


Preview text:
BỘ GIÁO DỤC VÀ ĐÀO TẠO
TRƯỜNG ĐẠI HỌC SƯ PHẠM KỸ THUẬT TP.HCM
KHOA CÔNG NGHỆ THÔNG TIN
BỘ MÔN AN TOÀN THÔNG TIN
BÁO CÁO BÀI THỰC HÀNH LAB 01: OS security
MÃ MÔN HỌC: INSE330380
THỰC HIỆN: Trần Nguyễn Phương Tây MSSV: 21110641
GI 䄃 NG VIÊN HƯỚNG DẪN: TS. Hu 礃 nh Nguyên Ch 椃Ānh
Tp. Hồ Ch 椃Ā Minh, tháng 09 năm 2022 Lab overview
In this lab, we will explore the use of the powerful network scanning tool, Nmap, to detect the
operating system, services, and vulnerabilities on a target machine. Lab task
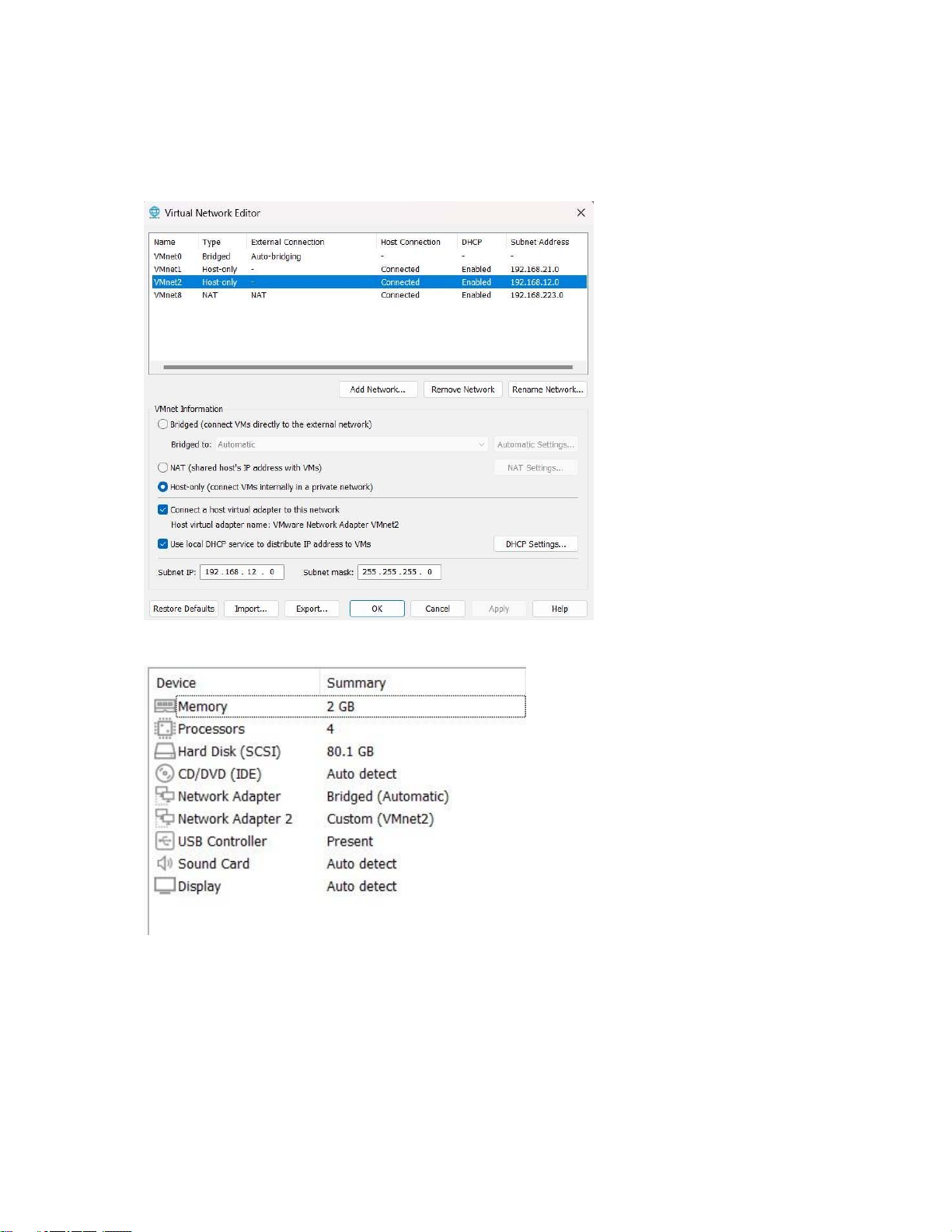
Connection between two machines - Create virtual network card:
- Attach the card to the 1st virtual machine:
- Attach the card to the 2nd virtual machine:
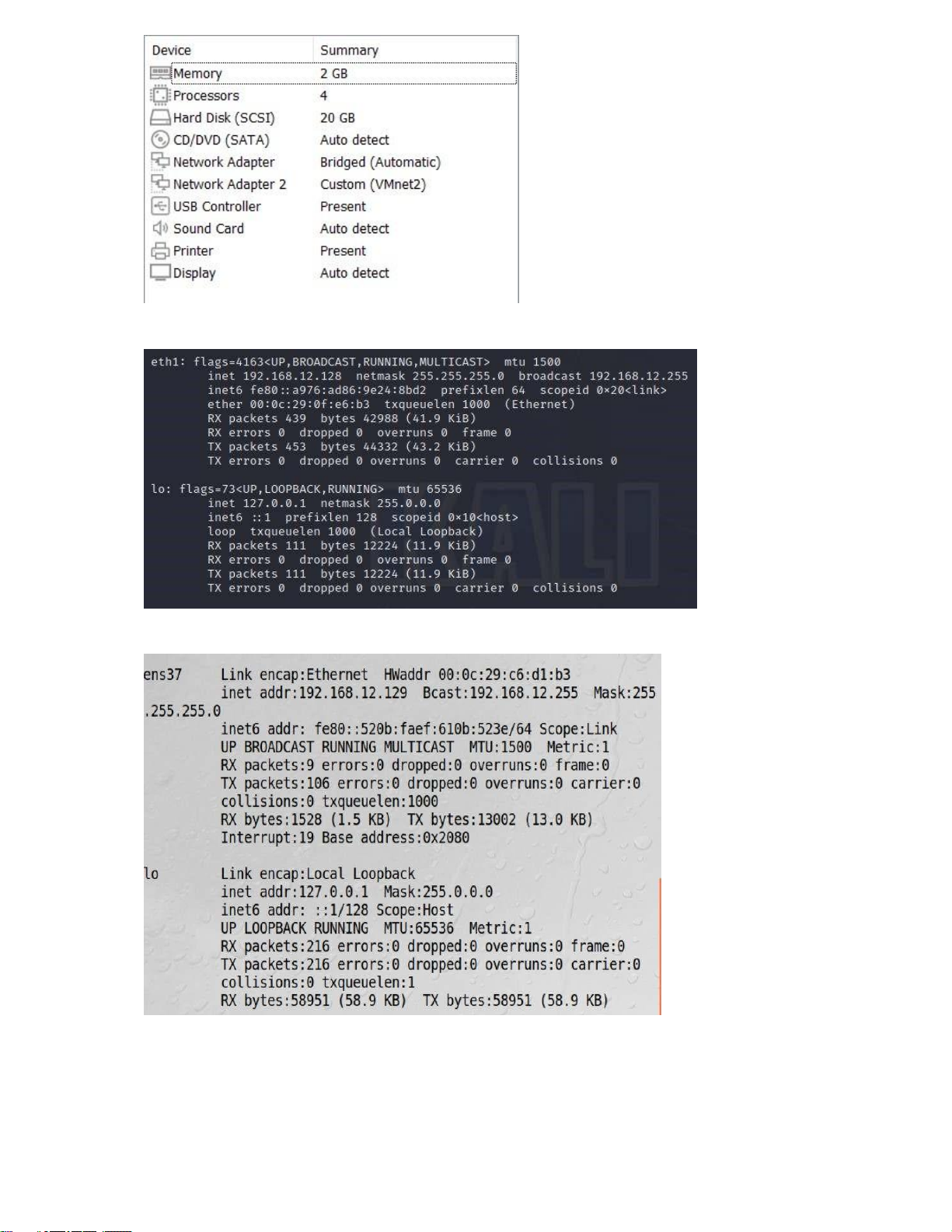
- IP configuration information of the 1st machine:
- IP configuration information of the 2nd machine:
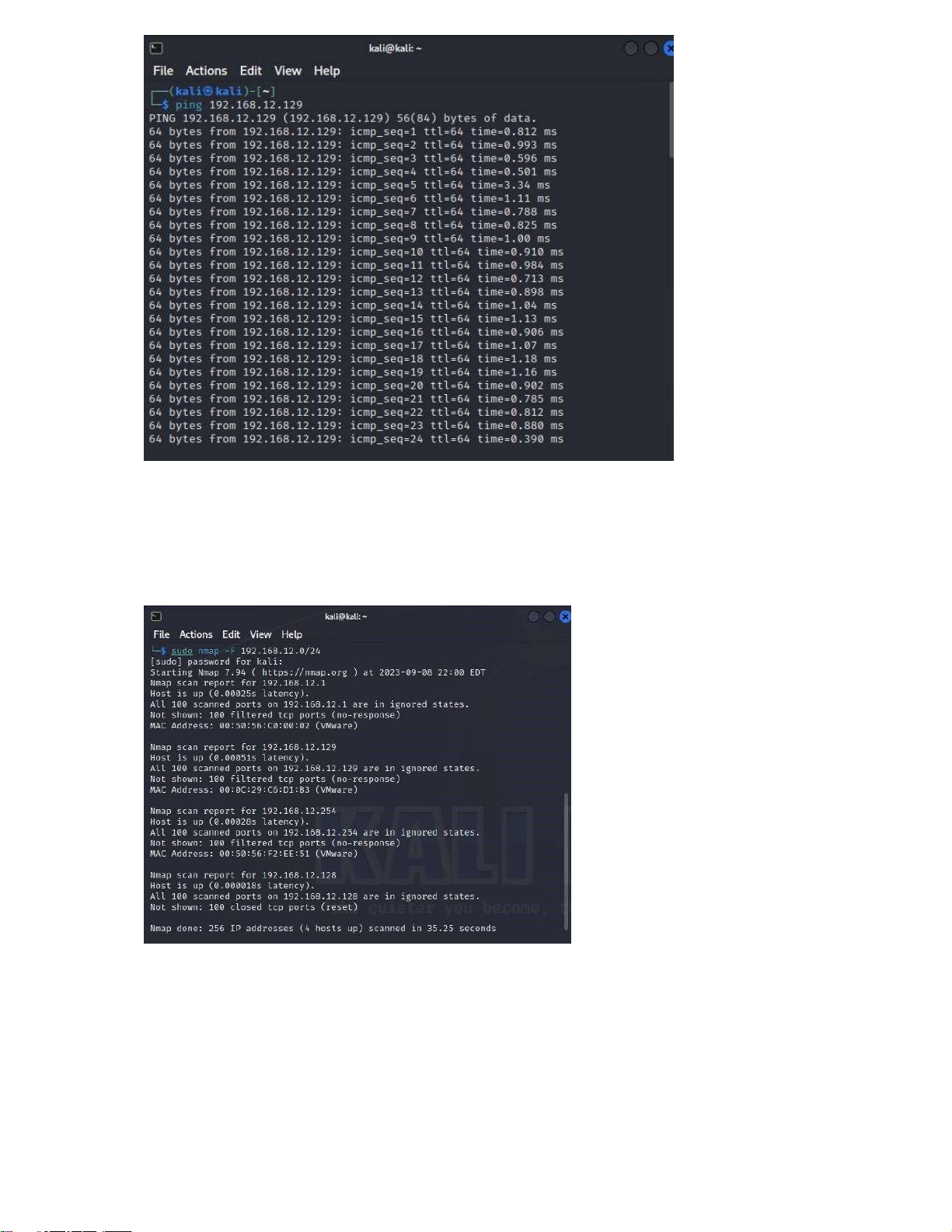
- Successful connection between 2 machines:
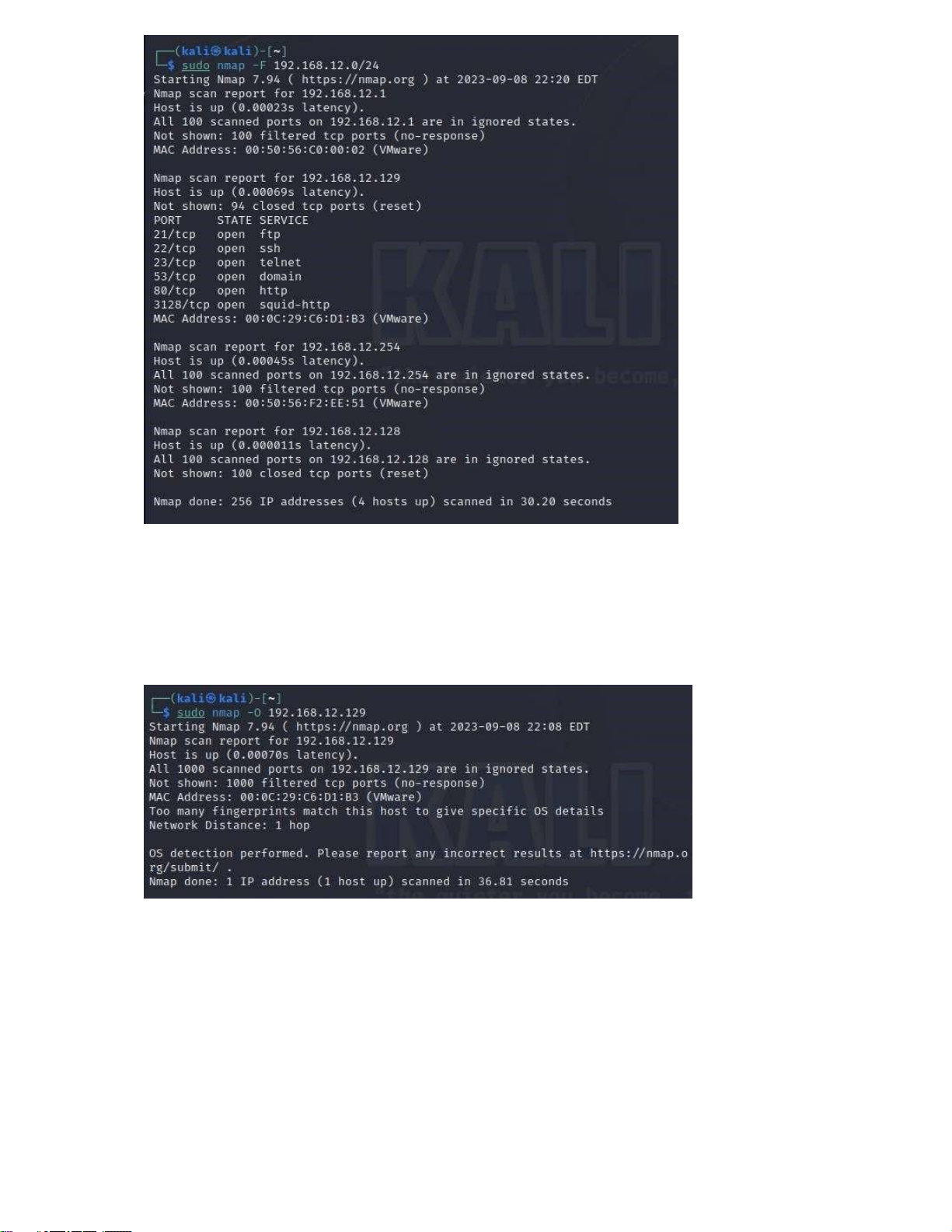
1. Using nmap to scan a machine (via IP address or name) to detect an
OS & services sudo nmap -F 192.168.12.0/24
This option specifies a type of quick scan, called a "Fast" or "Quick" scan. It will scan some
common ports instead of scanning all possible ports. - Turn on firewall:
Could not scan any port information - Turn off firewall:
Can scan out 6 ports on the machine 192.168.12.129
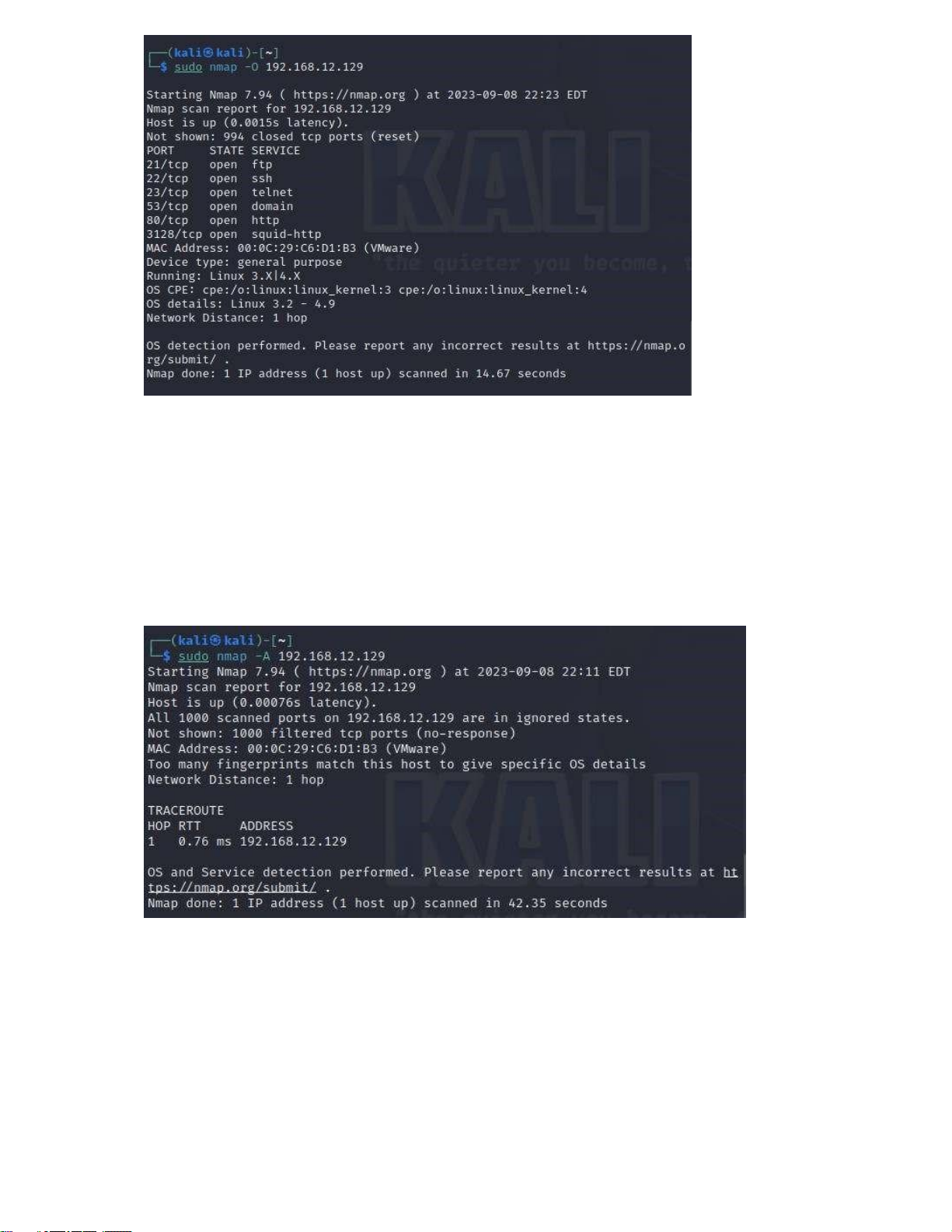
sudo nmap -O 192.168.12.129
Nmap will send network packets to the computer with IP address 192.168.12.129 and analyze
the responses to try to determine that computer's operating system. The results will display
information about the identified operating system (if any) along with the services and network
ports the computer is running on. - Turn on firewall:
Could not scan any OS information - Turn off firewall:
Information about the target machine's operating system has been scanned: running, OS CPE, OS details.
sudo nmap -A 192.168.12.129
-A: This is an aggregate option in Nmap and is often called "Aggressive Scan" or "All-in-one.".
Nmap will perform a detailed scan using a variety of scan types and system analysis techniques
to provide a detailed output about the target computer. This includes identifying the operating
system, checking for open network ports, identifying running services, and even executing
scripts through discovered services. The results will include a lot of useful information for
security analysis and system testing. - Turn on firewall: Could not scan any information - Turn off firewall:
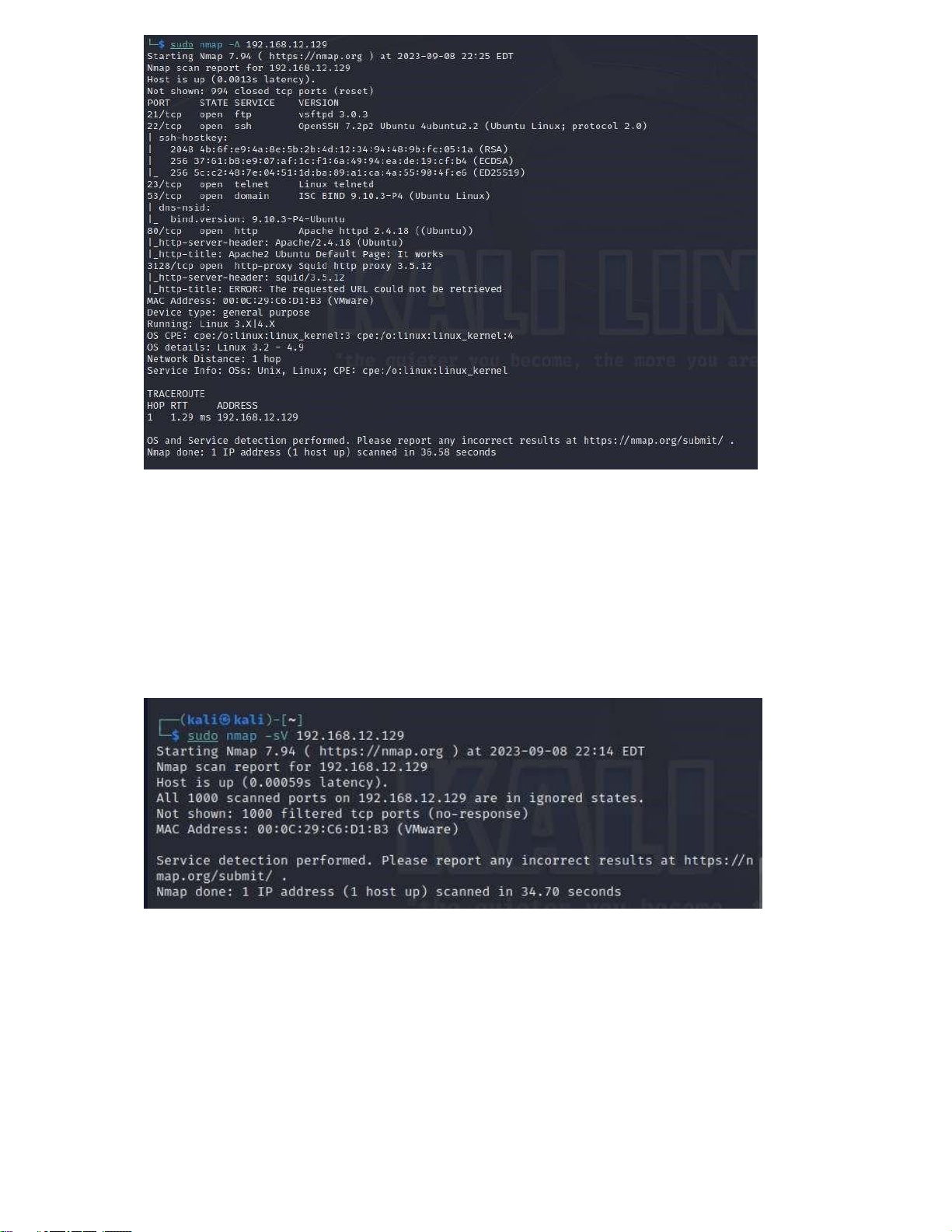
Scans out information about network ports, operating system and device information. This
result shows that the computer with IP address 192.168.12.129 runs Ubuntu Linux with many
services such as SSH, FTP, Telnet, DNS, HTTP, and HTTP Proxy.
sudo nmap -sV 192.168.12.129
Nmap will send requests to network ports on the computer with IP address 192.168.12.129 and
attempt to determine the versions of services running on those ports. The result will show a list
of network ports that have been scanned, information about the service (name and version) if
available, and network ports for which no service or version has been identified => overview
about the services running on the target computer and their versions. - Turn on firewall:
Could not scan any service version information - Turn off firewall:
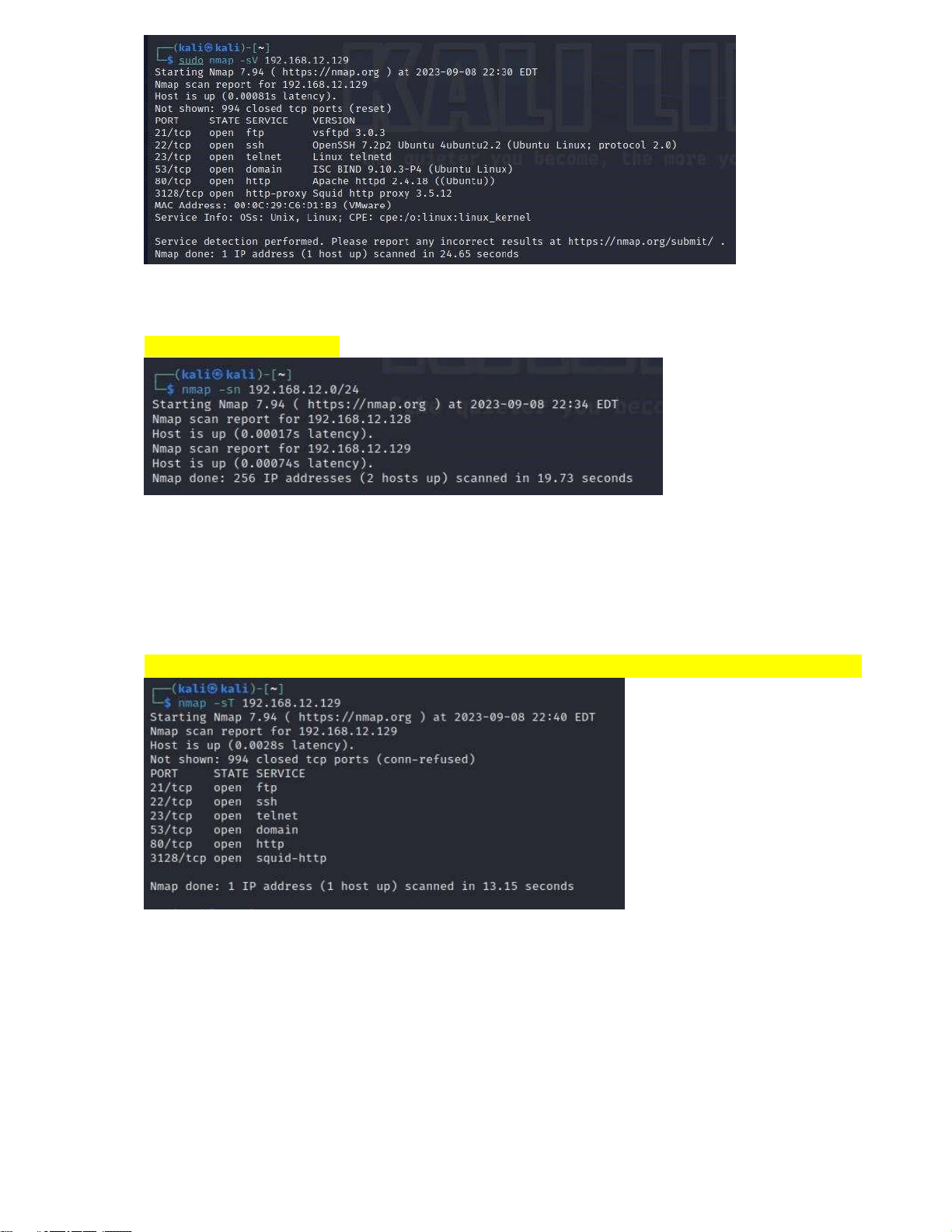
Scans out services running on ports and their versions. Some other options: nmap -sn 192.168.12.0/24
Command to identify active hosts. Scan results show a total of 2 hosts detected in the 192.168.12.0/24 subnet.
- IP address 192.168.12.128 was detected and determined to be "up" with a response time of 0.00017 seconds.
- IP address 192.168.12.129 was also detected and also identified as "up" with a response time of 0.00074 seconds. nmap -sT 192.168.12.129
The computer with IP address 192.168.12.129 is running various services on different network
ports such as FTP, SSH, Telnet, DNS, HTTP, and Squid HTTP Proxy. Scan results only show
opened network and service ports, not closed ports.
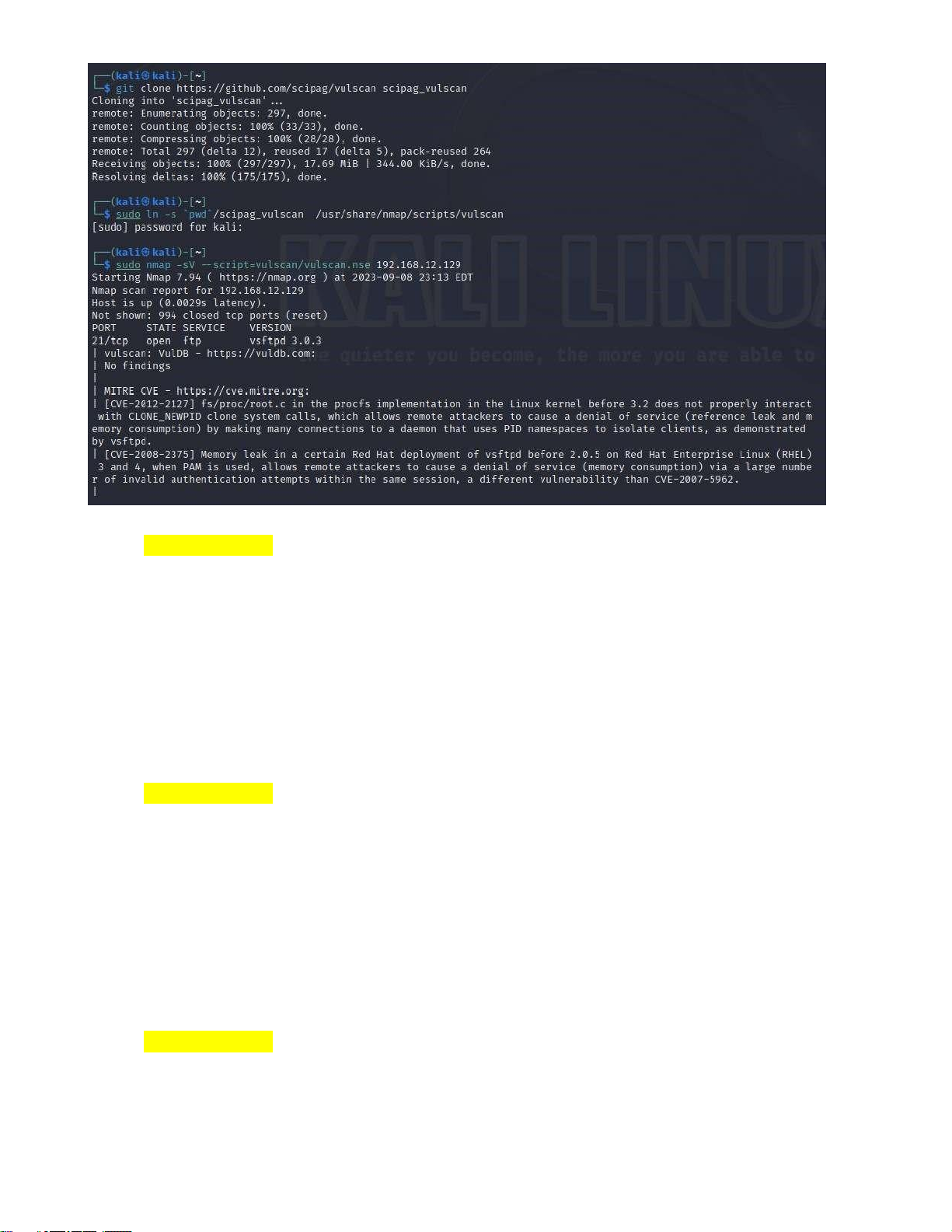
2. Using nmap with vul-scipt to detect vulnerabilities on an OS CVE-2010-3773:
Description: Mozilla Firefox before 3.5.16 and 3.6.x before 3.6.13, and SeaMonkey
before 2.0.11, when the XMLHttpRequestSpy module in the Firebug add-on is used, does not
properly handle interaction between the XMLHttpRequestSpy object and chrome privileged
objects, which allows remote attackers to execute arbitrary JavaScript via a crafted HTTP
response. NOTE: this vulnerability exists because of an incomplete fix for CVE-2010-0179.
Summary: This vulnerability allows remote attackers to initiate remote processes, read
arbitrary local files, and establish network connections through vectors related to the refresh
value in the http-equiv attribute of a META element, leading to the misuse of security principles. CVE-2010-1197:
Description: Mozilla Firefox 3.5.x before 3.5.10 and 3.6.x before 3.6.4, and
SeaMonkey before 2.0.5, does not properly handle situations in which both
"ContentDisposition: attachment" and "Content-Type: multipart" are present in HTTP headers,
which allows remote attackers to conduct cross-site scripting (XSS) attacks via an uploaded HTML document.
Summary: This vulnerability occurs when using the XMLHttpRequestSpy module in
the Firebug utility and mishandles interactions between the XMLHttpRequestSpy object and
objects with chrome privileges. This allows remote attacks to execute arbitrary JavaScript code
through HTTP responses, creating an opportunity for exploitation. CVE-2010-3775:
Description: Mozilla Firefox before 3.5.16 and 3.6.x before 3.6.13, and SeaMonkey
before 2.0.11, does not properly handle certain redirections involving data: URLs and Java
LiveConnect scripts, which allows remote attackers to start processes, read arbitrary local files,
and establish network connections via vectors involving a refresh value in the http-equiv
attribute of a META element, which causes the wrong security principal to be used.
Summary: A concise summary of the vulnerability, particularly highlighting the
impacts and consequences it may have on the affected system or application. CVE-2002-2246:
Description: Cross-site scripting (XSS) vulnerability in VisNetic Website before 3.5.15
allows remote attackers to inject arbitrary web script or HTML via the HTTP referer header
(HTTP_REFERER) to a non-existent page, which is injected into the resulting 404 error page.
Summary: This vulnerability allows remote attackers to inject arbitrary web or HTML
script via the HTTP_REFERER header. CVE-2002-2241:
Description: Buffer overflow in httpd32.exe in Deerfield VisNetic WebSite before
3.5.15 allows remote attackers to cause a denial of service (crash) via a long HTTP OPTIONS
request.Summary:Thisvulnerabilityallowsremote attackstocause a service crash. Summary
In this laboratory session, we immersed ourselves in the realm of operating system security,
with our focal point being the utilization of the Nmap tool for the thorough examination of a target
machine. Our primary objectives encompassed comprehending the methodologies employed in security
assessments and the discernment of potential system vulnerabilities. The ensuing key points
encapsulate the essence of our laboratory experience: -
Initial Scan: The inception of our laboratory endeavor involved the execution of a swift
scan on the target machine through the deployment of Nmap's -F flag. This expedited scan facilitated
the swift identification of commonly open ports and services. -
Operating System Detection: We harnessed Nmap's -O flag to discern the operating
system that was operational on the target machine. This pivotal step furnished us with invaluable
insights into the unique characteristics of the system. -
Thorough Service Scrutiny: A comprehensive service analysis was undertaken through
the application of the -sV flag. This exhaustive examination not only revealed the active services but
also unveiled their precise version numbers. This particular insight proved indispensable for the
evaluation of potential vulnerabilities. -
Firewall Evaluation: We embarked on an exploration of the firewall's influence on the
target machine by temporarily deactivating it and subsequently replicating the Nmap scans. This
comparative analysis shed illuminating light on the pivotal role played by firewalls in the realm of network security. -
Exploration of Supplementary Nmap Features: In our quest for a deeper comprehension,
we embarked on a journey of experimentation with supplementary Nmap options. This deliberate
exploration expanded our knowledge base and allowed us to amass a wealth of information concerning
the configuration of the target machine. -
Vulnerability Assessment: Our quest for insight led us to the installation and execution
of the vulscan Nmap script. This process unearthed latent vulnerabilities within the target machine,
effectively underscoring the critical role played by vulnerability assessments within the realm of security practices. -
CVE Vulnerability Analysis: A judicious selection of approximately five vulnerabilities
from the scan results, each adorned with a CVE identifier, was followed by in-depth research
endeavors. Our goal was to unravel the potential consequences and exploitation methodologies
associated with these identified vulnerabilities. -
Lab Report: Finally, our efforts culminated in the meticulous compilation of a
comprehensive laboratory report. This report encompassed an introductory section, an elaborate
breakdown of our procedural steps, recorded observations, a meticulous analysis of the detected
vulnerabilities, and a succinct conclusion. This report served as a document of our findings and the
insights garnered during the course of the laboratory exercise.
Upon the successful completion of this laboratory undertaking, we have acquired tangible
practical experience in the domains of network scanning, vulnerability identification, and the
paramount importance of safeguarding operating systems and services. Furthermore, we have refined
our abilities in the assessment and enhancement of computer system security. This knowledge is
indeed invaluable for individuals venturing into the captivating realms of cybersecurity and network administration. Reference
Security Trails. (2023, 09). Nmap Vulnerability Scan: A Comprehensive Guide. Retrieved from
https://securitytrails.com/blog/nmap-vulnerability-scan.
Document Outline
- Lab overview
- Lab task
- 1.Using nmap to scan a machine (via IP address or na
- sudo nmap -O 192.168.12.129
- sudo nmap -A 192.168.12.129
- sudo nmap -sV 192.168.12.129
- 2.Using nmap with vul-scipt to detect vulnerabilitie
- Summary
- Reference




