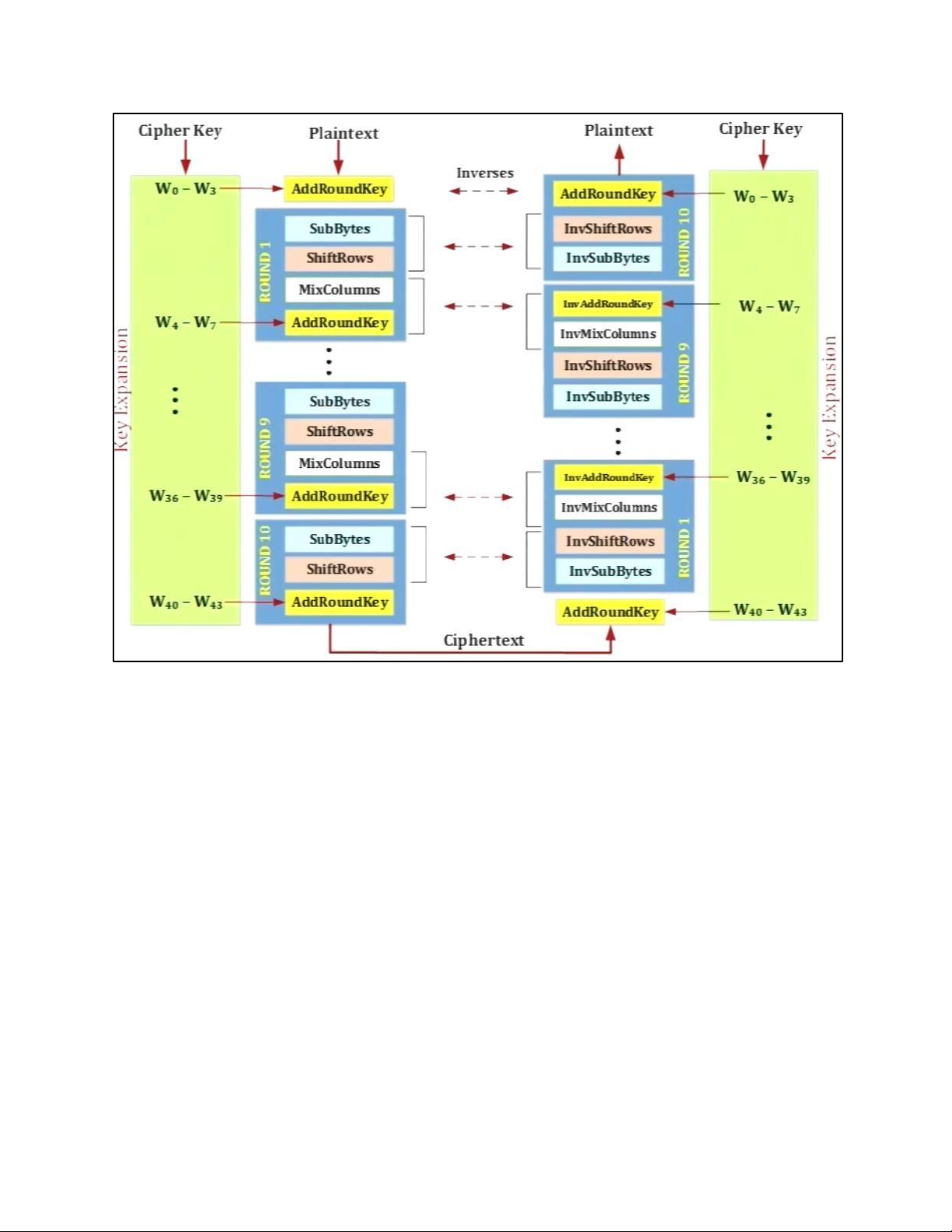
4. DES TẠI MỖI ROUND: H M DES: EXPANSION PBOX: KEY GENERATION: 5. AES 5.1 . AES CIPHER a. AES CIPHER ARCHITECTURE
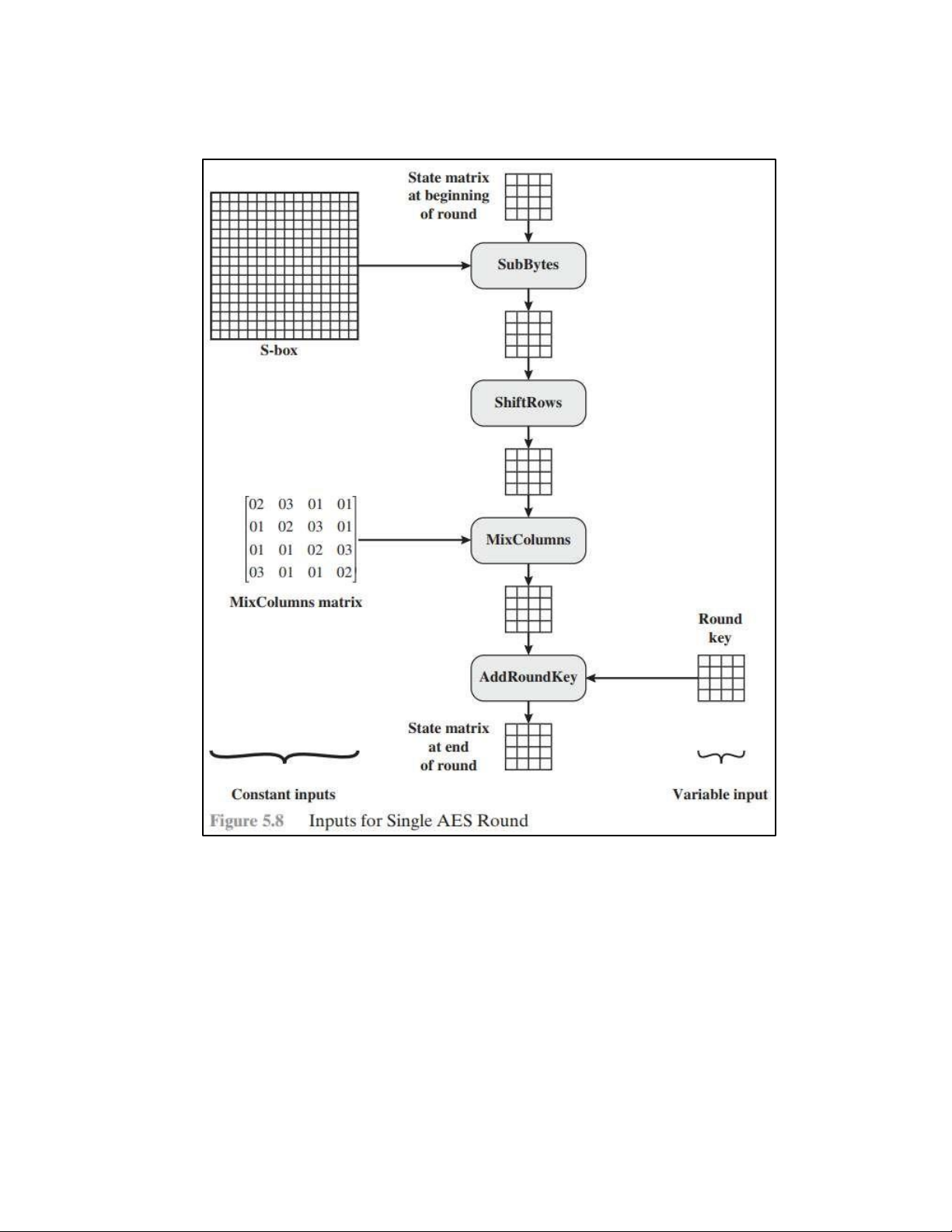
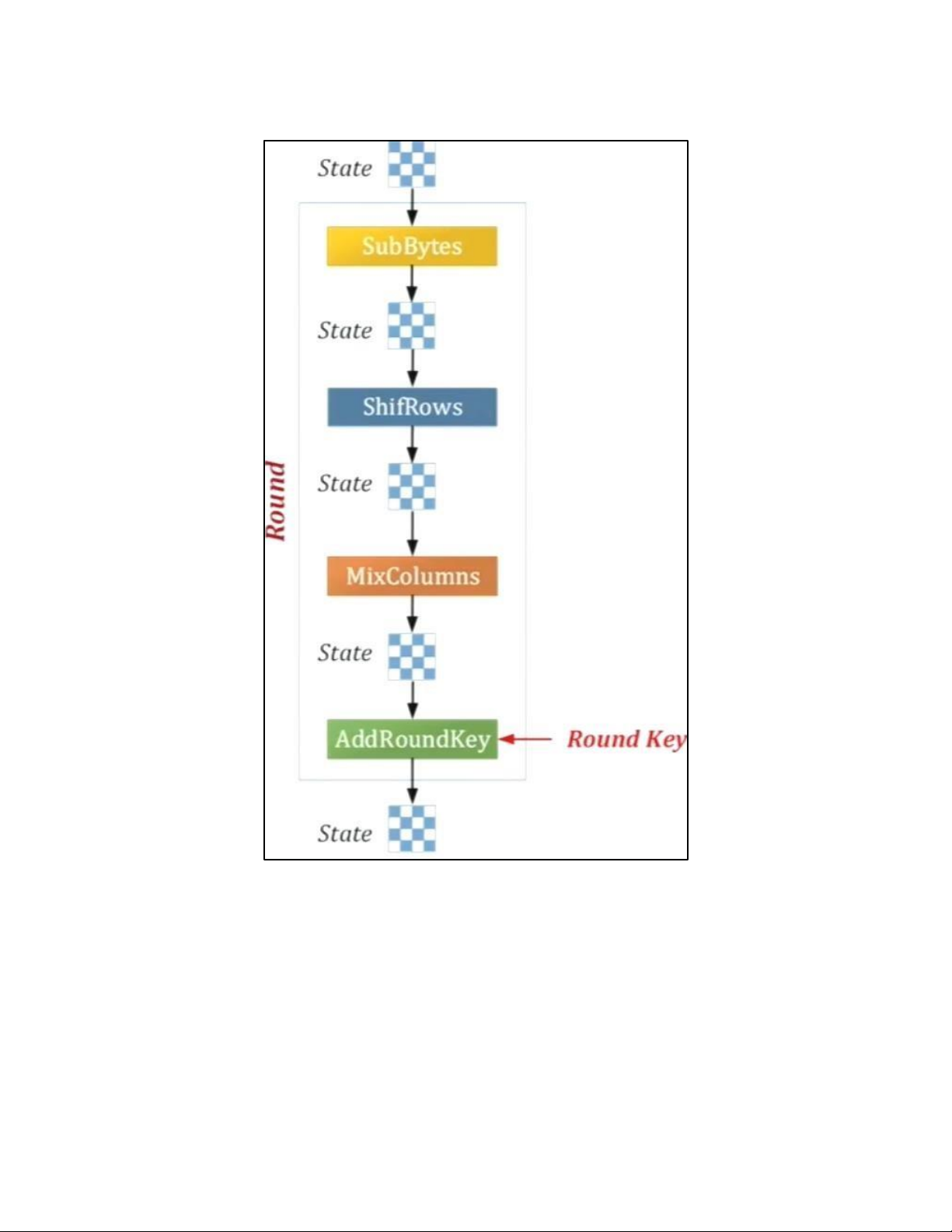
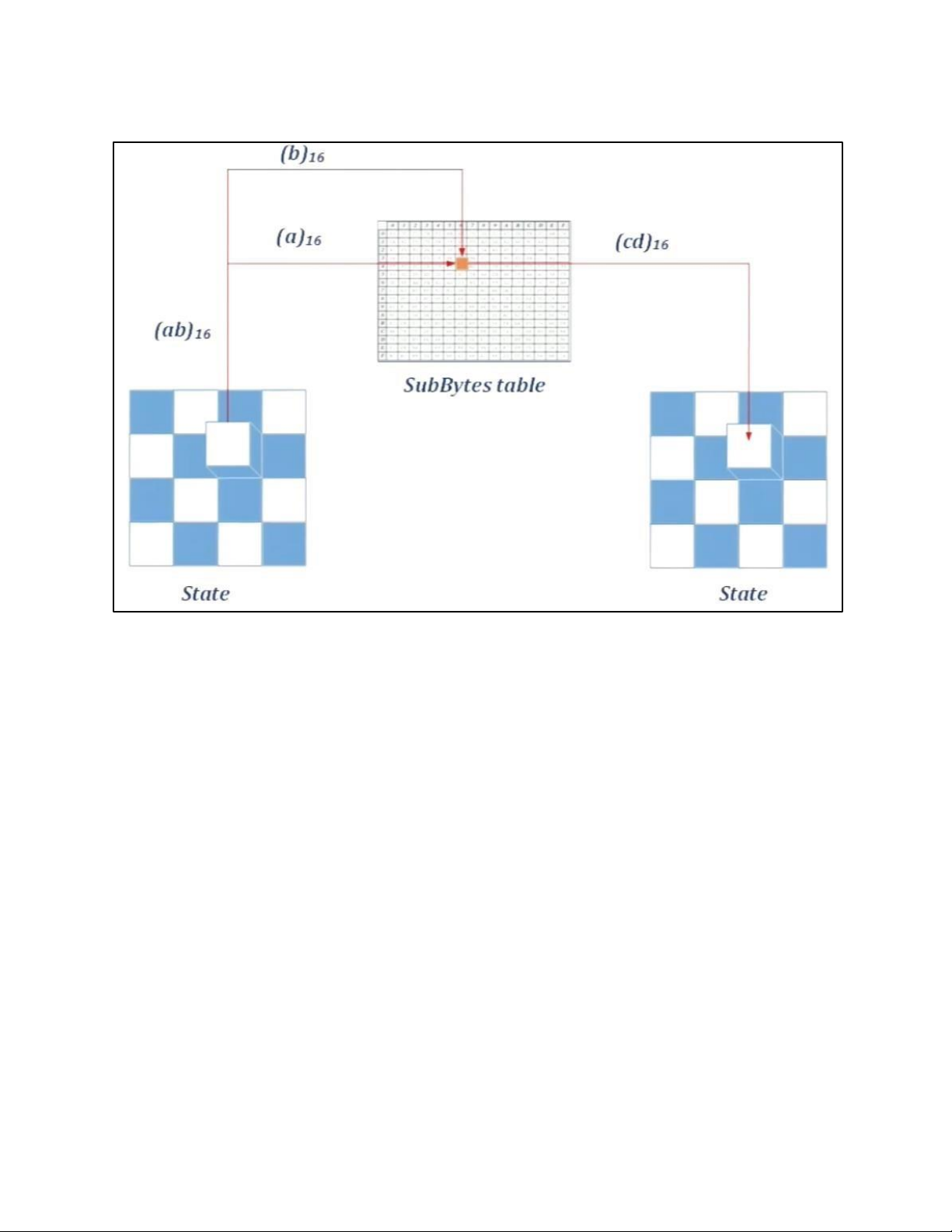
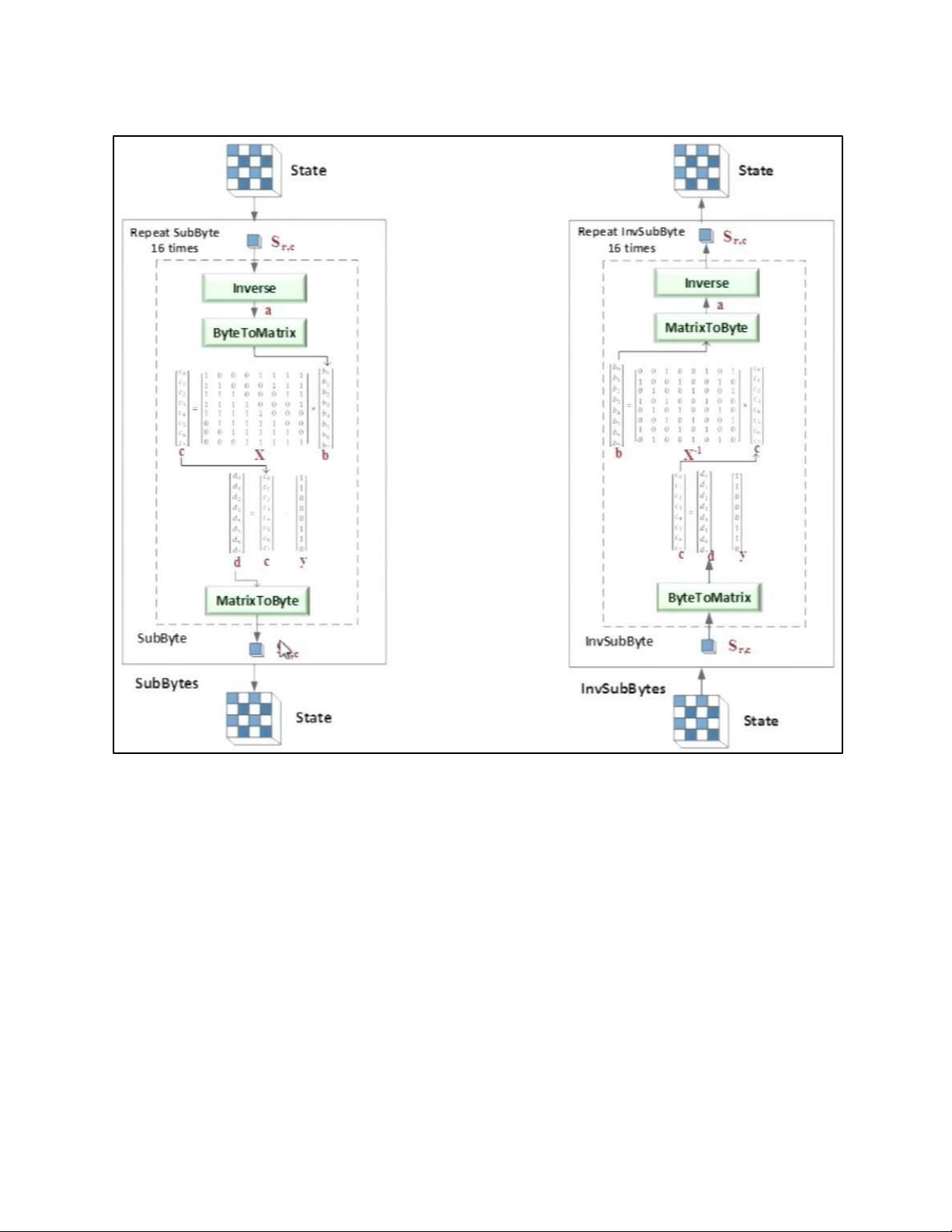
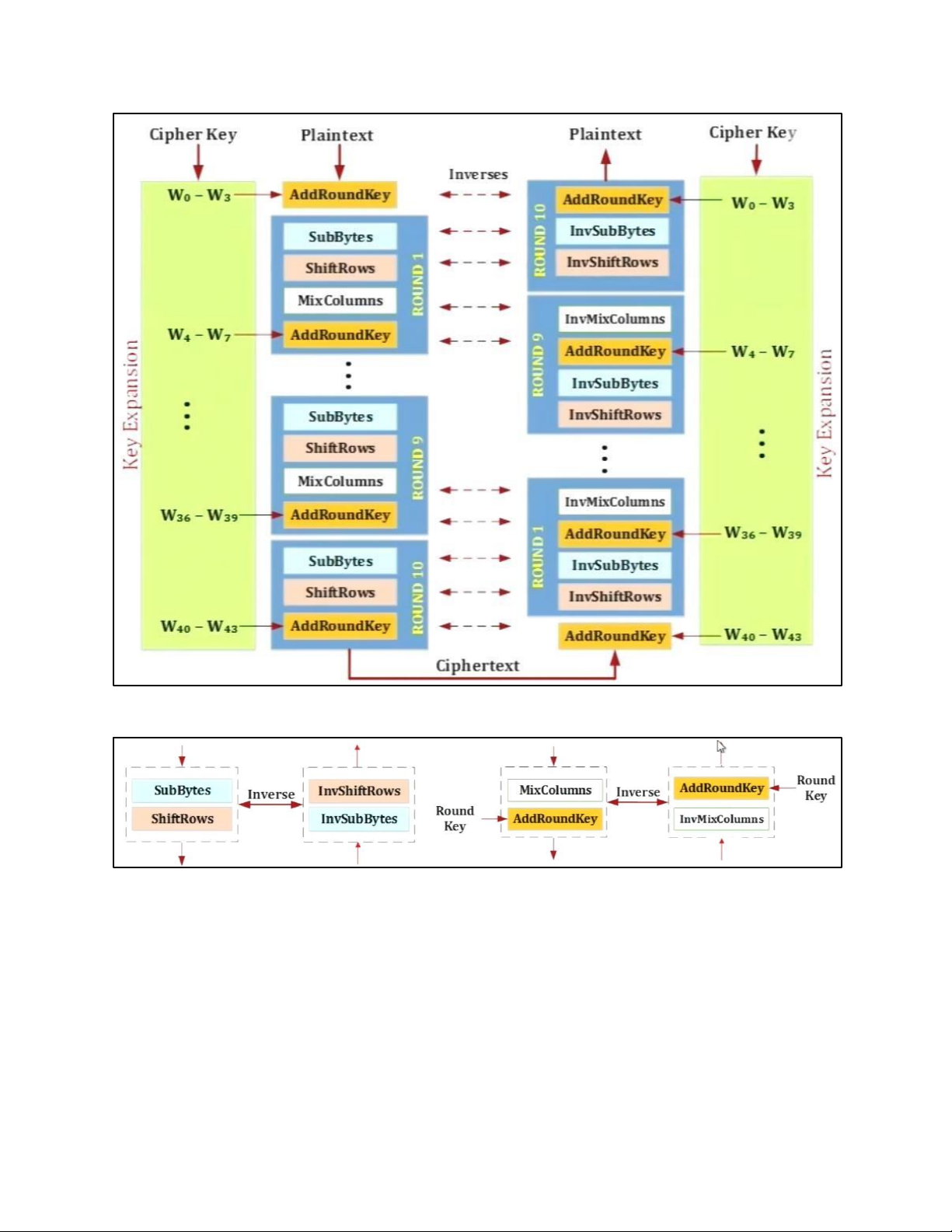
• BLOCK TO STATE AND STATE TO BLOCK TRANSFORMATION • STRUCTURE OF EACH ROUND b. AES PRINCIPLE • SUBSTITUTION - SUBBYTES
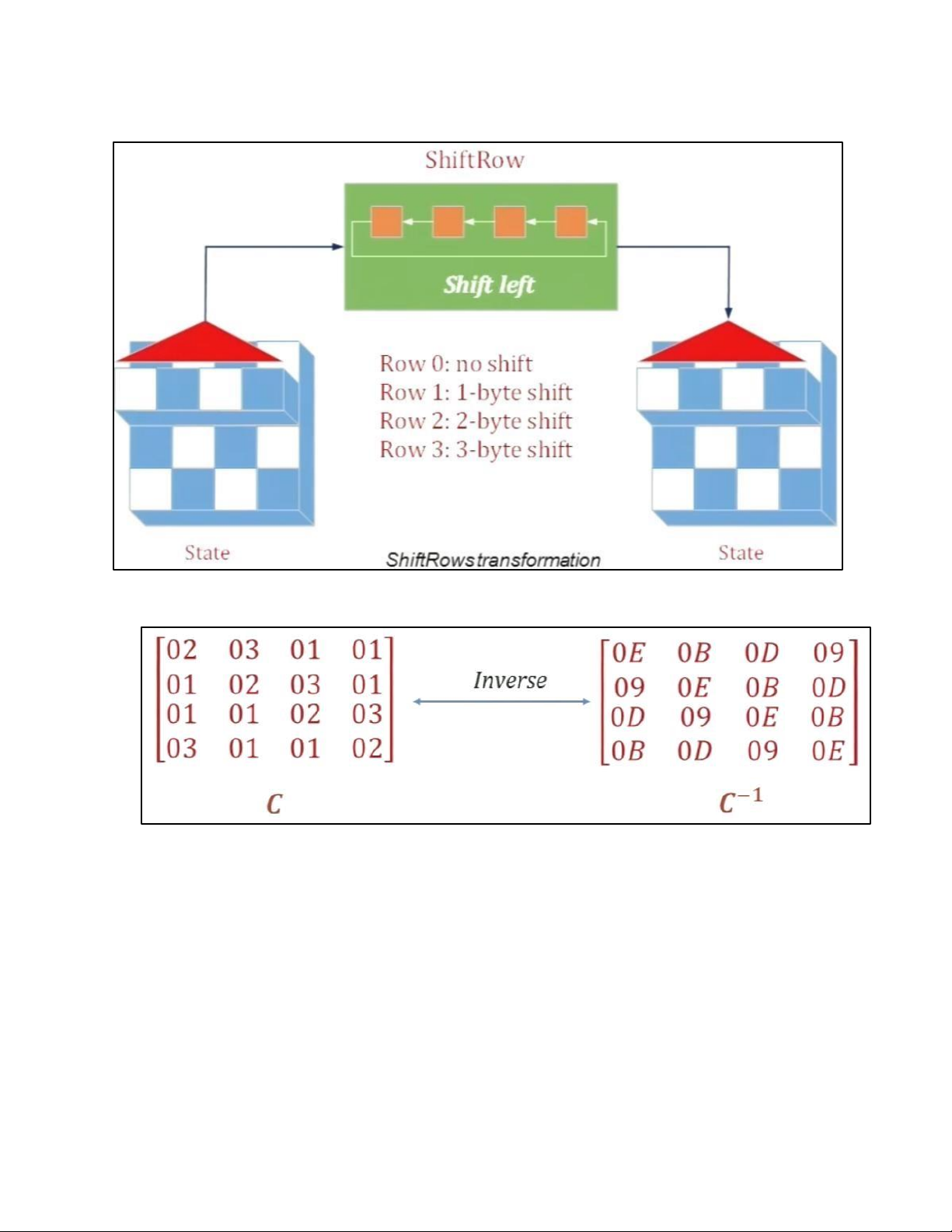
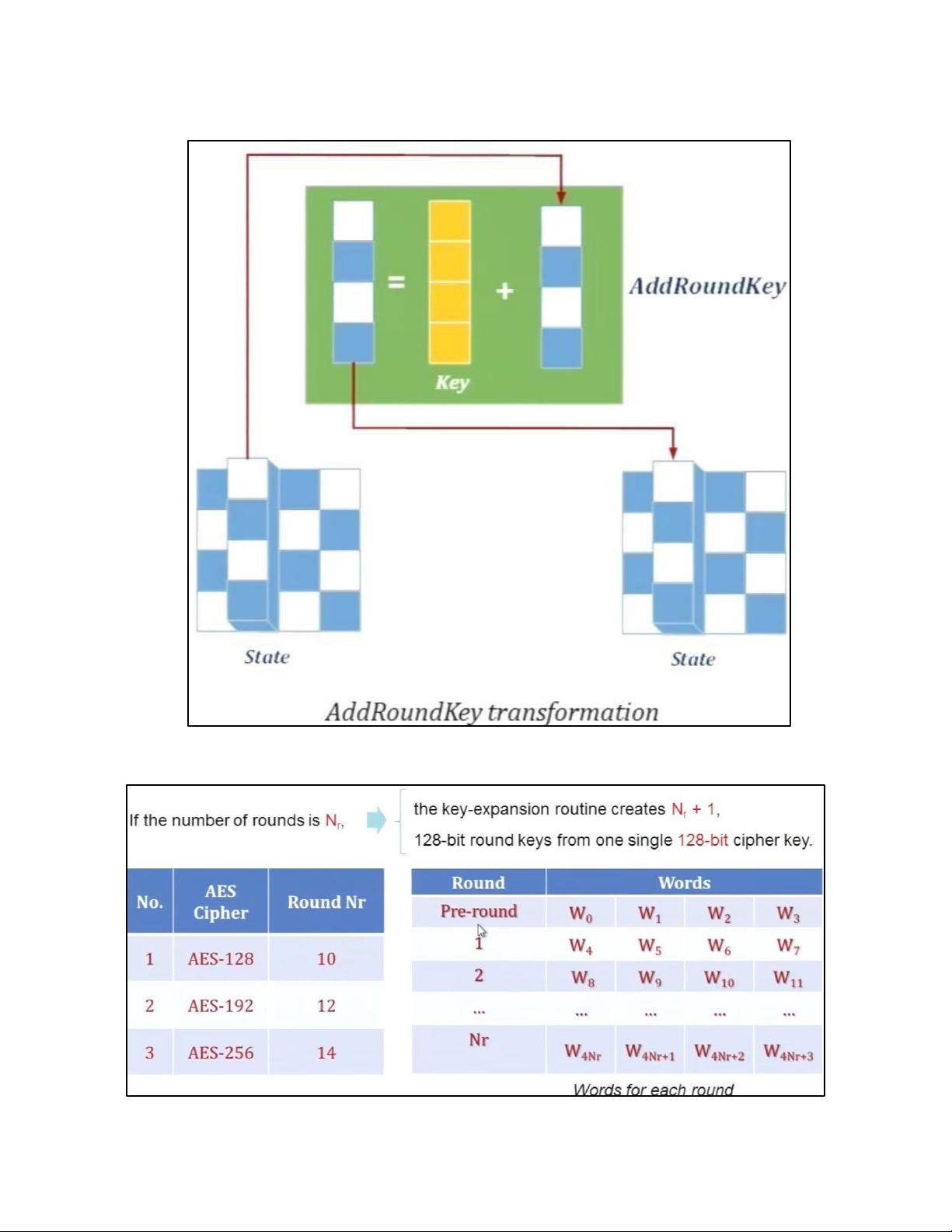
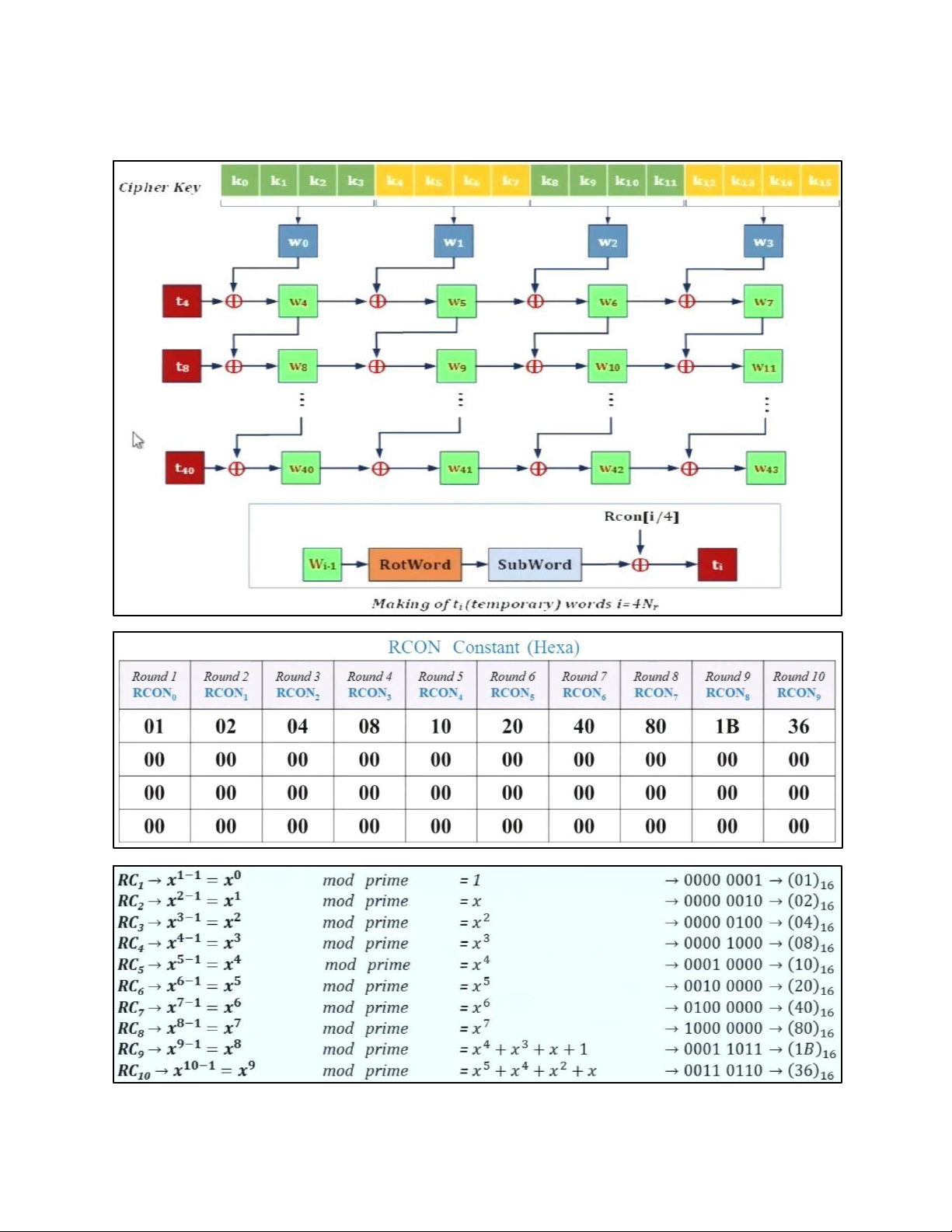
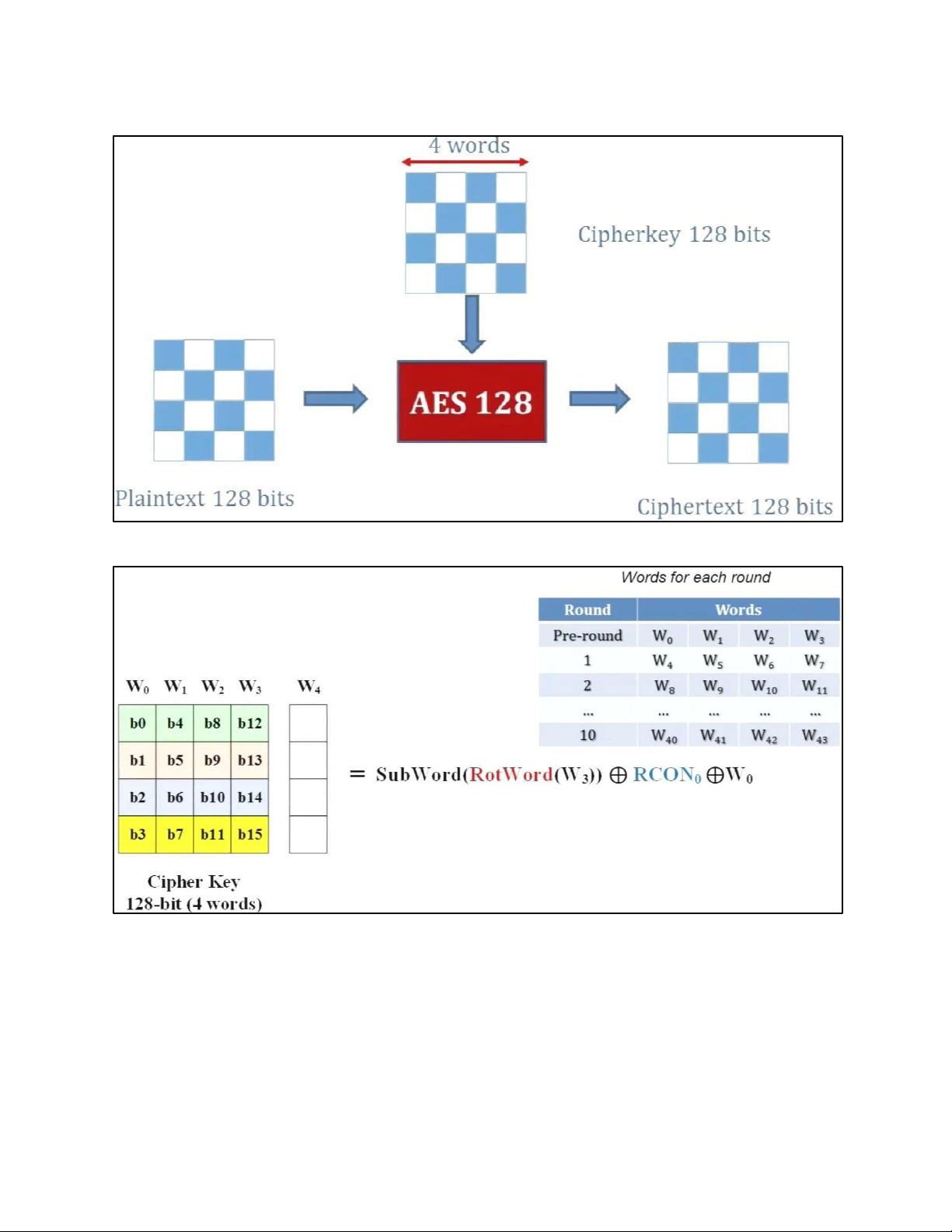
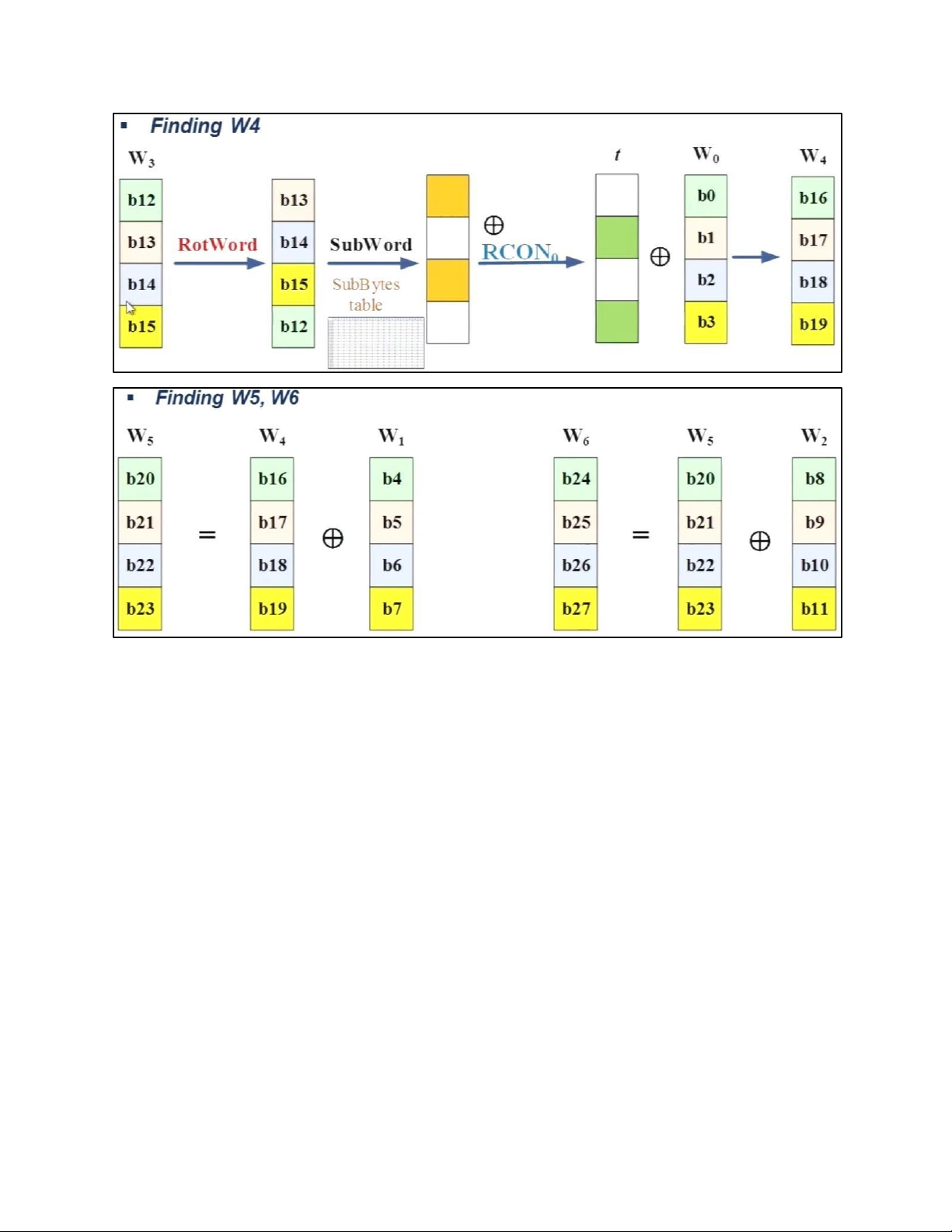
- TRANSFORMATION USING GF (28) • PERMUTATION - SHIFTROWS • MIXING • KEY – ADDING c. KEY EXPANSION KEY EXPANSION IN AES 128 5.2 . AES CIPHER DESIGN a. ORIGINAL DESIGN b. ALTERNATIVE DESIGN
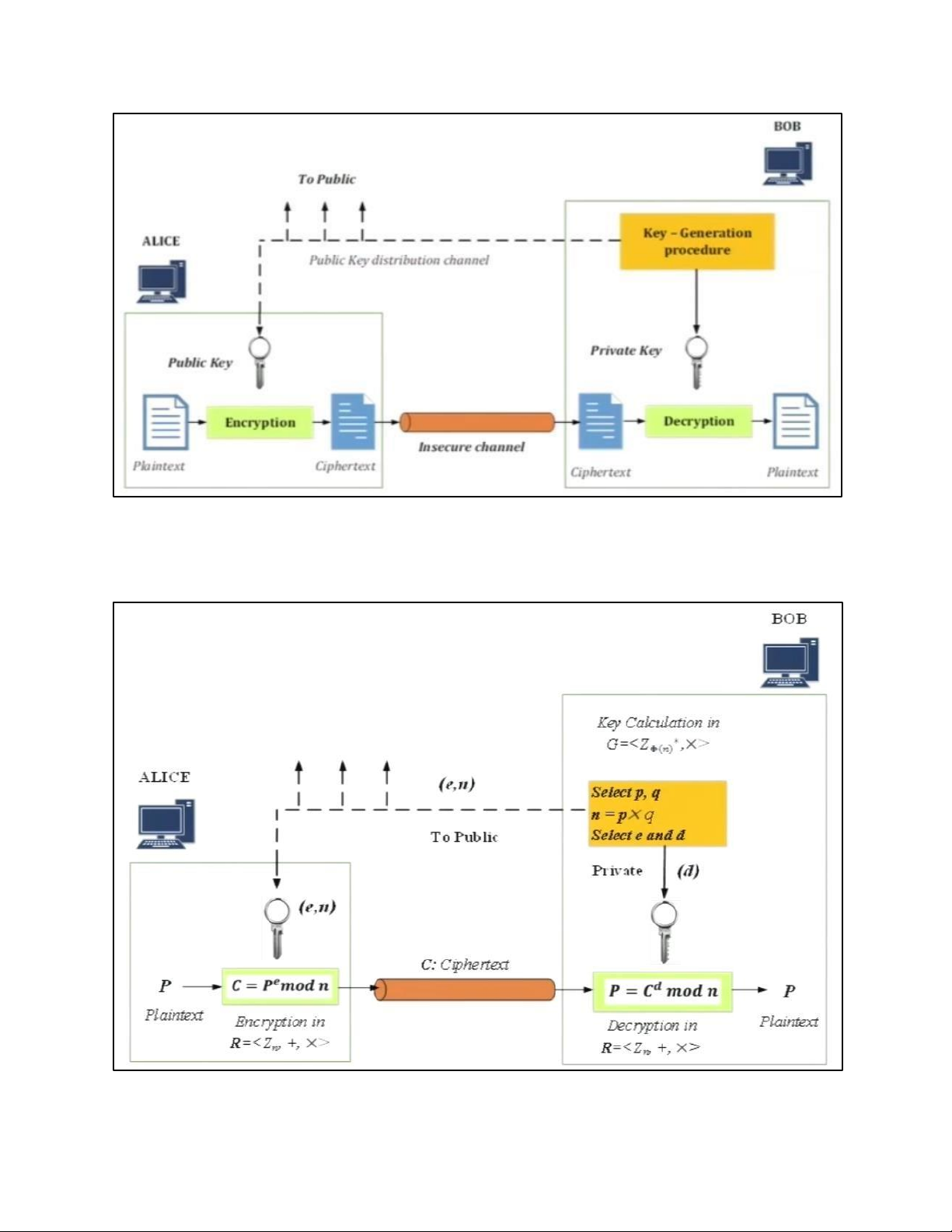
6. INTRODUCTION TO PUBLIC KEY CRYPTOGRAPHY 6.1. PUBLIC KEY a. SYSTEM STRUCTURE
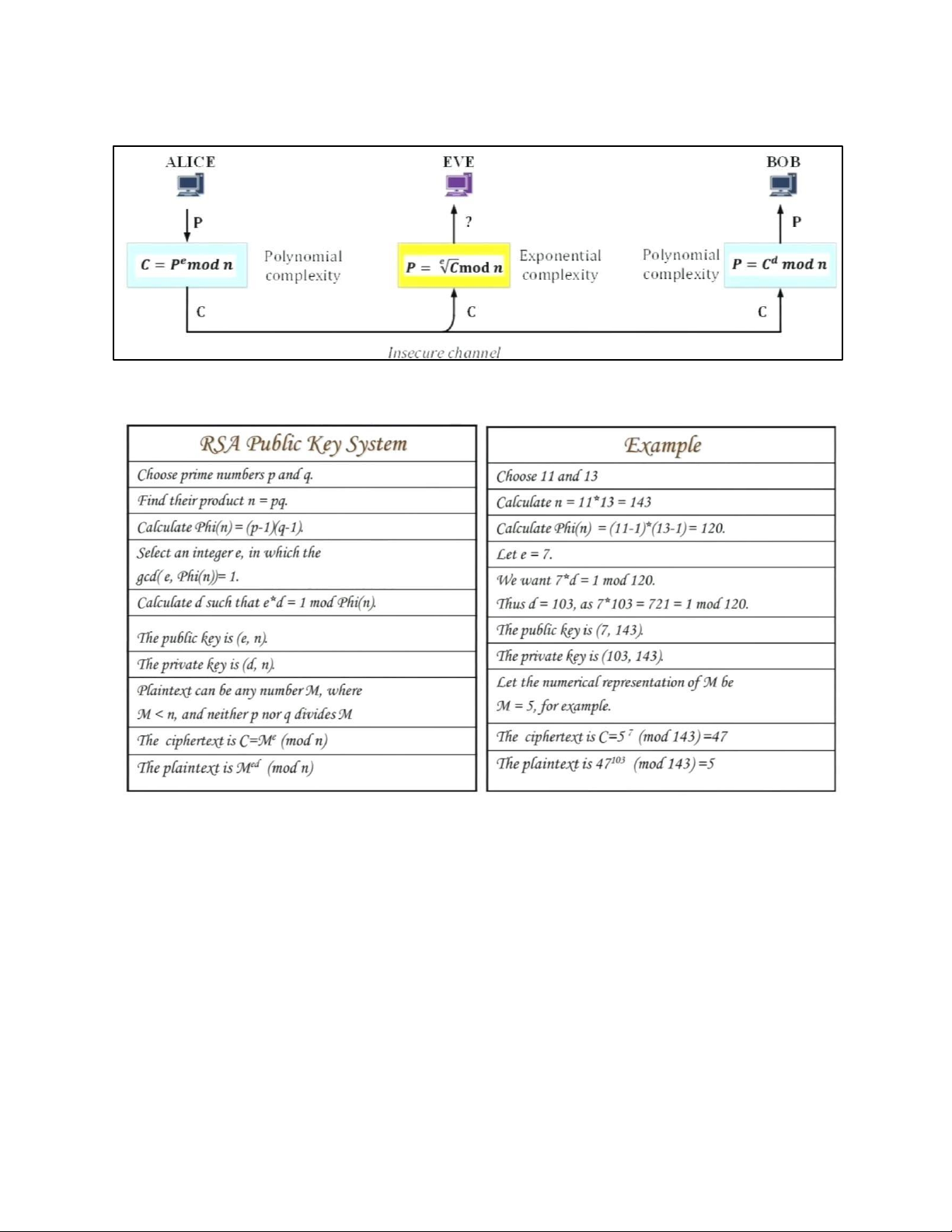
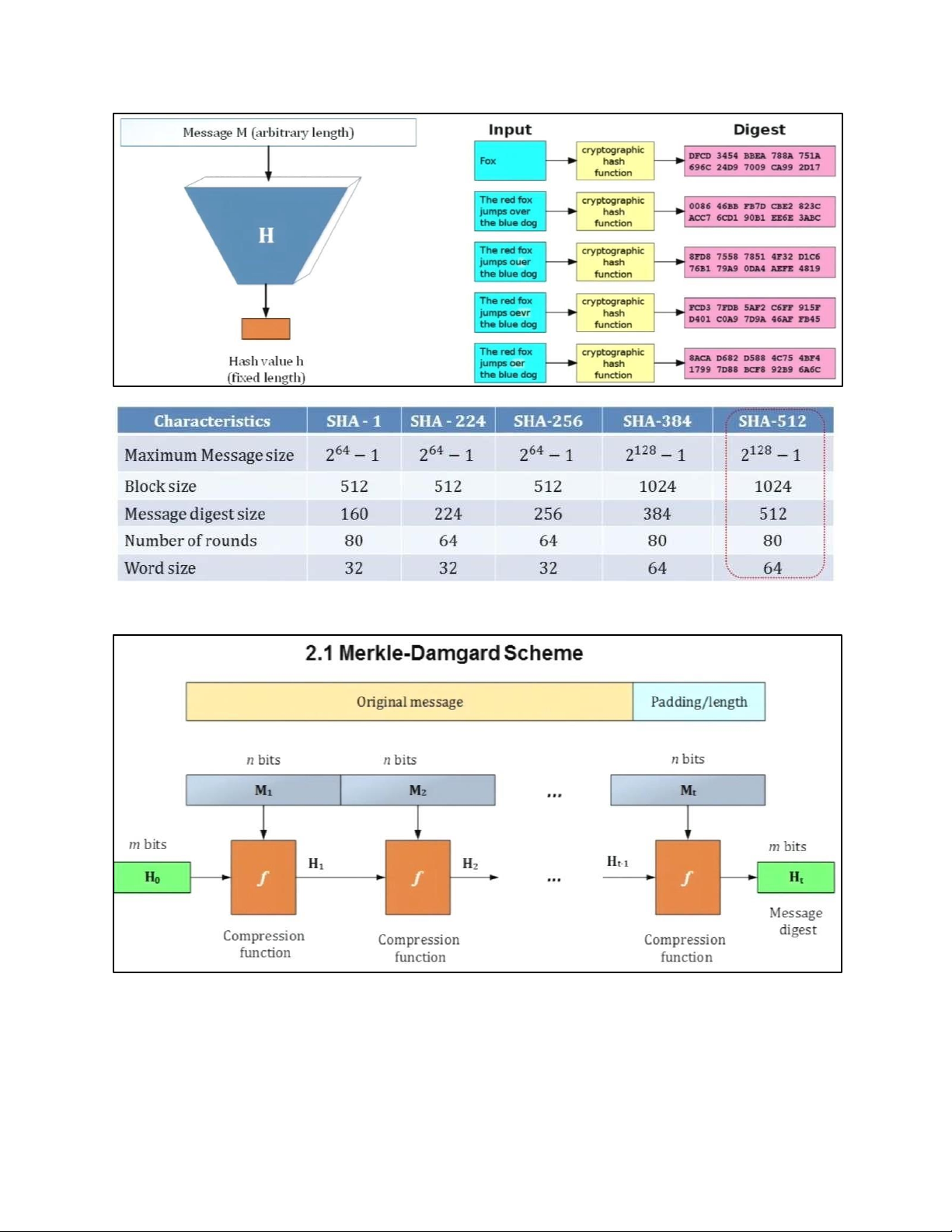
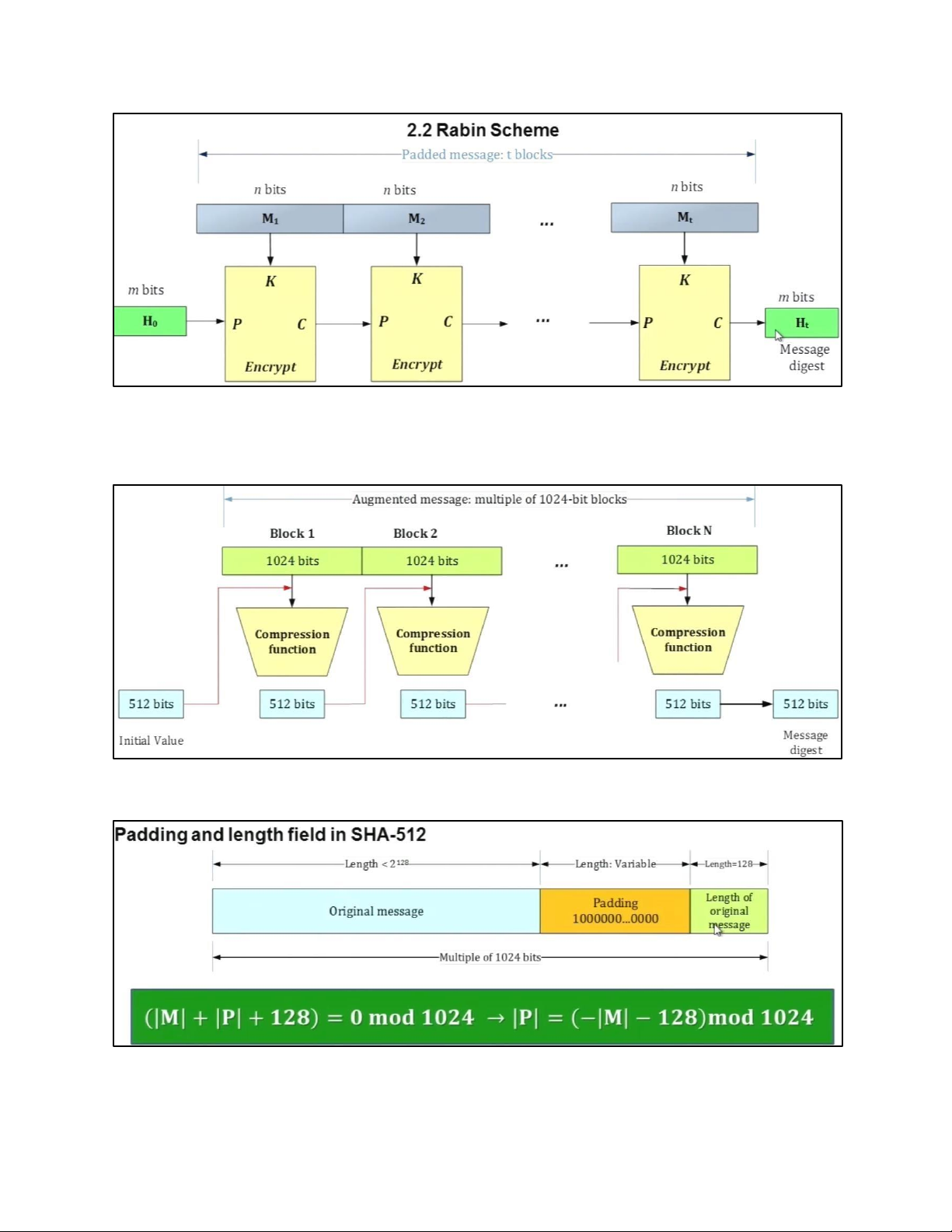
7 . RSA CRYPTOGRAPHY 7.1. SYSTEM MODEL 7.2. RSA CRYPTOGRAPHY 7.3 . SUMMARIZED EXAMPLE 8. HASH FUNCTION 8.1. INTRODUCTION 8.2. HASH FUNCTION SCHEME 8.3 . SHA-512 a. ALGORITHM STRUCTURE b. PRINCIPLE