

Preview text:
21/11/2019
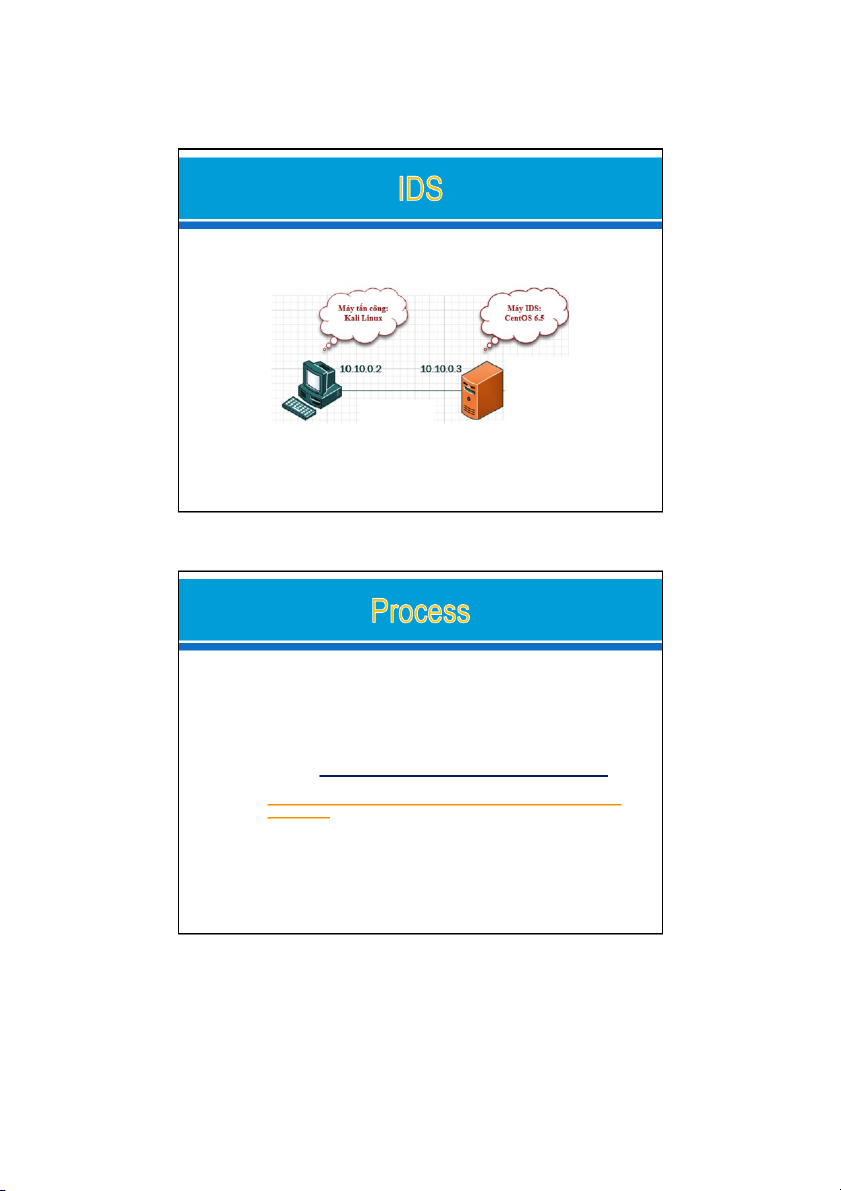
Lecturer: Nguyễn Thị Thanh Vân – FIT - HCMUTE ø Set up an IDS using: o Snort
ø Simulate attacks and use IDS above to detect o Ping o DDOS 21/11/2019 2 1 21/11/2019 21/11/2019 3 ø Set up IDS with Snort o Download and install Snort
o Database: MySQL – install, create, GRANT…. o Graphic Interface for Snort: • Web server, PHP • pear
• ADODB: http://nchc.dl.sourceforge.net/sourceforge/adodb/ • BASE:
http://nchc.dl.sourceforge.net/sourceforge/secureideas/base- 1.4.2.tar.gz
ø Set up attacker machine (DOS, Brute Force) o Ping: ping o DDOS: hping3 21/11/2019 4 2 21/11/2019 $ nano /etc/snort/snort.conf ipvar HOME_NET ipvar EXTERNAL_NET !$HOME_NET var RULE_PATH /etc/snort/rules
var SO_RULE_PATH /etc/snort/so_rules
var PREPROC_RULE_PATH /etc/snort/preproc_rules
var WHITE_LIST_PATH /etc/snort/rules
var BLACK_LIST_PATH /etc/snort/rules 21/11/2019 5
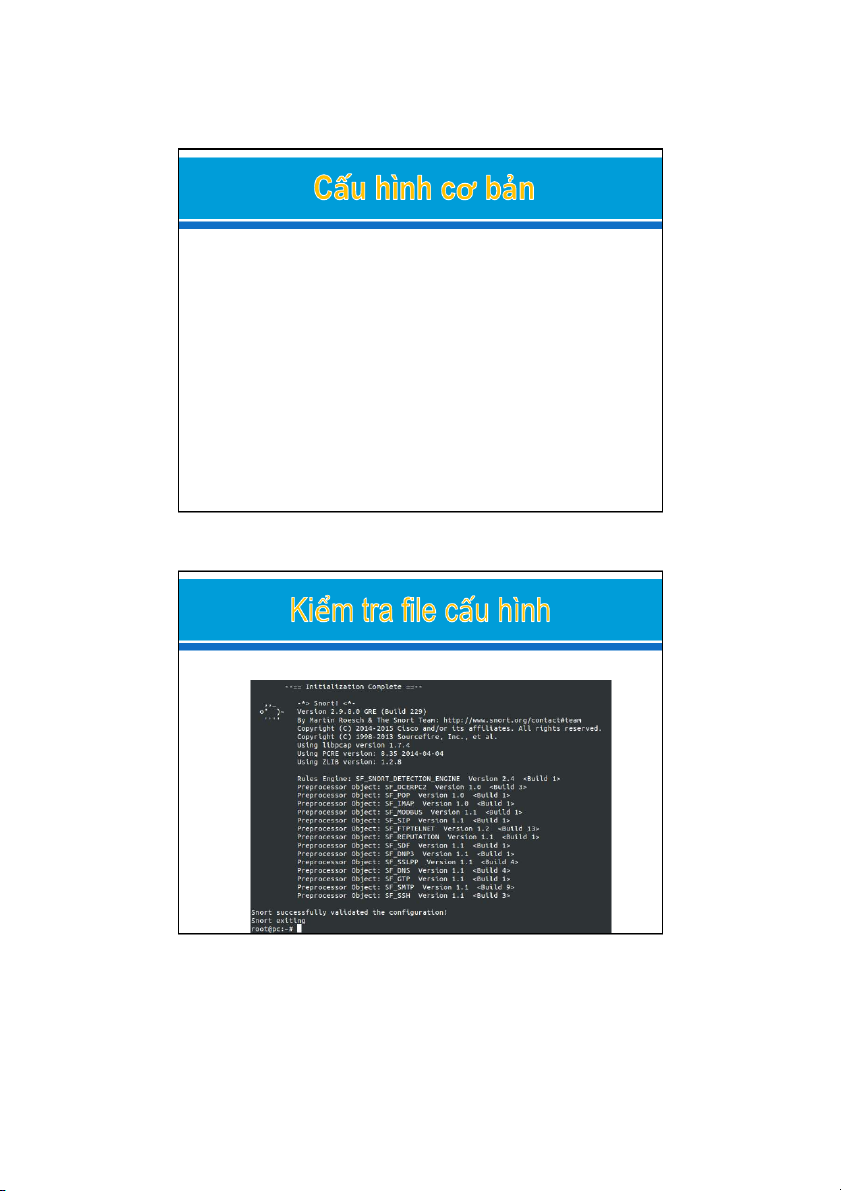
$ snort -T -c /etc/snort/snort.conf 21/11/2019 6 3 21/11/2019
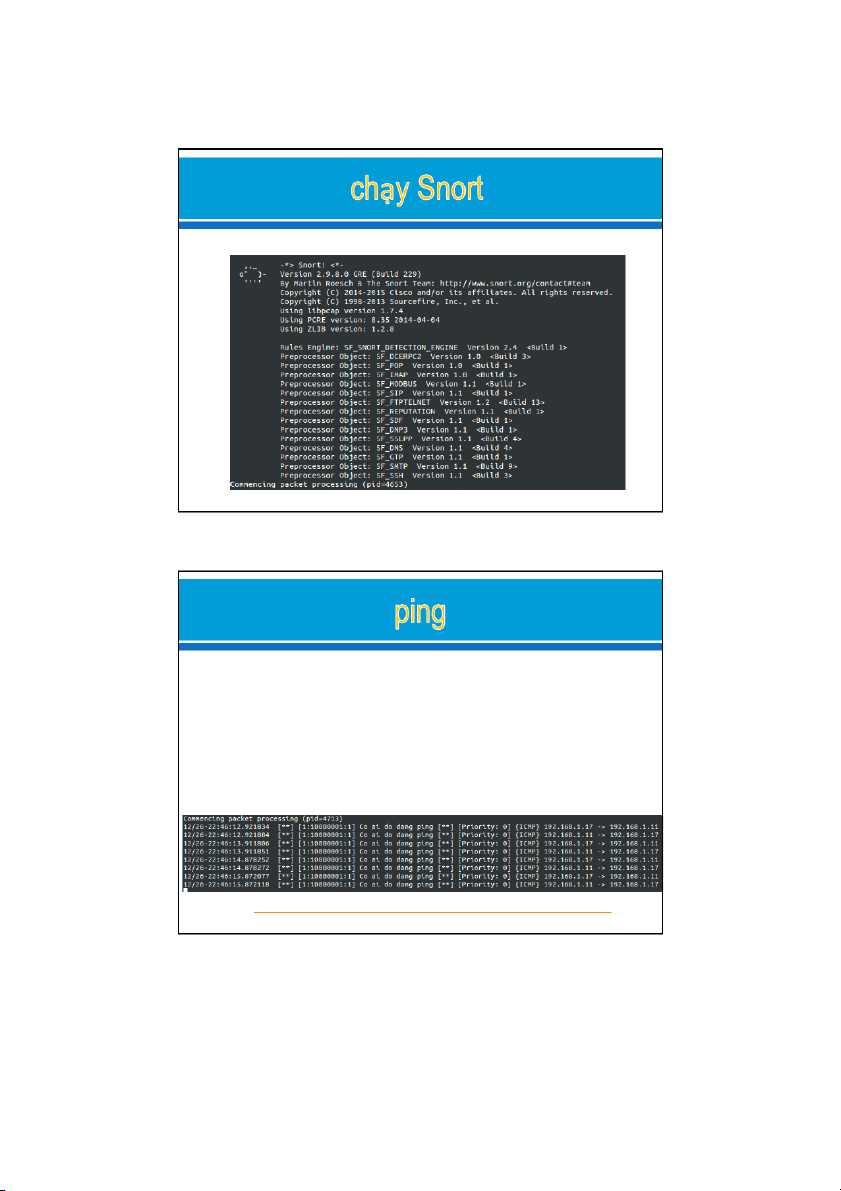
$ /usr/local/bin/snort -A console -c /etc/snort/snort.conf -i eth0 21/11/2019 7 ø Create rule icmp – ping:
$ nano /etc/snort/rules/icmp.rules
alert icmp any any -> $HOME_NET any (msg:"Co ai do dang ping"; sid:10000001; rev:001;) ø Add rule path in snort.conf $ nano /etc/snort/snort.conf include $RULE_PATH/icmp.rules ø At attacker: ping ø At IDS:
ø Ref: https://adminvietnam.org/cai-dat-snort-ids-tren-ubuntu/1210/ 21/11/2019 8 4 21/11/2019 ø Create rule dos – hping3:
$ nano /etc/snort/rules/dos.rules. Ex:
alert tcp any -> $HOME_NET 80 (msg:"DDOS GET";content:"GET /
HTTP"; flow:to_server, established; threshold: type threshold,
track by_src, count 30, seconds 30; sid:1000004;) ø Add rule path in snort.conf $ nano /etc/snort/snort.conf include $RULE_PATH/dos.rules ø At attacker: hping3 …. ø At IDS: ……"DDOS GET" 21/11/2019 9 5




