

Preview text:
MÔN
: HỆ THỐNG THÔNG TIN KẾ TOÁN C5: PROBLEM:
11.4. Which preventive, detective, and/or corrective controls would best mitigate the following threats?
a. An employee’s laptop was stolen at the airport. The laptop contained
personally identifying information about the company’s customers that could
potentially be used to commit identity theft.
Preventive: Should have special methods for storing sensitive information on laptop
such as: encrypt sensitive information, require multifactor authentication to access the
laptop and the information, training staff how to protect laptops while traveling…
Corrective: Install a software which can recover and erase information remotely from
the company, by an authorized person.
b. A salesperson successfully logged into the payroll system by guessing the
payroll supervisor’s password.
Preventive: Should use multifactor authentication to access the information.
Password should be strong and changed frequently.
Detective: Locking out accounts after 3-5 unsuccessful login attempts, a warning sent
by email or phone to confirm that it is the supervisor that log in.
c. A criminal remotely accessed a sensitive database using the authentication
credentials (user ID and strong password) of an IT manager. At the time the
attack occurred, the IT manager was logged into the system at his
workstation at company headquarters.
Preventive: A warning sent by IT manager’s email or phone to confirm that someone
log in. The system should have function to reject that same user is already
logged in from a physical workstation.
Detective: Having the system notify appropriate security staff about such an incident.
d. An employee received an email purporting to be from her boss informing her
of an important new attendance policy. When she clicked on a link embedded
in the email to view the new policy, she infected her laptop with a keystroke logger.
Preventive: Train awareness of the employee to avoid those case.
Detective and corrective: An Anti-spyware software has to be installed to the
employee pc as a part of logon access. It can check and clean the spyware on
employee’s computer before the accident happens.
e. A company’s programming staff wrote custom code for the shopping cart
feature on its web site. The code contained a buffer overflow vulnerability
that could be exploited when the customer typed in the ship-to address.
Preventive: Teach programmers secure programming practices and management
must support the commitment to secure coding practices.
Detective: All programs are thoroughly tested before being put into use
Have a department routinely test new developed software.
f. A company purchased the leading “off-the-shelf” e-commerce software for
linking its electronic storefront to its inventory database. A customer
discovered a way to directly access the back-end database by entering appropriate SQL code.
Preventive: Thoroughly test the software prior and its security before purchase from 3rd party.
g. Attackers broke into the company’s information system through a wireless
access point located in one of its retail stores. The wireless access point had
been purchased and installed by the store manager without informing central IT or security.
Preventive: Have a policy that forbids installation of unauthorized wireless access points.
Detective: Routinely check for unauthorized or rogue wireless access points.
Corrective: Policy enactment to punish employees who install unauthorized wireless access points.
h. An employee picked up a USB drive in the parking lot and plugged it into
their laptop to “see what was on it,” which resulted in a keystroke logger
being installed on that laptop.
Preventive: Security awareness training. Teach employees to never insert USB
drives unless they are absolutely certain of their source.
Anti-spyware software that automatically checks and cleans all detected spyware
on an employee's computer as part of the logon process.
i. Once an attack on the company’s website was discovered, it took more than
30 minutes to determine who to contact to initiate response actions.
Preventive: Document all members of the security department and their contact information.
Practice the incident response plan.
j. To facilitate working from home, an employee installed a modem on his office
workstation. An attacker successfully penetrated the company’s system by dialing into that modem.
Preventive: Routinely check for unauthorized or rogue modems by dialing all
telephone numbers assigned to the company and identifying those connected to modems.
k. An attacker gained access to the company’s internal network by installing a
wireless access point in a wiring closet located next to the elevators on the
fourth floor of a high-rise office building that the company shared with seven other companies.
Preventive: Secure or lock all wiring closets.
Require strong authentication of all attempts to log into the system from a wireless client.
Employ an intrusion detection system. 12.1: 1e 2l 3b 4k 5f 6q 7h 8j 9m 10n 11s 12c 13r 14d 15p 16o 17a 13.1 1r 2i 3n 4t 5a 6u 7c 8h 9e 10j 11m 12l 13o 14q 15s 16v 17d 18p 19w 13.2 13.3 13.4
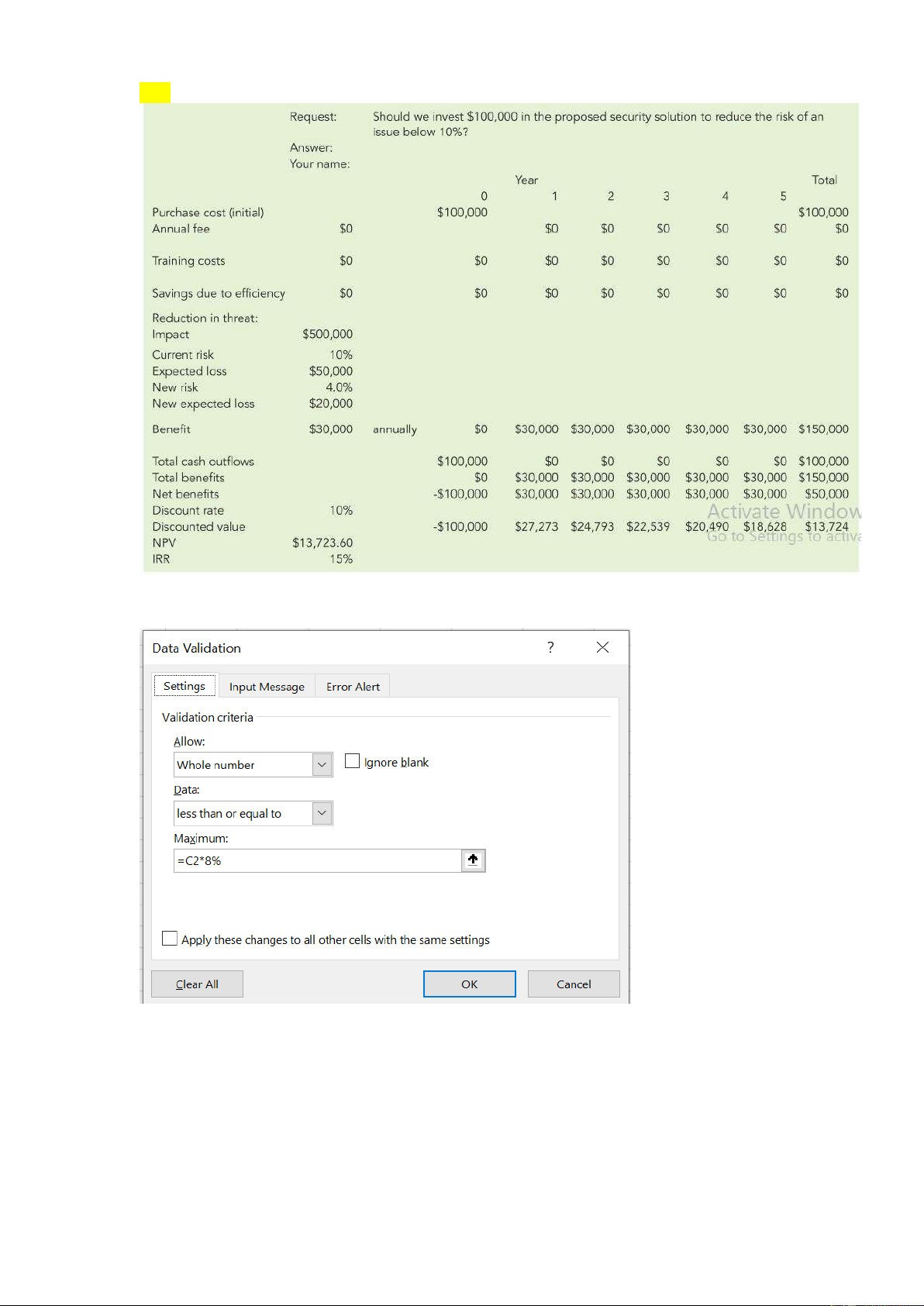
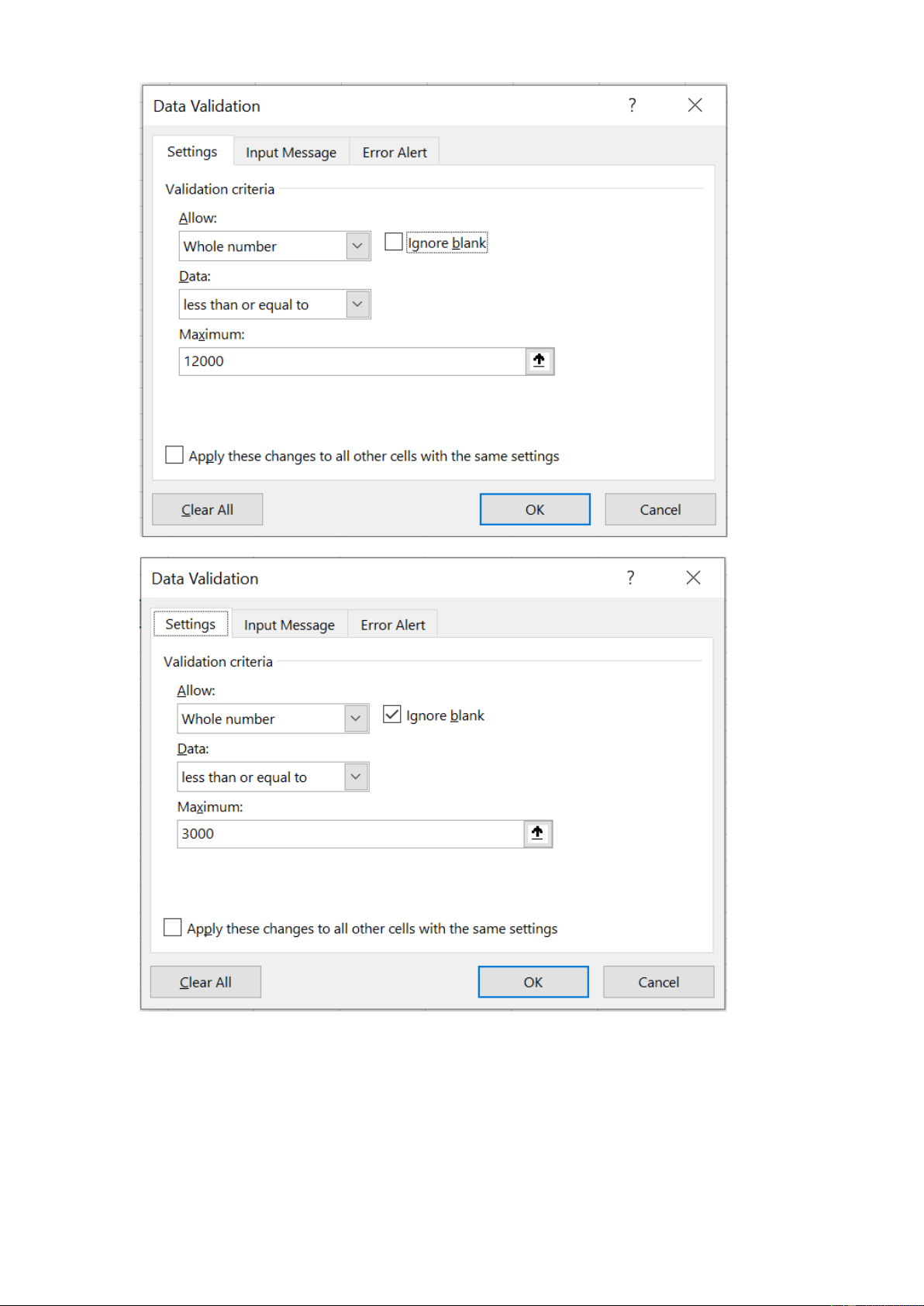
1. Annual fee cannot exceed 8% of purchase cost
2. Training costs cannot exceed $12,000 in year 0 and $3,000 thereafter Year 0 Year 1 -> Year 5
3. Savings due to efficiency cannot exceed $5000, but must be zero in year 0 Year 0 Year 1 -> Year 5
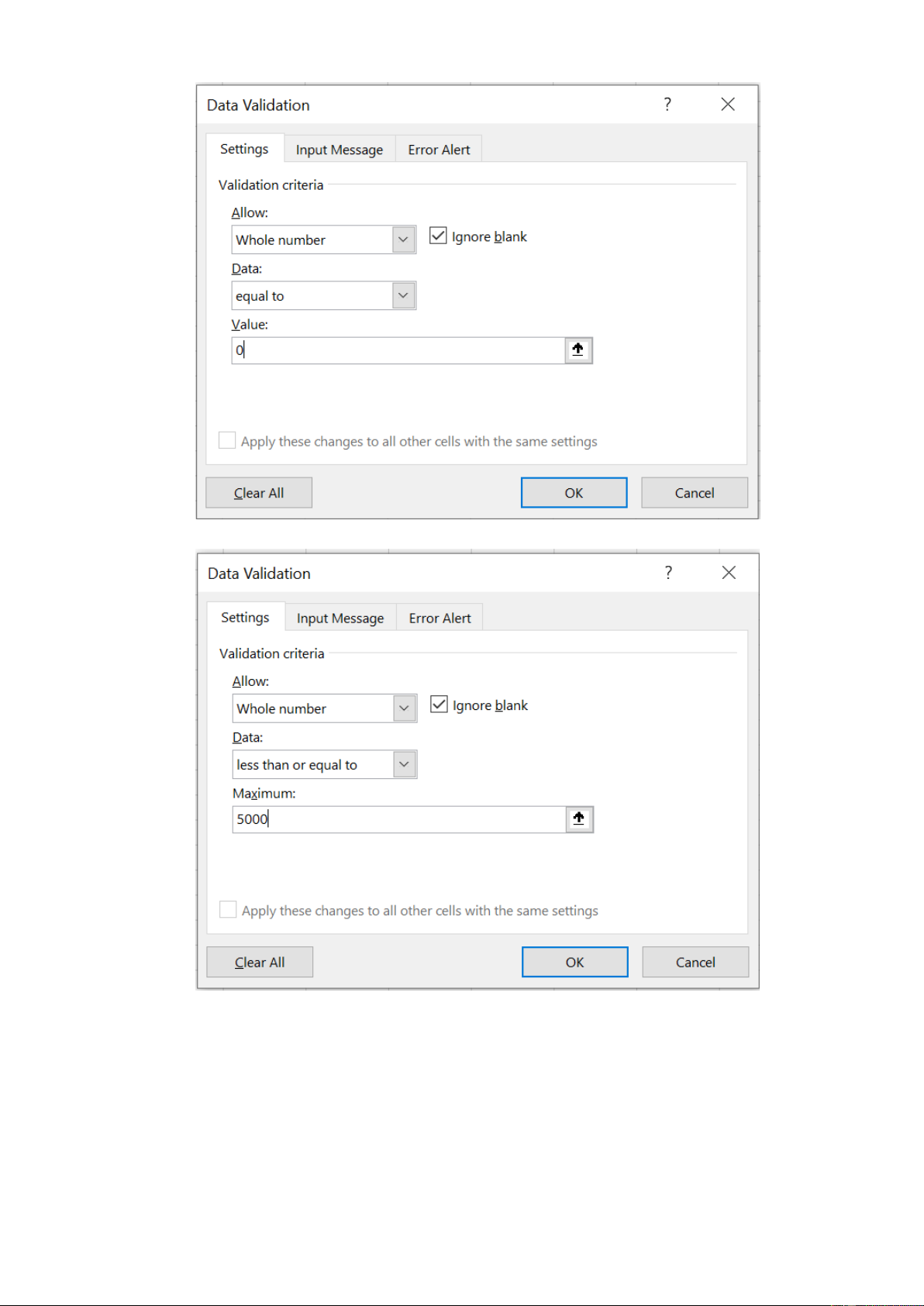
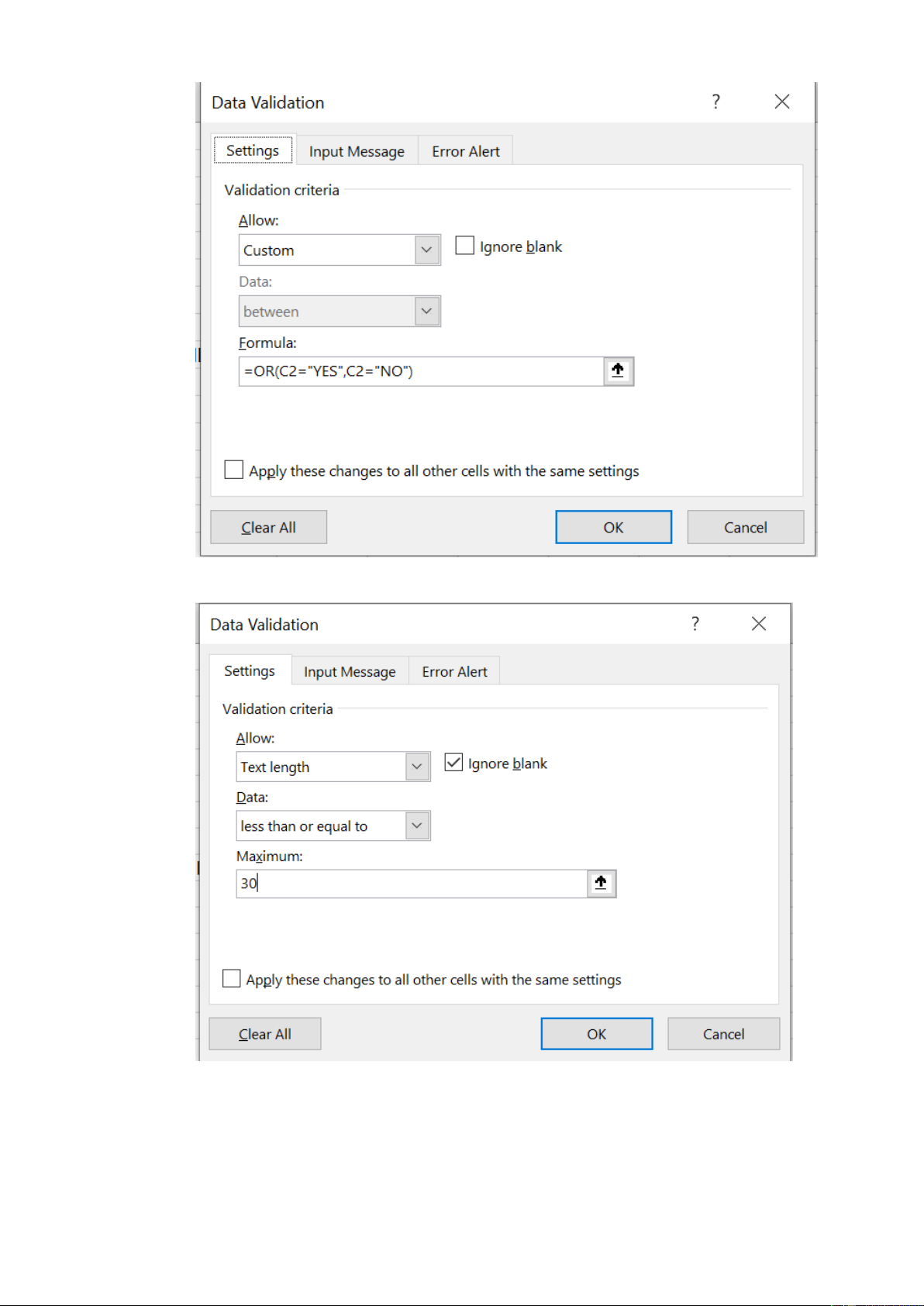
4. Cell C2 must force entry of either “YES” or “NO” – no other values can be accepted
5. Your name must appear in cell C3 and must not exceed 30 characters total
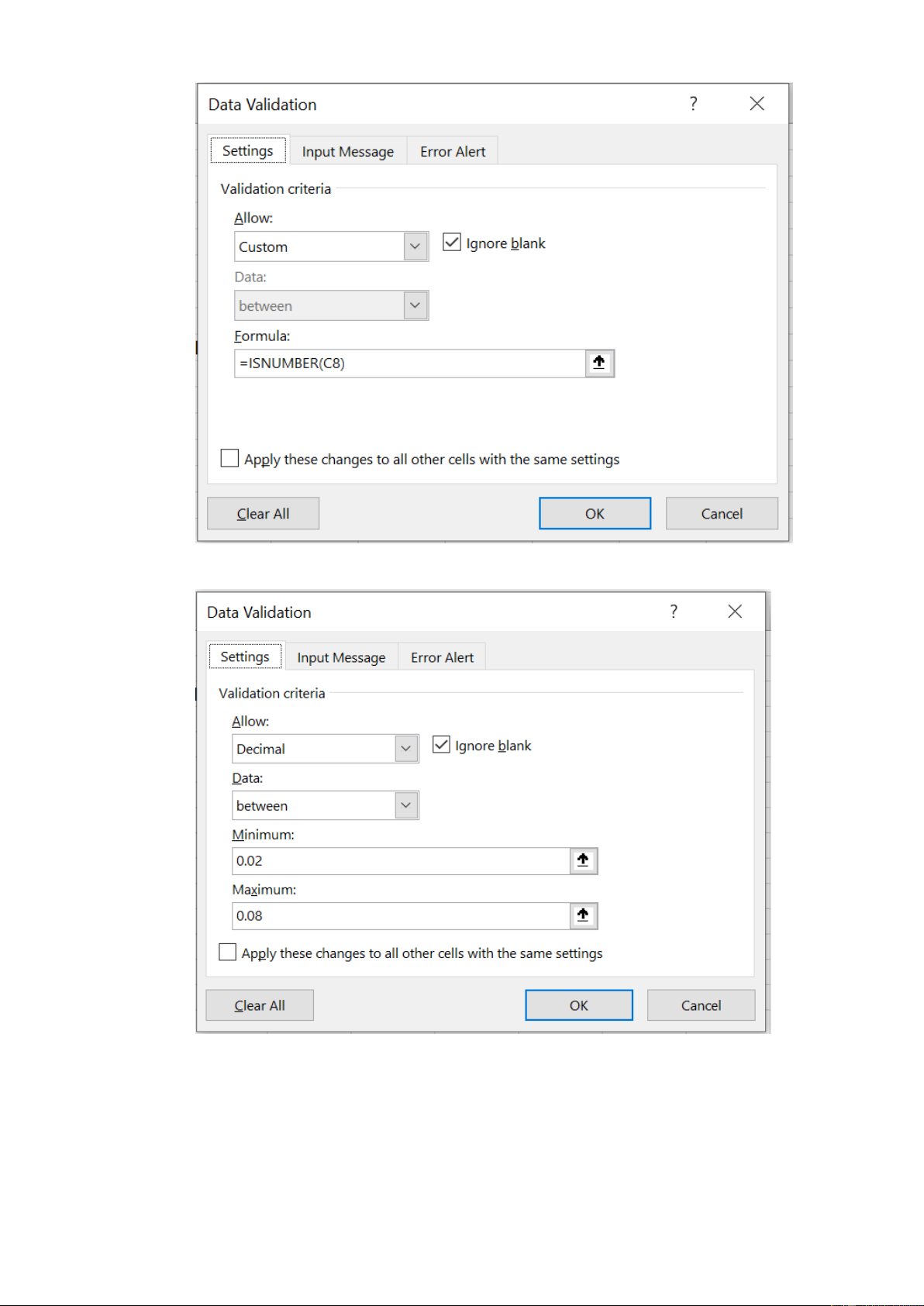
6. Cell B8 (annual fee) must NOT permit any alphabetic text
7. The reduction in risk due to the security investment (cell B18) must range between 2% and 8%, inclusive 13.7 13.8:
During a heavy storm, lightning struck an office building that houses the data
center of a small accounting firm. The lightning caused a fire that interrupted
the electricity supply to the building and damage some of the computer
hardware and office equipment. The fluctuation in the power supply caused the
file server to power down. All of these occurred while the backups were being
made, rendering the backup unusable. To save money, the company backups are
always made on the same storage media, reusing the same media every time a backup is made. Required
Identify at least five weaknesses in firm’s backup and DRP procedures.
1. No uninterruptible power source equipment to support computer equipment for Server.
2. Backups are not done on a regular basis.
3. Restoration of backups is not tested.
4. No offsite data backup/ No cloud backup
5. The location of the computing facility should be choose and have methods to
prevent the risk of damage due to power outage. 13.9
- Tất cả các quy tắc xác thực dữ liệu Excel, được tích hợp sẵn và tùy chỉnh,
chỉ xác minh dữ liệu mới được nhập vào một ô sau khi tạo quy tắc.
- Dữ liệu được sao chép không được xác thực, cũng không phải là dữ liệu
đầu vào trong ô trước khi thực hiện quy tắc.
- Để ghim các mục nhập hiện có không đáp ứng tiêu chí xác thực dữ liệu, sử
dụng tính năng Circle Invalid Data bên dưới mục Data Validation để tìm
dữ liệu không hợp lệ đã lọt vào trang tính trước khi thêm xác thực dữ liệu.





